Artificial Intelligence in Cybersecurity Market by Offering (Hardware, Software, and Service), Deployment Type, Security Type, Technology (ML, NLP, and Context-Aware), Application (IAM, DLP, and UTM), End User and Geography - Global Forecast to 2028
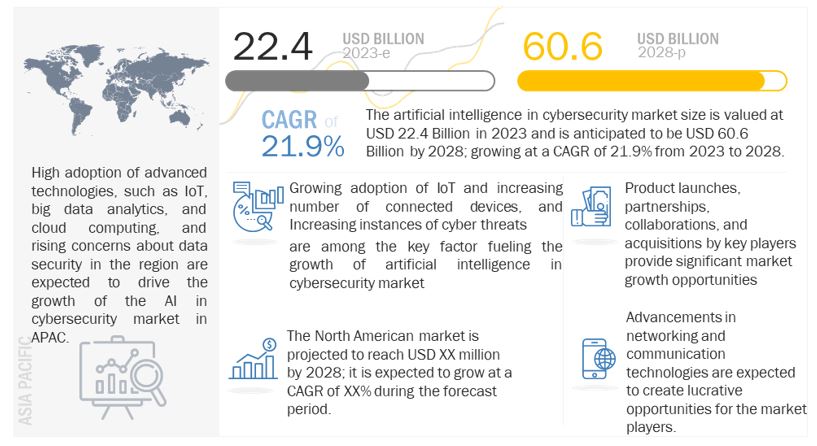
[312 Pages Report] The artificial intelligence in cybersecurity market size is valued at USD 22.4 Billion in 2023 and is anticipated to be USD 60.6 Billion by 2028; growing at a CAGR of 21.9%.
Factors such as the growing adoption of IoT and increasing number of connected devices, increasing instances of cyber threat, rising concerns of data protection, and increasing vulnerability of Wi-Fi networks to security threats are driving the growth of the AI in cybersecurity industry during the forecast period.
Artificial Intelligence in Cybersecurity Market Forecast to 2028
To know about the assumptions considered for the study, Request for Free Sample Report
Artificial intelligence in cybersecurity Market Dynamics
Driver: Increasing instances of cyber threats
The instances of cyberattacks are gradually increasing globally. Cybercriminals attack endpoints, networks, data, and other IT infrastructure that lead to a huge financial loss for individuals, enterprises, and governments. The primary motive of cybercriminals includes political rivalry, financial gain, harm reputation, international rivalry, and radical religious group interest. The majority of cyberattacks are for financial gains. WannaCry, Petya, NotPetya, and BadRabbit are among the significant ransomware that have affected enterprises and government organizations on a large scale.
According to the CISCO cybersecurity threat trends report 2021, 86% of the organizations of organizations had at least one user try to connect to a phishing site, 70% of organizations had users that were served malicious browser ads, 69% of organizations experienced some level of unsolicited crypto mining, and 50% of organizations encountered ransomware-related activity.
Cyber threats are not only hampering the productivity of businesses but also damaging the critical IT infrastructure and sensitive data of organizations. Owing to the rapid rise in the digital transaction globally across various industries, there is an increase in the frequency of cybercrimes. The increase in enterprise data breaches or data leakage is fueling the market for cybersecurity products and services. Therefore, safeguarding against cyber threats has become essential for enterprises’ business growth. Nowadays, cyber attackers are using sophisticated techniques to launch ransomware attacks and aim to raise money through small ransoms comprising a few hundred dollars each. With the advancements of technologies, automated and sophisticated cyberattacks are accelerating. The increasing sophistication of attacks is triggering organizations across the world to adopt cybersecurity solutions and services to combat with swarm cyberattacks. According to Microsoft US was the target of 46% of cyberattacks in 2020, more than double any other country.
Restraint: Inability of AI to stop zero-day and advanced threats
All algorithms or approaches used in AI, including machine learning, genetics algorithm, deep learning, or neural networks, are based on experiences from the past. This means that AI in cybersecurity is based on learning from past malware about what malware looks like and how it behaves. A zero-day threat exploits an unknown computer security vulnerability. An advanced persistent threat (APT) is a network attack in which an unauthorized person gains access to a network and stays undetected for a long period of time. APTs are armed with new methods to invoke application programming interfaces (APIs) and innovative techniques to access system resources, while a few APT behaviors might be similar to past events that AIs can recognize them, new APTs have no past events. Real protection against sophisticated, advanced threats must not rely on prior malware or prior attacks. The inability of AI to stop advanced threats is thus acting as a restraint in this market.
Opportunity: Zero trust framework providing advanced security
Zero trust is a framework that considers that the security of complex networks is constantly under threat from both internal and external threats. A zero-trust security model validates and authorizes each connection made by a user to an application or software that connects to a data set via an application programming interface (API). It helps organize and strategize a thorough approach to counter cyber threats. According to the zero-trust principle, no one or any application should ever be presumed to be trustworthy. According to the principle of least-privileged access, which is a cornerstone of zero trust, trust should be established in accordance with the context (such as user identification and location, endpoint security posture, and the app or service being requested), with policy checks at each level. It utilizes deep learning which reveals document meaning and context to provide accurate, granular categories that reflect business criticality. Once categorized, deep learning can establish a security baseline for each category. That baseline encompasses how files are permissioned, shared, stored, and managed, and it reflects the policy decisions made by the people who know those files best – the owners and end-users
Challenge: Shortcomings of AI
AI is sometimes just useful for detecting threats; it does not always remove threats. However, issues can occur even when AI is used to detect threats as AI and ML are often positioned to perform anomaly detection, which highlights unknowns while also highlighting additional unknowns that are unrelated to security. To avoid this, security teams must constantly train the existing model using training data that includes a strong feedback loop. However, it requires additional effort and cost in addition to looking into the finding itself. The idea that artificial intelligence and machine learning can take the place of human judgment is a misconception. Human decision-making is unmatched. For instance, creating detection criteria based on attack paths, new vulnerabilities, and emerging threat intelligence involves context, research, and creativity. Being aware of impending attacks via research, replicating them, determining where detectability can occur across the stack, and building detections and playbooks are all distinctly human tasks that AI can assist with but cannot fully perform on its own.
Software to hold the largest market share of artificial intelligence in cybersecurity market during the forecast period
Software holds a major share of the overall AI in cybersecurity market owing to developments in AI software and related software development kits. AI systems require different types of software, including application program interfaces, such as language, speech, vision, and sensor data, along with machine learning algorithms, to realize the applications for cybersecurity. The software platforms and solutions are available at higher costs as there are only a limited number of experts that develop machine learning algorithms. Companies such as Darktrace (UK), Cylance (US), Securonix (US), and IBM (US) are among the frontrunners in the development of software for the AI in cybersecurity market.
Cloud-based deployment held the largest share of the market during the forecast period
Cloud deployment is gaining popularity among SMEs as it is cost-effective. Organizations can avoid costs related to hardware, software, storage, and technical staff by using cloud-based cybersecurity solutions. Cloud-based platforms offer a unified way in the form of SaaS-based security services to secure business applications. These platforms are beneficial for organizations that have strict budgets for security investments. SMEs deploy their solutions on the cloud as it enables them to focus on their core competencies, rather than investing their capital on security infrastructure. The cloud-based deployment is growing as cloud-cybersecurity solutions are easy to maintain and upgrade. IBM (US), Cylance (US), Microsoft (US), Amazon (US), and Darktrace (UK) are among the major providers of cloud-based deployment services.
Application security expected to grow at the second fastest rate
Application security solutions enable enterprises to secure their business-sensitive applications through greater visibility and control. The use of existing security solutions, such as IAM, web filtering, and application whitelisting, enables the security of enterprise applications and software codes from external and internal threats, such as web attacks, DDoS, site scraping, and fraud. Business-sensitive applications are among the primary targets of attackers as they carry information about critical assets, as well as processes that are followed by an enterprise. Several organizations rely on network security and neglect applications, which create a security gap and make them susceptible to attacks. The cybersecurity solutions and services prevent user applications from being attacked. These solutions and services collect the security and the event information from all web applications, after which they analyze the data for vulnerable or malicious events and study the event behavior to protect user applications. This security type includes mobile application security and web application security. The mobile application security ensures the confidentiality of the data that is transferred among mobile applications, along with transparency and visibility among the business processes. Increasing number of mobile devices is expected to drive the market for application security.
North America to hold the largest share of the artificial intelligence in cybersecurity market during the forecast period
North America being a technologically advanced region, tops the world in terms of the presence of security vendors and cyber incidents. North America is the early adopter of cybersecurity solutions and services across the world. Increasing instances of cyberattacks are identified as the most crucial economic and national security challenge by governments in the region. Businesses in this region top the world in terms of adoption of advanced technologies and infrastructures, such as cloud computing, big data analytics, and IoT. The attacks are increasing dramatically and becoming more sophisticated in nature, and targeting business applications in various industries. Sophisticated cyberattacks include DDoS, ransomware, bot attacks, malware, zero-day attacks, and spear phishing attacks. Growing trends, such as IoT, Internet of Everything (IoE), Industrial Internet of Things (IIoT), and BYOD, have brought tremendous growth in the region, but have also triggered the rise in cyberattacks and added more complexities and concerns for enterprises. The rise in threats and vulnerabilities, and government compliances have made North America the most lucrative market for different categories of vendors.
Artificial Intelligence in Security Market by Region
To know about the assumptions considered for the study, download the pdf brochure
Key Market Players:
The AI in cybersecurity Companies is dominated by a few globally established players such as NVIDIA Corporation (US), Intel Corporation (US), Xilinx Inc. (US), Samsung Electronics Co., Ltd (South Korea), Micron Technology, Inc. (US), IBM Corporation (US), Amazon Web Services, Inc. (US), Microsoft (US), Palo Alto Networks Inc. (US), Trellix (US), CrowdStrike (US), NortonLifeLock (US), Cylance Inc. (US), ThreatMetrix Inc. (US), Securonix Inc. (US), Sift Science (US), Acalvio Technologies (US), Darktrace (UK), SparkCognition Inc. (US), Fortinet (US), Check Point Software Technologies, Ltd (US), High-Tech Bridge (Switzerland), Deep Instinct (US), SentinelOne (US), Feedzai (US), Vectra Networks (US) Zimperium (US), Argus Cyber Security (Israel), Nozomi Networks (US), BitSight Technologies (US), and Antivirus companies such as Kaspersky Lab (Russia), Bitdefender (Romania), and ESET (US).
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
Request Sample Scope of the Report
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
|
Report Metric |
Details |
| Market size value in 2023 | USD 24.4 Billion |
| Market size value in 2028 | USD 60.6 Billion |
| CAGR (2023-2028) | 21.9% |
|
Years Considered |
2023–2028 |
|
On Demand Data Available |
2030 |
|
Forecast Period |
2023–2028 |
|
Forecast Units |
Value (USD Million/USD Billion) |
|
Segments Covered |
Offering, Deployment Type, Security Type, Technology, Application, End User and Geography |
|
Geographies Covered |
North America, Europe, Asia Pacific, and RoW |
|
Companies Covered |
Other players include in AI in Cybersecurity Companies. Total 36 Major Players are covered. |
Artificial Intelligence in Cybersecurity Market Highlights
The study categorizes the artificial intelligence in cybersecurity market based on offering, Deployment Type, Security Type, Applications, End Users, Technology, and Geography
|
Aspect |
Details |
|
By Offering |
|
|
BY Deployment Type |
|
|
BY Security Type |
|
|
By Technology |
|
|
By Application |
|
|
By End Users |
|
|
By Geography |
|
Recent Developments
- In September 2022, NVIDIA launched NVIDIA IGX, which is a platform for high-precision edge AI, bringing advanced security and proactive safety to sensitive industries such as manufacturing, logistics and healthcare.
- In November 2021, IBM launched QRadar XDR Connect which is a cloud-native, open XDR solution. Advanced analytics, along with artificial intelligence (AI), automation, and connected workflows from XDR offer deeper insights, quick action, and automatic response to stop and slow the progression of threats.
- In March 2021, Samsung collaborated with Mastercard (US) to work on a biometric scanning payment card with a built-in fingerprint reader,
- In December 2019, Intel acquired Habana Labs (Israel), an Israel-based developer of programmable deep learning accelerators for data centers
Frequently Asked Questions (FAQ):
What are the key benefits of using AI in cybersecurity Market in Revenue?
Artificial Intelligence in Cybersecurity refers by using of machine learning and other AI technologies to enhance majors and benefit the capabilities of cybersecurity systems. Revenue is anticipated to be USD 60.6 Billion by 2028; growing at a CAGR of 21.9%.
What are major focus area of Artificial Intelligence (AI) in cybersecurity Market?
Artificial Intelligence (AI) in cybersecurity improves threat detection and response, provides automated analysis and triage, increases accuracy, reduces false alerts, better protects against advanced threats, and enhances security operation efficiency and effectiveness.
What are some challenges in using AI for cybersecurity Market?
Integrating AI in cybersecurity involves challenges, including complexity in integrating with existing systems, data privacy and security risks, biases in AI algorithms, false alerts, and high implementation and maintenance costs.
What are some of the leading companies in the AI in cybersecurity market?
The AI in Cybersecurity market is dominated by major players including NVIDIA, Intel, Xilinx, Samsung, Micron, IBM, AWS, Microsoft, Palo Alto Networks, Trellix, CrowdStrike, and NortonLifeLock. They have adopted various strategies to expand their global presence and increase market shares.
What is the future of AI in cybersecurity Market?
The future of AI in cybersecurity is promising with growing demand for advanced security solutions, increased adoption, and advancements in AI technology resulting in sophisticated and effective security solutions. AI will play a critical role in addressing evolving cyber threats, automating manual security tasks, and improving threat detection and response. The AI in cybersecurity market is expected to continue to grow with increased investment and innovation.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
The study involved four major activities in estimating the size of the artificial intelligence in cybersecurity market. Exhaustive secondary research has been done to collect information on the market, peer market, and parent market. Validation of these findings, assumptions, and sizing with industry experts across the value chain through primary research has been the next step. Both top-down and bottom-up approaches have been employed to estimate the global market size. After that, market breakdown and data triangulation have been used to estimate the market sizes of segments and subsegments.
Secondary Research
The secondary sources referred to for this research study includes These secondary sources include biometric technologies journals and magazines; annual reports, press releases, and investor presentations of companies; white papers; certified publications and articles from recognized authors; and directories and databases such as Factiva, Hoovers, and OneSource.
Secondary research has been conducted to obtain key information about the supply chain of the artificial intelligence in cybersecurity industry, the monetary chain of the market, the total pool of key players, and market segmentation according to the industry trends to the bottommost level, regional markets, and key developments from both market- and technology oriented perspectives. The secondary data has been collected and analyzed to arrive at the overall market size, which has further been validated by primary research.
Primary Research
Extensive primary research has been conducted after acquiring an understanding of artificial intelligence in cybersecurity market scenario through secondary research. Several primary interviews have been conducted with market experts from both the demand- (consumers, industries) and supply-side (artificial intelligence in cybersecurity providers) players across four major regions, namely, North America, Europe, Asia Pacific, and the Rest of the World (the Middle East & Africa). Approximately 75% and 25% of primary interviews have been conducted from the supply and demand side, respectively. Primary data has been collected through questionnaires, emails, and telephonic interviews. In the canvassing of primaries, various departments within organizations, such as sales, operations, and administration, were covered to provide a holistic viewpoint in our report.
fter interacting with industry experts, brief sessions were conducted with highly experienced independent consultants to reinforce the findings from our primaries. This, along with the in-house subject matter experts’ opinions, has led us to the findings as described in the remainder of this report.
Market Size Estimation
Both top-down and bottom-up approaches have been used to estimate and validate the total size of the artificial intelligence in cybersecurity market. These methods have also been extensively used to estimate the sizes of various market subsegments. The research methodology used to estimate the market sizes includes the following:
- Identifying various applications that use or are expected to use artificial intelligence in cybersecurity market.
- Analyzing historical and current data pertaining to the size of the artificial intelligence in the cybersecurity market for each application
- Analyzing the average selling prices of artificial intelligence in cybersecurity based on different technologies
- Studying various paid and unpaid sources, such as annual reports, press releases, white papers, and databases
- Identifying leading providers of artificial intelligence in cybersecurity, studying their portfolios, and understanding features of their products and their underlying technologies, as well as the types of artificial intelligence in cybersecurity products offered
- Tracking ongoing and identifying upcoming developments in the market through investments, research and development activities, product launches, expansions, and partnerships, and forecasting the market size based on these developments and other critical parameters
- Carrying out multiple discussions with key opinion leaders to understand the technologies used in artificial intelligence in cybersecurity, and products wherein they are deployed, and analyze the break-up of the scope of work carried out by key manufacturers of artificial intelligence in cybersecurity solutions providers
- Verifying and crosschecking estimates at every level through discussions with key opinion leaders, such as CXOs, directors, and operations managers, and finally with domain experts at MarketsandMarkets
Market Size Estimation Methodology-Bottom-Up Approach

Data Triangulation
After arriving at the overall market size-using the market size estimation processes explained above-the market has been split into several segments and subsegments. To complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, data triangulation, and market breakdown procedures have been employed, wherever applicable. The data has been triangulated by studying various factors and trends from both the demand and supply sides.
The main objectives of this study are as follows:
- To define, describe, segment, and forecast the artificial intelligence in cybersecurity market, in terms of value, based on deployment type, security type, offering, applications, end users, and geography.
- To forecast the size of the market and its segments with respect to four main regions, namely, North America, Europe, Asia Pacific (APAC), and the Rest of the World (RoW), along with their key countries
- To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and contributions to the total market
- To provide detailed information regarding the key factors influencing market growth, such as drivers, restraints, opportunities, and challenges
- To provide a detailed analysis of the artificial intelligence in the cybersecurity value chain
- To analyze the opportunities in the market for stakeholders and provide a detailed competitive landscape of the market leaders
- To strategically profile the key players and comprehensively analyze their market ranking and core competencies2
- To analyze key growth strategies such as expansions, contracts, joint ventures, acquisitions, product launches and developments, and research and development activities undertaken by players operating in the artificial intelligence in cybersecurity market.
Available Customizations:
MarketsandMarkets offers the following customizations for this market report:
- Further breakdown of the market in different regions to the country-level
- Detailed analysis and profiling of additional market players (up to 5)












Growth opportunities and latent adjacency in Artificial Intelligence in Cybersecurity Market