5G Security Market by Component, Deployment Mode, Organization Size, End User, Network Component Security (RAN and Core Security), Architecture, Application, Vertical and Region - Global Forecast to 2027
Updated on : April 28, 2023
Market Overview
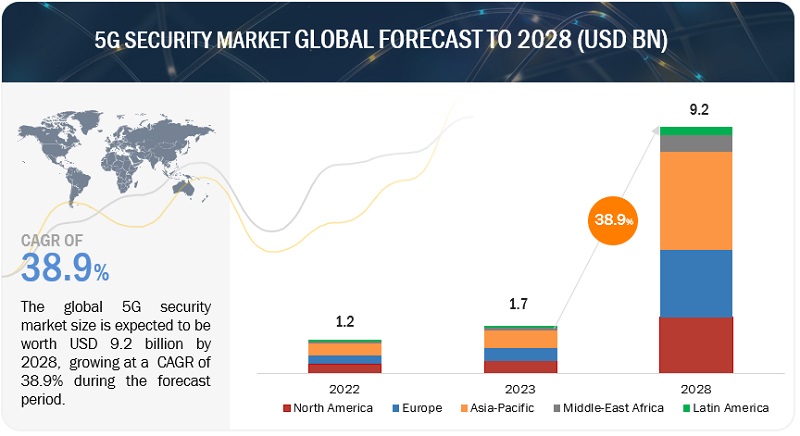
The global 5G security market size was valued at $1.3 billion in 2022 and is predicted to reach $7.2 billion by 2027, increasing at a CAGR of 41.6% from 2022 to 2027. Our analysis provides in-depth details on recent market developments, conferences, webinars, patent analysis, important stakeholder information, and pricing analysis in this new research report.
To know about the assumptions considered for the study, Request for Free Sample Report
COVID-19 Impact
The outbreak of COVID-19 has significantly impacted operations in a few key verticals, such as manufacturing, logistics, hospitality, transportation, healthcare, and retail, and moderately impacted a few sectors, such as IT & telecom, energy & utilities, government, education, and BFSI. Hence, the impact of this factor on the market is expected to be moderate across global sectors.
5G Security Market Dynamics
Driver: Rising attacks on critical infrastructure
Hackers are targeting IoT devices and taking advantage of known vulnerabilities, such as those related to default username, password, and static code backdoor is on the rise. Nowadays, all verticals are adopting automation with the integration of IoT and high-speed networks. Critical infrastructures, such as electricity, water, and other important resources, are among the early adopters of technologies and are in the phase of automation. Automation, while making the operations much more efficient, has also made the systems prone to cyberattacks. The growing vulnerability of critical systems is now the prime concern of all governments. Either accidental or malicious interference with the controls of a nuclear reactor poses a severe threat to human life and property.
Restraint: Delay in standardization of spectrum allocation
The use of higher frequencies is a major advantage in the development of the 5G network. However, all high frequencies (radio spectrum) are already used for different applications, such as telecommunications services and government agencies. To develop 5G infrastructure, accessing these high-frequency spectrums is crucial. As it is already allocated for different applications, there is conflict in accessing these frequency bands. However, there is no clarity on the definite timeframe as to when wireless operators would be given access to these spectrums to implement 5G infrastructure. As of now, different regulations are being set by different government agencies across all regions. For instance, Ofcom (UK), UK’s communications regulator, has suggested allocating a 6 GHz frequency band for 5G infrastructure, while the Federal Communications Commission (FCC) in the US has allocated frequencies from ~24 GHz. In South Korea, the Ministry of Science and ICT auctioned 3.5 GHz and 28 GHz bands for 5G services in June 2018. This irregularity in spectrum allocation and the delay in agreement on spectrum use are the factors hampering the clarity of the exact security requirement, thereby increasing the network's vulnerability. The standardization of spectrum allocation across regions and countries is extremely important for the development of 5G infrastructure. It impacts the economies of scale and clarifies equipment vendors for developing suitable products.
Opportunity: Increasing operator investments for dynamic infrastructure
With increasing network attacks, many operators have focused on securing their carrier network. For instance, after the O2 Telefonica bank attack, the Spanish operator employed 1,000 security staff and 650 analysts in seven Security Operations Centers (SOCs) around the globe. Moreover, British Telecom (BT), authorized to accredit its systems and networks for UK government use, has 3,000 security professionals in 15 SOCs across the globe. BT denotes the use of AI to keep its customers’ data safe. Its machine-assisted cyber threat hunting technology uses visual interfaces to identify and understand cybersecurity threats for large amounts of data. These investments are carried out to improve the network security measures, thus, creating a huge opportunity for the growth of 5G security solutions.
Challenge: Uncertainty around ROI and other unprecedented challenges
5G deployments are in the introductory stage of their product life cycle with standalone solution-related transitioning that requires a significant amount of work. 5G ensures several advantages, such as CUPS and network slicing. Operators need end-to-end 5G networks to be expansible, high-performance, and flexible to efficiently deliver extensive services expected by users, which finally brings competitive advantages to operators. However, the challenges with 5G rollouts, which telcos face, include aligning with the company’s long-term interest in entering the industry and value proposition credibility with the target market segment. The level of market success also depends on the financial investment committed. However, telcos do not want to indulge in over-investments before experiencing RoI or real traction.
By Component, the services segment to have a higher growth during the forecast period
Services in the 5G security market have a key role to play. The changing trends in technologies have surged the need for services by end users. A 5G security network is new to telecom operators and enterprise customers and needs to be managed end-to-end. The deployment of 5G security networks requires expertise and special skill sets, which drive the demand for consulting, implementation, and support & maintenance services. These services help end users effectively secure their 5G network infrastructure to gain desirable business outcomes.
By Deployment mode, the cloud segment to dominate the market during the forecast period
Cloud is the fastest-growing deployment mode in the 5G security market, especially among SMEs, as it is cost-effective. SMEs, in particular, have implemented cloud services to focus on their core competencies rather than investing in the security infrastructure. Cloud-based solutions utilize detection and scrubbing technologies to detect and mitigate network cyberattacks. The cloud deployment type helps manage DNS, rerouting traffic, and safeguard the website traffic. Security Operations Centers (SOCs) help support and assist cyber threat management. By deploying 5G security solutions and services on the cloud, organizations can avoid spending on hardware, software, storage, and technical staff. The cloud deployment type is often used for both private and public clouds and may vary from case to case, depending on the client's requirement. Additionally, organizations can scale up or down, depending on their use of cloud-based 5G security services.
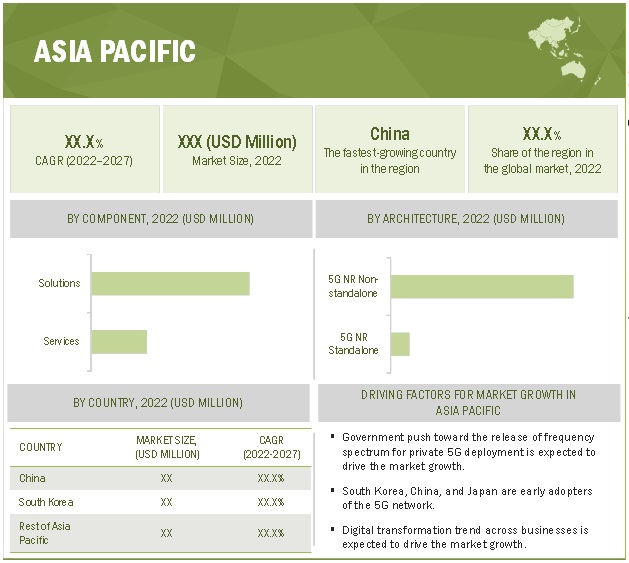
APAC to grow at the second-highest CAGR during the forecast period
The large population in the Asia Pacific has created an extensive pool of mobile subscribers for telecom companies. The region is the largest contributor to the total number of mobile subscribers across the globe and will add more subscribers to its network in the coming years. It is a diversified region that houses a wide range of countries moving toward digital transformation. The Asia Pacific region is set to dominate leading technologies, such as 5G, edge computing, blockchain, and 5G security. The main reason for the domination is the size, diversity, and the strategic lead taken by countries, which includes Singapore, South Korea, China, Australia, and Japan. Japan and China are the largest manufacturing economies that produce automobiles, IT products, networking products, and electronic products.
To know about the assumptions considered for the study, download the pdf brochure
Top Companies in 5G Security Market
The report includes the study of key Companies 5G security market. It profiles major vendors in the market. The major vendors in the market include
- Ericsson (Sweden)
- Palo Alto Networks (US)
- Cisco (US)
- Allot (Israel)
- Huawei (China)
- A10 Networks (US)
- Nokia (Finland)
- F5 Networks (US)
- Juniper Networks (US)
- Spirent (US).
The study includes an in-depth competitive analysis of these key players in the offering 5G security market with their company profiles, recent developments, and key market strategies.
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
Request Sample Scope of the Report
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
|
Report Metrics |
Details |
|
Market Revenue in 2022 |
$1.3 billion |
|
Estimated Value by 2027 |
$7.2 billion |
|
Growth Rate |
41.6% CAGR |
|
Market Driver |
|
|
Market Opportunity |
|
|
Forecast units |
Value (USD Billion) |
|
Segments covered |
By component, deployment mode, organization size, end user, network component security, architecture, application, vertical, and region |
|
Regions covered |
North America, Europe, Asia Pacific, and Rest of world |
This research report categorizes the 5G security market to forecast revenues and analyze trends in each of the following subsegments:
By Component:
-
Solutions
- Next Gen Firewall
- Data loss Prevention
- Antivirus/Antimalware
- Disturbed Denial of Service Protection
- Security Gateway
- Sandboxing
- Other Solutions
-
Services
- Consulting
- Implementation
- Support & Maintenance
By Deployment mode:
- On-Premises
- Cloud
By Organization Size:
- Large enterprises
- SMEs
By End User:
- Telecom Operators
- Enterprises
By Network Component Security:
- Radio Access Network Security
- Core Security
By Architecture:
- 5G NR Standalone
- 5G NR Non-Standalone
By Application:
- Virtual & Augmented Reality
- Connected Automotive
- Smart Manufacturing
- Wireless eHealth
- Smart Cities
By Vertical:
- Manufacturing
- Healthcare
- Energy & Utilities
- Reatil
- Automotive & Transportaition
- Public Safety
- Media & Entertainment
- Other Verticals
By Region:
-
North America
- US
- Canada
-
Europe
- UK
- Germany
- Rest of Europe
-
Asia Pacific
- China
- South Korea
- Rest of Asia Pacific
-
Rest of world
- Middle East and Africa
- Latin America
Recent Developments:
- In December 2021, Ericsson announced the launch of the Authentication Security Module. It is a module that helps communications service providers store crypto keys and algorithms in a Hardware Security Module (HSM), which augments security for markets and various use cases with more strict security requirements.
- In October 2021, Ericcson partnered with Singtel, a leading communications technology group in Singapore. This partnership will help accelerate 5G adoption across multiple industries and power industry partnerships to develop and deploy advanced 5G solutions in Singapore.
- In June 2021, Cisco announced the launch of its new IoT Router Portfolio. This product will help enterprise networks with the flexibility, security, and scalability needed for IoT and 5G deployment.
- In April 2021, Palo Alto Networks collaborated with DISH, a connectivity company based in the US. The collaboration will help DISH secure its 5G network. It will enable DISH to use container security and secure network slicing, real-time threat correlation, and dynamic security enforcement. It will also use a cloud-native security offering, which includes VM-series and CN-series Next-Generation Firewalls, as well as Prisma Cloud.
- In March 2021, Allot and Exetel decided to partner in the offering of parental control services to their residential customers based on Allot NetworkSecure. The engagement between Exetel and Allot is based on a recurring monthly fee derived from the actual number of subscribers using cybersecurity solutions.
Frequently Asked Questions (FAQ):
How big is the market for 5G security?
What is the estimated growth rate (CAGR) of the global 5G security market?
What are the major revenue pockets in the 5G security market currently?
Who are the major vendors in the 5G security market?
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
TABLE OF CONTENTS
1 INTRODUCTION (Page No. - 30)
1.1 OBJECTIVES OF STUDY
1.2 MARKET DEFINITION
1.2.1 INCLUSIONS AND EXCLUSIONS
1.3 MARKET SCOPE
1.3.1 MARKET SEGMENTATION
1.3.2 YEARS CONSIDERED FOR STUDY
1.4 CURRENCY CONSIDERED
TABLE 1 UNITED STATES DOLLAR, EXCHANGE RATES, 2018–2021
1.5 STAKEHOLDERS
1.6 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY (Page No. - 34)
2.1 RESEARCH DATA
FIGURE 1 GLOBAL 5G SECURITY MARKET: RESEARCH DESIGN
2.1.1 SECONDARY DATA
2.1.2 PRIMARY DATA
2.1.2.1 Breakup of primary profiles
FIGURE 2 BREAKUP OF PROFILES OF PRIMARY PARTICIPANTS: BY COMPANY TYPE, DESIGNATION, AND REGION
2.1.2.2 Key industry insights
2.2 MARKET BREAKUP AND DATA TRIANGULATION
FIGURE 3 DATA TRIANGULATION
2.3 MARKET SIZE ESTIMATION
2.3.1 BOTTOM-UP APPROACH
FIGURE 4 MARKET SIZE ESTIMATION: BOTTOM-UP APPROACH- SUPPLY-SIDE ANALYSIS (1/2)
FIGURE 5 MARKET SIZE ESTIMATION: BOTTOM-UP APPROACH - SUPPLY-SIDE ANALYSIS (2/2)
2.3.2 TOP-DOWN APPROACH
FIGURE 6 MARKET SIZE ESTIMATION METHODOLOGY - APPROACH 2 (DEMAND SIDE): 5G SECURITY MARKET
2.4 MARKET FORECAST
TABLE 2 FACTOR ANALYSIS
2.5 ASSUMPTIONS FOR STUDY
TABLE 3 ASSUMPTIONS FOR STUDY
2.6 LIMITATIONS OF STUDY
3 EXECUTIVE SUMMARY (Page No. - 43)
FIGURE 7 5G SECURITY MARKET, 2020–2027
FIGURE 8 LEADING SEGMENTS IN MARKET IN 2022
FIGURE 9 MARKET, REGIONAL AND COUNTRY-WISE SHARES, 2022
FIGURE 10 ASIA PACIFIC TO BE BEST MARKET FOR INVESTMENTS DURING FORECAST PERIOD
4 PREMIUM INSIGHTS (Page No. - 50)
4.1 ATTRACTIVE OPPORTUNITIES IN MARKET
FIGURE 11 RISING SECURITY CONCERNS IN 5G NETWORKS TO DRIVE MARKET GROWTH
4.2 5G SECURITY MARKET, BY DEPLOYMENT MODE
FIGURE 12 ON-PREMISES SEMENT TO LEAD MARKET DURING FORECAST PERIOD
4.3 NORTH AMERICAN MARKET, 2022
FIGURE 13 SOLUTIONS SEGMENT AND US TO ACCOUNT FOR LARGER MARKET SHARES IN NORTH AMERICA IN 2022
4.4 ASIA PACIFIC MARKET, 2022
FIGURE 14 SOLUTIONS SEGMENT AND CHINA TO ACCOUNT FOR LARGER MARKET SHARES IN ASIA PACIFIC IN 2022
4.5 MARKET, BY COUNTRY
FIGURE 15 CHINA TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
5 MARKET OVERVIEW AND INDUSTRY TRENDS (Page No. - 53)
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
FIGURE 16 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES: 5G SECURITY MARKET
5.2.1 DRIVERS
5.2.1.1 Security concerns in 5G network
FIGURE 17 5G SECURITY THREAT LANDSCAPE
5.2.1.2 Increasing IoT connections to pave way for mMTC with enhanced security requirement
FIGURE 18 GLOBAL INTERNET OF THINGS CONNECTIONS (BILLION)
5.2.1.3 Increasing ransomware attacks on IoT devices
5.2.1.4 Rising attacks on critical infrastructure
5.2.2 RESTRAINTS
5.2.2.1 Delay in standardization of spectrum allocation
5.2.2.2 Expensive security solutions impacting budget of SMEs
5.2.3 OPPORTUNITIES
5.2.3.1 Increasing operator investments for dynamic infrastructure
5.2.3.2 Demand for private 5G across enterprises, governments, and industrial sectors
5.2.4 CHALLENGES
5.2.4.1 Uncertainty around ROI and other unprecedented challenges
5.3 COVID-19 PANDEMIC-DRIVEN MARKET DYNAMICS AND FACTOR ANALYSIS
5.3.1 DRIVERS AND OPPORTUNITIES
5.3.2 RESTRAINTS AND CHALLENGES
5.3.3 CUMULATIVE GROWTH ANALYSIS
TABLE 4 5G SECURITY MARKET: CUMULATIVE GROWTH ANALYSIS
5.4 INDUSTRY TRENDS
5.4.1 VALUE CHAIN
FIGURE 19 MARKET: VALUE CHAIN ANALYSIS
5.4.1.1 Telecom Original Equipment Manufacturers
5.4.1.2 5G Radio
5.4.1.3 5G Security
5.4.1.4 5G transport
5.4.1.5 NFV/SDN/Cloud
5.4.1.6 System Integrators/Managed Service Providers
5.4.1.7 End Users
5.4.2 ECOSYSTEM
FIGURE 20 5G SECURITY MARKET: ECOSYSTEM
TABLE 5 MARKET: ECOSYSTEM
5.4.3 PORTER’S FIVE FORCES MODEL
TABLE 6 MARKET: PORTER’S FIVE FORCES MODEL
FIGURE 21 5G SECURITY PORTER’S FIVE FORCES MODEL
5.4.3.1 Threat of New Entrants
5.4.3.2 Threat of Substitutes
5.4.3.3 Bargaining Power of Buyers
5.4.3.4 Bargaining Power of Suppliers
5.4.3.5 Rivalry Among Existing Competitors
5.4.4 KEY STAKEHOLDERS AND BUYING CRITERIA
5.4.4.1 Key Stakeholders in Buying Process
FIGURE 22 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR TOP THREE END USERS
TABLE 7 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR TOP THREE END USERS (%)
5.4.4.2 Buying Criteria
FIGURE 23 KEY BUYING CRITERIA FOR TOP THREE END USERS
TABLE 8 KEY BUYING CRITERIA FOR TOP THREE END USERS
5.4.5 IMPACT OF CERTIFICATIONS ON 5G SECURITY
5.4.6 TECHNOLOGY ANALYSIS
5.4.6.1 Wi-Fi
5.4.6.2 WIMAX
5.4.6.3 Network Slicing in Radio Access Network
5.4.6.4 Network Slicing in Core Network
5.4.6.5 Network Slicing in Transport Network
5.4.6.6 Small Cell Networks
5.4.6.7 LTE Network
FIGURE 24 LTE NETWORK LAUNCHED WORLDWIDE (2021)
5.4.6.8 Citizens Broadband Radio Service (CBRS)
FIGURE 25 THREE-TIER MODEL FOR CBRS SPECTRUM ACCESS
5.4.6.9 MulteFire
5.4.7 TRENDS AND DISRUPTIONS IMPACTING BUYERS
FIGURE 26 REVENUE SHIFT FOR 5G SECURITY MARKET
5.4.8 PATENT ANALYSIS
FIGURE 27 TOP TEN COMPANIES WITH HIGHEST NUMBER OF PATENT APPLICATIONS
TABLE 9 TOP TWENTY PATENT OWNERS
FIGURE 28 NUMBER OF PATENTS GRANTED IN TEN YEARS, 2012-2021
5.4.9 PRICING ANALYSIS
5.4.10 USE CASES
5.4.10.1 Case study 1: Mobile service provider implemented A10 Networks’ solution to scale out security for massive 5G-rollout
5.4.10.2 Case study 2: City of Williamsburg implemented Palo Alto Networks’ solution to prevent cyber threats
5.4.10.3 Case study 3: Ericsson helped Erillisverkot to provide next-generation public safety networks
5.4.11 KEY CONFERENCES & EVENTS IN 2022
TABLE 10 5G SECURITY MARKET: DETAILED LIST OF CONFERENCES & EVENTS
5.4.12 TARIFF AND REGULATORY IMPACT
5.4.12.1 General Data Protection Regulation (GDPR)
5.4.12.2 California Consumer Privacy Act (CCPA)
5.4.12.3 Payment Card Industry Data Security Standard (PCI DSS)
5.4.12.4 Health Insurance Portability and Accountability Act (HIPAA)
5.4.12.5 Digital Imaging and Communications in Medicine (DICOM)
5.4.12.6 Health Level Seven (HL7)
5.4.12.7 Gramm-Leach-Bliley (GLB) Act
5.4.12.8 Sarbanes-Oxley (SOX) Act
5.4.12.9 SOC2
5.4.12.10 Communications Decency Act (CDA)
5.4.12.11 Digital Millennium Copyright Act (DMCA)
5.4.12.12 Anti-Cybersquatting Consumer Protection Act (ACPA)
5.4.12.13 Lanham Act
TABLE 11 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 12 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 13 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 14 MIDDLE EAST & AFRICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 15 LATIN AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
6 5G SECURITY MARKET, BY COMPONENT (Page No. - 83)
6.1 INTRODUCTION
FIGURE 29 MARKET SCENARIO: OPTIMISTIC, REALISTIC, AND PESSIMISTIC
TABLE 16 MARKET SCENARIO: OPTIMISTIC, REALISTIC, AND PESSIMISTIC
FIGURE 30 SERVICES SEGMENT TO EXHIBIT HIGHER CAGR DURING FORECAST PERIOD
TABLE 17 MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
6.1.1 COMPONENT: MARKET DRIVERS
6.1.2 COMPONENT: COVID-19 IMPACT
6.2 SOLUTIONS
FIGURE 31 DDOS PROTECTION SEGMENT TO EXHIBIT HIGHEST CAGR DURING FORECAST PERIOD
TABLE 18 COMPONENT: MARKET, BY SOLUTIONS, 2020–2027 (USD MILLION)
TABLE 19 SOLUTIONS: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.2.1 NEXT-GENERATION FIREWALL
TABLE 20 NEXT-GENERATION FIREWALL: 5G SECURITY MARKET, BY REGION, 2020–2027 (USD MILLION)
6.2.2 DATA LOSS PREVENTION
TABLE 21 DATA LOSS PREVENTION: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.2.3 ANTIVIRUS/ANTIMALWARE
TABLE 22 ANTIVIRUS/ANTIMALWARE: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.2.4 DISTRIBUTED DENIAL OF SERVICE PROTECTION
TABLE 23 DISTRIBUTED DENIAL OF SERVICE PROTECTION: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.2.5 SECURITY GATEWAY
TABLE 24 SECURITY GATEWAY: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.2.6 SANDBOXING
TABLE 25 SANDBOXING: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.2.7 OTHER SOLUTIONS
TABLE 26 OTHER SOLUTIONS: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.3 SERVICES
TABLE 27 COMPONENT: 5G SECURITY MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 28 SERVICES: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.3.1 CONSULTING
TABLE 29 CONSULTING: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.3.2 IMPLEMENTATION
TABLE 30 IMPLEMENTATION: MARKET, BY REGION, 2020–2027 (USD MILLION)
6.3.3 SUPPORT & MAINTENANCE
TABLE 31 SUPPORT & MAINTENANCE: MARKET, BY REGION, 2020–2027 (USD MILLION)
7 5G SECURITY MARKET, BY DEPLOYMENT MODE (Page No. - 95)
7.1 INTRODUCTION
FIGURE 32 CLOUD DEPLOYMENT MODE TO EXHIBIT HIGHER CAGR DURING FORECAST PERIOD
TABLE 32 MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
7.1.1 DEPLOYMENT MODE: MARKET DRIVERS
7.1.2 DEPLOYMENT MODE: COVID-19 IMPACT
7.2 ON-PREMISES
TABLE 33 ON-PREMISES: MARKET, BY REGION, 2020–2027 (USD MILLION)
7.3 CLOUD
TABLE 34 CLOUD: MARKET, BY REGION, 2020–2027 (USD MILLION)
8 5G SECURITY MARKET, BY ORGANIZATION SIZE (Page No. - 99)
8.1 INTRODUCTION
8.1.1 ORGANIZATION SIZE: MARKET DRIVERS
8.1.2 ORGANIZATION SIZE: COVID-19 IMPACT
FIGURE 33 LARGE ENTERPRISES SEGMENT TO LEAD MARKET GROWTH DURING FORECAST PERIOD
TABLE 35 MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
8.2 LARGE ENTERPRISES
TABLE 36 LARGE ENTERPRISES: MARKET, BY REGION, 2020–2027 (USD MILLION)
8.3 SMALL AND MEDIUM-SIZED ENTERPRISES
TABLE 37 SMALL AND MEDIUM-SIZED ENTERPRISES: MARKET, BY REGION, 2020–2027 (USD MILLION)
9 5G SECURITY MARKET, BY END USER (Page No. - 103)
9.1 INTRODUCTION
FIGURE 34 ENTERPRISES SEGMENT TO EXHIBIT HIGHER CAGR DURING FORECAST PERIOD
TABLE 38 MARKET, BY END USER, 2020–2027 (USD MILLION)
9.1.1 END USER: MARKET DRIVERS
9.1.2 END USER: COVID-19 IMPACT
9.2 TELECOM OPERATORS
9.2.1 STATE OF 5G COMMERCIALIZATION
TABLE 39 GLOBAL 5G LAUNCH
TABLE 40 TELECOM OPERATORS: CAPITAL EXPENDITURE, 2017–2019 (USD MILLION)
TABLE 41 TELECOM OPERATORS: MARKET, BY REGION, 2020–2027 (USD MILLION)
9.3 ENTERPRISES
TABLE 42 NUMBER OF INDUSTRY, BY SECTOR
TABLE 43 GLOBAL PRIVATE LTE AND 5G SPECTRUM, BY COUNTRY
TABLE 44 ENTERPRISES: MARKET, BY REGION, 2020–2027 (USD MILLION)
10 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY (Page No. - 114)
10.1 INTRODUCTION
FIGURE 35 CORE SECURITY SEGMENT TO EXHIBIT HIGHER CAGR DURING FORECAST PERIOD
TABLE 45 MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
10.1.1 NETWORK COMPONENT SECURITY: MARKET DRIVERS
10.1.2 NETWORK COMPONENT SECURITY: COVID-19 IMPACT
10.2 RADIO ACCESS NETWORK SECURITY
TABLE 46 RADIO ACCESS NETWORK SECURITY: MARKET, BY REGION, 2020–2027 (USD MILLION)
10.3 CORE SECURITY
TABLE 47 CORE SECURITY: MARKET, BY REGION, 2020–2027 (USD MILLION)
11 5G SECURITY MARKET, BY ARCHITECTURE (Page No. - 118)
11.1 INTRODUCTION
FIGURE 36 5G NR STANDALONE TO EXHIBIT HIGHER CAGR DURING FORECAST PERIOD
TABLE 48 MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
11.1.1 ARCHITECTURE: MARKET DRIVERS
11.1.2 ARCHITECTURE: COVID-19 IMPACT
11.2 5G NR STANDALONE
TABLE 49 5G NR STANDALONE: MARKET, BY REGION, 2020–2027 (USD MILLION)
11.3 5G NR NON-STANDALONE
TABLE 50 5G NR NON-STANDALONE: MARKET, BY REGION, 2020–2027 (USD MILLION)
12 5G SECURITY MARKET, BY APPLICATION (Page No. - 122)
12.1 INTRODUCTION
FIGURE 37 WIRELESS EHEALTH SEGMENT TO EXHIBIT HIGHEST CAGR DURING FORECAST PERIOD
TABLE 51 MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
12.1.1 APPLICATION: MARKET DRIVERS
12.1.2 APPLICATION: COVID-19 IMPACT
12.2 VIRTUAL & AUGMENTED REALITY
TABLE 52 VIRTUAL & AUGMENTED REALITY: MARKET, REGION, 2020–2027 (USD MILLION)
12.3 CONNECTED AUTOMOTIVE
TABLE 53 CONNECTED AUTOMOTIVE: MARKET, REGION, 2020–2027 (USD MILLION)
12.4 SMART MANUFACTURING
TABLE 54 SMART MANUFACTURING: MARKET, REGION, 2020–2027 (USD MILLION)
12.5 WIRELESS EHEALTH
TABLE 55 WIRELESS EHEALTH: MARKET, REGION, 2020–2027 (USD MILLION)
12.6 SMART CITIES
TABLE 56 SMART CITIES: MARKET, REGION, 2020–2027 (USD MILLION)
13 5G SECURITY MARKET, BY VERTICAL (Page No. - 127)
13.1 INTRODUCTION
FIGURE 38 MEDIA & ENTERTAINMENT SEGMENT TO EXHIBIT HIGHEST CAGR DURING FORECAST PERIOD
TABLE 57 MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
13.1.1 VERTICAL: MARKET DRIVERS
13.1.2 VERTICAL: COVID-19 IMPACT
13.2 MANUFACTURING
TABLE 58 MANUFACTURING: MARKET, BY REGION, 2020–2027 (USD MILLION)
13.3 HEALTHCARE
TABLE 59 HEALTHCARE: MARKET, BY REGION, 2020–2027 (USD MILLION)
13.4 ENERGY & UTILITIES
TABLE 60 ENERGY & UTILITIES: MARKET, BY REGION, 2020–2027 (USD MILLION)
13.5 RETAIL
TABLE 61 RETAIL: MARKET, BY REGION, 2020–2027 (USD MILLION)
13.6 AUTOMOTIVE & TRANSPORTATION
TABLE 62 AUTOMOTIVE & TRANSPORTATION: 5G SECURITY MARKET, BY REGION, 2020–2027 (USD MILLION)
13.7 PUBLIC SAFETY
TABLE 63 PUBLIC SAFETY: MARKET, BY REGION, 2020–2027 (USD MILLION)
13.8 MEDIA & ENTERTAINMENT
TABLE 64 MEDIA & ENTERTAINMENT: MARKET, BY REGION, 2020–2027 (USD MILLION)
13.9 OTHER VERTICALS
TABLE 65 OTHER VERTICALS: MARKET, BY REGION, 2020–2027 (USD MILLION)
14 5G SECURITY MARKET, BY REGION (Page No. - 136)
14.1 INTRODUCTION
14.1.1 REGION: COVID-19 IMPACT
FIGURE 39 ASIA PACIFIC TO LEAD MARKET DURING FORECAST PERIOD
TABLE 66 MARKET, BY REGION, 2020–2027 (USD MILLION)
14.2 NORTH AMERICA
14.2.1 NORTH AMERICA: 5G SECURITY MARKET DRIVERS
14.2.2 NORTH AMERICA: REGULATIONS
14.2.2.1 HIPAA
14.2.2.2 CCPA
14.2.2.3 Federal Information Security Management Act (FISMA)
14.2.2.4 Federal Information Processing Standards (NIST)
FIGURE 40 NORTH AMERICA: MARKET SNAPSHOT
TABLE 67 NORTH AMERICA: 5G SECURITY MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
TABLE 68 NORTH AMERICA: MARKET, BY SOLUTION, 2020–2027 (USD MILLION)
TABLE 69 NORTH AMERICA: MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 70 NORTH AMERICA: MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
TABLE 71 NORTH AMERICA: MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
TABLE 72 NORTH AMERICA: MARKET, BY END USER, 2020–2027 (USD MILLION)
TABLE 73 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
TABLE 74 NORTH AMERICA: MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
TABLE 75 NORTH AMERICA: MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
TABLE 76 NORTH AMERICA: MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
TABLE 77 NORTH AMERICA: MARKET, BY COUNTRY, 2020–2027 (USD MILLION)
14.2.3 UNITED STATES
14.2.3.1 Rapid growth in technology innovations and network infrastructure to drive market growth
TABLE 78 UNITED STATES: 5G SECURITY MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
TABLE 79 UNITED STATES: MARKET, BY SOLUTION, 2020–2027 (USD MILLION)
TABLE 80 UNITED STATES: MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 81 UNITED STATES: MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
TABLE 82 UNITED STATES: MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
TABLE 83 UNITED STATES: MARKET, BY END USER, 2020–2027 (USD MILLION)
TABLE 84 UNITED STATES: MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
TABLE 85 UNITED STATES: MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
TABLE 86 UNITED STATES: MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
TABLE 87 UNITED STATES: MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
14.2.4 CANADA
14.2.4.1 Public private partnerships and increased government initiatives to drive market growth
TABLE 88 CANADA: 5G SECURITY MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
TABLE 89 CANADA: MARKET, BY SOLUTION, 2020–2027 (USD MILLION)
TABLE 90 CANADA: MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 91 CANADA: MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
TABLE 92 CANADA: MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
TABLE 93 CANADA: MARKET, BY END USER, 2020–2027 (USD MILLION)
TABLE 94 CANADA: MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
TABLE 95 CANADA: MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
TABLE 96 CANADA: MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
TABLE 97 CANADA: MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
14.3 EUROPE
14.3.1 EUROPE: 5G SECURITY MARKET DRIVERS
14.3.2 EUROPE: REGULATIONS
14.3.2.1 European Market Infrastructure Regulation (EMIR)
14.3.2.2 GDPR
14.3.2.3 European Committee for Standardization (CEN)
14.3.2.4 European Technical Standards Institute (ETSI)
14.3.2.5 Other Regulations
TABLE 98 EUROPE: 5G SECURITY MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
TABLE 99 EUROPE: MARKET, BY SOLUTION, 2020–2027 (USD MILLION)
TABLE 100 EUROPE: MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 101 EUROPE: MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
TABLE 102 EUROPE: MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
TABLE 103 EUROPE: MARKET, BY END USER, 2020–2027 (USD MILLION)
TABLE 104 EUROPE: MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
TABLE 105 EUROPE: MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
TABLE 106 EUROPE: MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
TABLE 107 EUROPE: MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
TABLE 108 EUROPE: MARKET, BY COUNTRY, 2020–2027 (USD MILLION)
14.3.3 UNITED KINGDOM
14.3.3.1 Increased investments and presence of major telecommunications vendors to drive market growth
TABLE 109 UNITED KINGDOM: 5G SECURITY MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
TABLE 110 UNITED KINGDOM: MARKET, BY SOLUTION, 2020–2027 (USD MILLION)
TABLE 111 UNITED KINGDOM: MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 112 UNITED KINGDOM: MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
TABLE 113 UNITED KINGDOM: MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
TABLE 114 UNITED KINGDOM: MARKET, BY END USER, 2020–2027 (USD MILLION)
TABLE 115 UNITED KINGDOM: MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
TABLE 116 UNITED KINGDOM: MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
TABLE 117 UNITED KINGDOM: MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
TABLE 118 UNITED KINGDOM: MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
14.3.4 GERMANY
14.3.4.1 Need for stringent security across networks due to increase in cyberattacks to drive market growth
14.3.5 REST OF EUROPE
14.4 ASIA PACIFIC
14.4.1 ASIA PACIFIC: 5G SECURITY MARKET DRIVERS
14.4.2 ASIA PACIFIC: REGULATIONS
14.4.2.1 Privacy Commissioner for Personal Data (PCPD)
14.4.2.2 Act on the Protection of Personal Information (APPI)
14.4.2.3 Critical Information Infrastructure (CII)
14.4.2.4 International Organization for Standardization (ISO) 27001
14.4.2.5 Personal Data Protection Act (PDPA)
14.4.2.6 Other Regulations
FIGURE 41 ASIA PACIFIC: MARKET SNAPSHOT
TABLE 119 ASIA PACIFIC: 5G SECURITY MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
TABLE 120 ASIA PACIFIC: MARKET, BY SOLUTION, 2020–2027 (USD MILLION)
TABLE 121 ASIA PACIFIC: MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 122 ASIA PACIFIC: MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
TABLE 123 ASIA PACIFIC: MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
TABLE 124 ASIA PACIFIC: MARKET, BY END USER, 2020–2027 (USD MILLION)
TABLE 125 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
TABLE 126 ASIA PACIFIC: MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
TABLE 127 ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
TABLE 128 ASIA PACIFIC: MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
TABLE 129 ASIA PACIFIC: MARKET, BY COUNTRY, 2020–2027 (USD MILLION)
14.4.3 CHINA
14.4.3.1 Government initiatives and huge investments in network infrastructure to drive market growth
14.4.3.2 China: Regulatory Norms
14.4.4 SOUTH KOREA
14.4.4.1 Rapid growth in technology innovations and need for faster communications to drive market growth
14.4.5 REST OF ASIA PACIFIC
14.5 REST OF WORLD
TABLE 130 REST OF WORLD: 5G SECURITY MARKET, BY COMPONENT, 2020–2027 (USD MILLION)
TABLE 131 REST OF WORLD: MARKET, BY SOLUTION, 2020–2027 (USD MILLION)
TABLE 132 REST OF WORLD: MARKET, BY SERVICE, 2020–2027 (USD MILLION)
TABLE 133 REST OF WORLD: MARKET, BY NETWORK COMPONENT SECURITY, 2020–2027 (USD MILLION)
TABLE 134 REST OF WORLD: MARKET, BY ARCHITECTURE, 2020–2027 (USD MILLION)
TABLE 135 REST OF WORLD: MARKET, BY END USER, 2020–2027 (USD MILLION)
TABLE 136 REST OF WORLD: MARKET, BY DEPLOYMENT MODE, 2020–2027 (USD MILLION)
TABLE 137 REST OF WORLD: MARKET, BY VERTICAL, 2020–2027 (USD MILLION)
TABLE 138 REST OF WORLD: MARKET, BY ORGANIZATION SIZE, 2020–2027 (USD MILLION)
TABLE 139 REST OF WORLD: MARKET, BY APPLICATION, 2020–2027 (USD MILLION)
TABLE 140 REST OF WORLD: MARKET, BY SUB-REGION, 2020–2027 (USD MILLION)
14.5.1 MIDDLE EAST & AFRICA
14.5.1.1 Public private partnerships and investments from major vendors to drive market growth
14.5.1.2 Middle East & Africa: 5G Security Market Drivers
14.5.1.3 Middle East & Africa: Regulatory Norms
14.5.1.3.1 Israeli Privacy Protection Regulations (Data Security), 5777–2017
14.5.1.3.2 Cloud Computing Framework (CCF)
14.5.1.3.3 GDPR Applicability in the KSA
14.5.1.3.4 Protection of Personal Information (POPI) Act
14.5.2 LATIN AMERICA
14.5.2.1 Increased government investments toward 5G security infrastructure to drive market growth
14.5.2.2 Latin America: 5G Security Market Drivers
14.5.2.3 Latin America: Regulatory Norms
14.5.2.3.1 Brazil Data Protection Law
14.5.2.3.2 Federal Law on Protection of Personal Data Held by Individuals
15 COMPETITIVE LANDSCAPE (Page No. - 182)
15.1 OVERVIEW
15.2 MARKET EVALUATION FRAMEWORK
FIGURE 42 MARKET EVALUATION FRAMEWORK, 2019–2021
15.3 COMPETITIVE SCENARIO AND TRENDS
15.3.1 PRODUCT LAUNCHES
TABLE 141 5G SECURITY MARKET: PRODUCT LAUNCHES, 2019–2021
15.3.2 DEALS
TABLE 142 MARKET: DEALS, 2019-2021
15.3.3 OTHERS
TABLE 143 MARKET: OTHERS, 2020
15.4 MARKET SHARE ANALYSIS OF TOP PLAYERS
TABLE 144 5GMARKET: DEGREE OF COMPETITION
FIGURE 43 MARKET SHARE ANALYSIS OF COMPANIES IN MARKET
15.5 HISTORICAL REVENUE ANALYSIS
FIGURE 44 HISTORICAL REVENUE ANALYSIS, 2017–2021
15.6 COMPANY EVALUATION MATRIX OVERVIEW
15.7 COMPANY EVALUATION MATRIX METHODOLOGY AND DEFINITIONS
TABLE 145 PRODUCT FOOTPRINT WEIGHTAGE
15.7.1 STAR
15.7.2 EMERGING LEADERS
15.7.3 PERVASIVE
15.7.4 PARTICIPANTS
FIGURE 45 5G SECURITY MARKET, COMPANY EVALUATION MATRIX, 2022
15.8 COMPANY PRODUCT FOOTPRINT ANALYSIS
TABLE 146 COMPANY PRODUCT FOOTPRINT
TABLE 147 COMPANY COMPONENT FOOTPRINT
TABLE 148 COMPANY VERTICAL FOOTPRINT
TABLE 149 COMPANY REGION FOOTPRINT
15.9 COMPANY MARKET RANKING ANALYSIS
FIGURE 46 RANKING OF KEY PLAYERS IN 5G SECURITY MARKET, 2022
15.10 STARTUP/SME EVALUATION MATRIX METHODOLOGY AND DEFINITIONS
FIGURE 47 STARTUP/SME EVALUATION MATRIX: CRITERIA WEIGHTAGE
TABLE 150 STARTUP/SME EVALUATION MATRIX: CRITERIA WEIGHTAGE
15.10.1 PROGRESSIVE COMPANIES
15.10.2 RESPONSIVE COMPANIES
15.10.3 DYNAMIC COMPANIES
15.10.4 STARTING BLOCKS
FIGURE 48 STARTUP/SME EVALUATION MATRIX
15.11 COMPETITIVE BENCHMARKING FOR SME/STARTUP
TABLE 151 MARKET: DETAILED LIST OF KEY STARTUP/SMES
TABLE 152 5G SECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY PLAYERS [STARTUPS/SMES]
16 COMPANY PROFILES (Page No. - 202)
(Business overview, Products/solutions/services offered, Recent developments & MnM View)*
16.1 KEY PLAYERS
16.1.1 ERICSSON
TABLE 153 ERICSSON: BUSINESS OVERVIEW
FIGURE 49 ERICSSON: COMPANY SNAPSHOT
TABLE 154 ERICSSON: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 155 ERICSSON: PRODUCT LAUNCHES
TABLE 156 ERICSSON: DEALS
TABLE 157 ERICSSON: OTHERS
16.1.2 PALO ALTO NETWORKS
TABLE 158 PALO ALTO NETWORKS: BUSINESS OVERVIEW
FIGURE 50 PALO ALTO NETWORKS: COMPANY SNAPSHOT
TABLE 159 PALO ALTO NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 160 PALO ALTO NETWORKS: PRODUCT LAUNCHES
TABLE 161 PALO ALTO NETWORKS: DEALS
16.1.3 CISCO
TABLE 162 CISCO: BUSINESS OVERVIEW
FIGURE 51 CISCO: COMPANY SNAPSHOT
TABLE 163 CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 164 CISCO: PRODUCT LAUNCHES
TABLE 165 CISCO: DEALS
16.1.4 ALLOT
TABLE 166 ALLOT: BUSINESS OVERVIEW
FIGURE 52 ALLOT: COMPANY SNAPSHOT
TABLE 167 ALLOT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 168 ALLOT: PRODUCT LAUNCHES
TABLE 169 ALLOT: DEALS
16.1.5 HUAWEI
TABLE 170 HUAWEI: BUSINESS OVERVIEW
FIGURE 53 HUAWEI: COMPANY SNAPSHOT
TABLE 171 HUAWEI: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 172 HUAWEI: PRODUCT LAUNCHES
TABLE 173 HUAWEI: DEALS
16.1.6 A10 NETWORKS
TABLE 174 A10 NETWORKS: BUSINESS OVERVIEW
FIGURE 54 A10 NETWORKS: COMPANY SNAPSHOT
TABLE 175 A10 NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 176 A10 NETWORKS: PRODUCT LAUNCHES
16.1.7 NOKIA
TABLE 177 NOKIA: BUSINESS OVERVIEW
FIGURE 55 NOKIA: COMPANY SNAPSHOT
TABLE 178 NOKIA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 179 NOKIA: PRODUCT LAUNCHES
TABLE 180 NOKIA: DEALS
TABLE 181 NOKIA: OTHERS
16.1.8 F5 NETWORKS
TABLE 182 F5 NETWORKS: BUSINESS OVERVIEW
FIGURE 56 F5 NETWORKS: COMPANY SNAPSHOT
TABLE 183 F5 NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 184 F5 NETWORKS: PRODUCT LAUNCHES
TABLE 185 F5 NETWORKS: DEALS
TABLE 186 F5 NETWORKS: OTHERS
16.1.9 JUNIPER NETWORKS
TABLE 187 JUNIPER NETWORKS: BUSINESS OVERVIEW
FIGURE 57 JUNIPER NETWORKS: COMPANY SNAPSHOT
TABLE 188 JUNIPER NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 189 JUNIPER NETWORKS: PRODUCT LAUNCHES
TABLE 190 JUNIPER NETWORKS: DEALS
16.1.10 SPIRENT
TABLE 191 SPIRENT: BUSINESS OVERVIEW
FIGURE 58 SPIRENT: COMPANY SNAPSHOT
TABLE 192 SPIRENT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 193 SPIRENT: PRODUCT LAUNCHES
TABLE 194 SPIRENT: DEALS
16.1.11 FORTINET
16.1.12 MOBILEUM
16.1.13 TREND MICRO
16.1.14 ZTE
16.1.15 AKAMAI TECHNOLOGIES
16.1.16 COLT TECHNOLOGY SERVICES
16.1.17 CLAVISTER
16.1.18 RADWARE
16.1.19 AT&T
16.1.20 RISCURE
16.1.21 AVAST
16.1.22 G+D MOBILE SECURITY
16.1.23 CHECKPOINT SOFTWARE TECHNOLOGIES
16.1.24 FORGE ROCK
*Details on Business overview, Products/solutions/services offered, Recent developments & MnM View might not be captured in case of unlisted companies.
16.2 SMES/STARTUPS
16.2.1 POSITIVE TECHNOLOGIES
16.2.2 CELLWIZE
16.2.3 BENU NETWORKS
16.2.4 SUAVEI
16.2.5 CACHENGO
16.2.6 BROADFORWARD
16.2.7 TRILOGY
16.2.8 MOVANDI
16.2.9 DEEPSIG
16.2.10 EDGEQ
16.2.11 ALCAN SYSTEMS
16.2.12 MIXCOMM
16.2.13 MICROAMP SOLUTIONS
17 ADJACENT/RELATED MARKETS (Page No. - 263)
17.1 INTRODUCTION
17.1.1 LIMITATIONS
17.2 5G SERVICES MARKET
17.2.1 MARKET DEFINITION
17.2.2 MARKET OVERVIEW
17.2.2.1 5G services market, by end user
TABLE 195 5G SERVICES MARKET SIZE, BY END USER, 2020–2026 (USD BILLION)
TABLE 196 CONSUMERS: 5G SERVICES MARKET SIZE, BY REGION, 2020–2026 (USD BILLION)
TABLE 197 ENTERPRISES: 5G SERVICES MARKET SIZE, BY REGION, 2020–2026 (USD BILLION)
17.2.2.2 5G services market, by communication type
TABLE 198 5G SERVICES MARKET SIZE, BY COMMUNICATION TYPE, 2020–2026 (USD BILLION)
TABLE 199 FIXED WIRELESS ACCESS: 5G SERVICES MARKET SIZE, BY REGION, 2020–2026 (USD BILLION)
TABLE 200 ENHANCED MOBILE BROADBAND: 5G SERVICES MARKET SIZE, BY REGION, 2020–2026 (USD BILLION)
TABLE 201 MASSIVE MACHINE-TYPE COMMUNICATIONS: 5G SERVICES MARKET SIZE, BY REGION, 2020–2026 (USD BILLION)
TABLE 202 ULTRA-RELIABLE LOW-LATENCY: 5G SERVICES MARKET SIZE, BY REGION, 2020–2026 (USD BILLION)
17.2.2.3 5G services market, by enterprise
TABLE 203 5G SERVICES MARKET SIZE, BY ENTERPRISE, 2020–2026 (USD BILLION)
17.2.2.4 5G services market, by region
17.2.3 5G IOT MARKET
17.2.3.1 Market definition
17.2.3.2 Market overview
17.2.3.3 5G IoT market, by component
TABLE 204 5G IOT MARKET SIZE, BY COMPONENT, 2020–2026 (USD MILLION)
17.2.3.4 5G IoT market, by network type
TABLE 205 5G IOT MARKET SIZE, BY NETWORK TYPE, 2020–2026 (USD MILLION)
TABLE 206 5G STANDALONE: 5G IOT MARKET SIZE, BY REGION, 2020–2026 (USD MILLION)
TABLE 207 5G NON-STANDALONE: 5G IOT MARKET SIZE, BY REGION, 2020–2026 (USD MILLION)
17.2.3.5 5G IoT market, by end user
TABLE 208 5G IOT MARKET SIZE, BY END USER, 2020–2026 (USD MILLION)
17.2.3.6 5G IoT market, by region
TABLE 209 5G IOT MARKET SIZE, BY REGION, 2020–2026 (USD MILLION)
17.2.4 5G CORE MARKET
17.2.4.1 Market definition
17.2.4.2 Market overview
17.2.4.3 5G Core market, by component
TABLE 210 5G CORE MARKET SIZE, BY COMPONENT, 2020–2025 (USD MILLION)
TABLE 211 SOLUTIONS: 5G CORE MARKET SIZE, BY REGION, 2020–2025 (USD MILLION)
TABLE 212 5G CORE MARKET SIZE, BY SERVICE, 2020–2025 (USD MILLION)
17.2.4.4 5G Core market, by deployment model
TABLE 213 5G CORE MARKET SIZE, BY DEPLOYMENT MODEL, 2020–2025 (USD MILLION)
17.2.4.5 5G Core market, by network function
TABLE 214 5G CORE MARKET SIZE, BY END USER, 2020–2025 (USD MILLION)
17.2.4.6 5G Core market, by end user
TABLE 215 5G CORE MARKET SIZE, BY NETWORK FUNCTION, 2020–2025 (USD MILLION)
17.2.4.7 5G Core market, by region
18 APPENDIX (Page No. - 276)
18.1 DISCUSSION GUIDE
18.2 KNOWLEDGE STORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
18.3 AVAILABLE CUSTOMIZATIONS
18.4 RELATED REPORTS
18.5 AUTHOR DETAILS
The study involved four major activities in estimating the current size of the 5G security market. Exhaustive secondary research was done to collect information on the industry. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Both top-down and bottom-up approaches were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and sub segments of the 5G security market.
Secondary Research
In the secondary research process, various secondary sources were referred to for identifying and collecting information for this study. The secondary sources included annual reports; press releases and investor presentations of companies; and white papers, certified publications, and articles from recognized associations and government publishing sources; journals and various associations, have also been referred to for consolidating the report.
Secondary research was mainly used to obtain key information about industry insights, market’s monetary chain, the overall pool of key players, and market classification and segmentation according to industry trends to the bottom-most level, regional markets, and key developments from both market and technology-oriented perspectives.
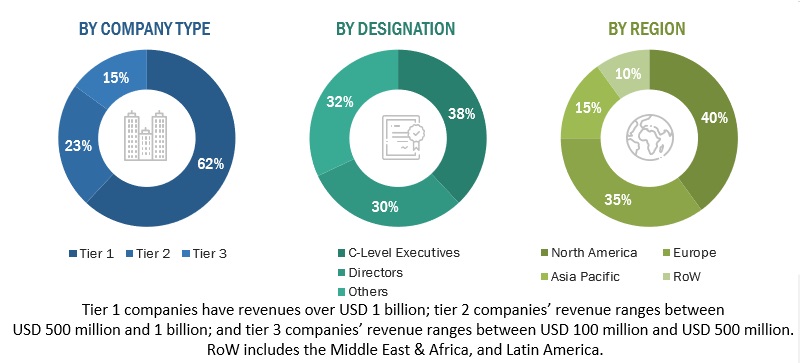
Primary Research
In the primary research process, various primary sources from both supply and demand sides of the 5G security market ecosystem were interviewed to obtain qualitative and quantitative information for this study. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various vendors providing 5G security software, associated service providers, and system integrators operating in the targeted regions. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. After the complete market engineering (including calculations for market statistics, market breakdown, market size estimations, market forecast, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also conducted to identify and validate the segmentation types; industry trends; key players; the competitive landscape of the market; and key market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key strategies.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Multiple approaches were adopted to estimate and forecast the 5G security market. The first approach involves the estimation of the market size by summation of companies’ revenue generated through the 5G security solutions and services. This procedure has studied top market players' annual and financial reports and extensive interviews of industry leaders, such as CEOs, VPs, directors, and marketing executives of leading companies, for key insights. All percentage splits and breakups have been determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to arrive at the final quantitative and qualitative data. This data has been consolidated and enhanced with detailed inputs and analysis from MarketsandMarkets.
The bottom-up procedure was employed to arrive at the overall size of the 5G security market from the revenues of key players (companies) and their market shares. The calculation was done based on estimations and by verifying key companies’ revenue through extensive primary interviews. Calculations based on the revenues of the key companies identified led to the overall market size. The overall market size was used in the top-down procedure to estimate the size of other individual segments (component, network component security, architecture, deployment mode, organization size, application, end user, vertical, and region) via the percentage splits of the market’s segments from secondary and primary research. The bottom-up procedure was also implemented for the data extracted from the secondary research to validate the market segment revenues obtained. Market shares were then estimated for each company to verify revenue shares used earlier in the bottom-up procedure. With the data triangulation procedure and data validation through primary interviews, the exact values of the overall parent market size and its segments’ market size were determined and confirmed using this study.
Data Triangulation
After arriving at the overall market size using the market size estimation processes as explained above—the market was split into several segments and subsegments. In order to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, the data triangulation and market breakdown procedures were employed, wherever applicable.
Report Objectives
- To determine and forecast the global 5G security market by component, deployment mode, organization size, end user, network component security, architecture, application, vertical, and region from 2022 to 2027, and analyze various macroeconomic and microeconomic factors that affect the market growth
- To forecast the size of the market’s segments with respect to four main regions: North America, Europe, Asia Pacific (APAC) and Rest of World (RoW).
- To analyze each submarket with respect to individual growth trends, prospects, and contributions to the overall 5G security market
- To provide detailed information regarding major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the 5G security market
- To profile key market players and provide a comparative analysis based on their business overviews, service offerings, regional presence, business strategies, and key financials
- To track and analyze competitive developments, such as mergers and acquisitions, product developments, partnerships and collaborations, and Research and Development (R&D) activities, in the market
Available Customizations
Along with the market data, MarketsandMarkets offers customizations as per the company’s specific needs. The following customization options are available for the report:
Product Analysis
- Product Matrix which gives a detailed comparison of the product portfolio of each company
Company Information
- Detailed analysis and profiling of additional market players (up to 5)




 Generating Response ...
Generating Response ...







Growth opportunities and latent adjacency in 5G Security Market