Embedded Security Market Size, Share and Industry Growth Analysis Report by Security type (authentication and access management, payment and content protection), Application, Offerings (hardware, software and services) and Region (North America, Europe, APAC, RoW) - Global Growth Driver and Industry Forecast to 2027
Updated on : May 30, 2023
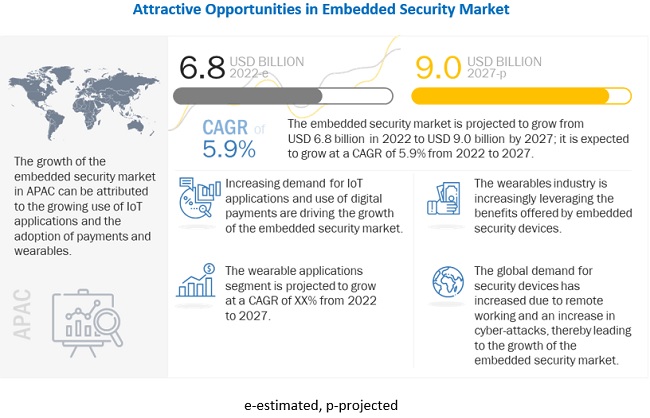
Global embedded security market in terms of revenue was estimated to be worth USD 6.8 billion in 2022 and is poised to reach USD 9.0 billion by 2027, growing at a CAGR of 5.9% from 2022 to 2027. The new research study consists of an industry trend analysis of the market.
Factors such as the growing demand for Internet of Things (IoT) applications and the inclusion of payments functionality in wearables devices are driving the growth of the embedded security market during the forecast period.
To know about the assumptions considered for the study, Request for Free Sample Report
COVID-19 Impact on the Global embedded security market
The COVID-19 pandemic has led to the growth of the embedded security market. The pandemic has impacted the market owing to remote working due to the imposition of lockdowns across the world. Remote working has led to an increase in cyber-attacks which necessitates the use of security devices to protect the devices from getting attacked. This has increased the market of embedded security devices. Key players are focusing on maintaining and generating revenues which have resulted in an increased number of developments in the market in 2021. However, this impact of the pandemic is expected to decline steadily during the forecasted period
Embedded Security Market Dynamics
Driver: Inclusion of payments functionality in wearables
Wearable technology is evolving and developing, with everything from clothing to smart glasses to jewelry to virtual reality (VR) tools (such as the Oculus Rift) being a part of it. Smart wearable technology is being employed in a variety of applications, including fitness tracking, navigation, and health monitoring. To avoid misuse, several of these apps, such as payments and smart home control, require user authorization. Embedded security solution companies are releasing new embedded security solutions to meet this niche market. For instance, STMicroelectronics (Switzerland) offers secure wearable solutions for a variety of applications, including payment, transportation, and contactless transactions. Axis Bank and Thales Group collaborated to launch "Wear N Pay," a range of contactless payment devices.
Restraint: Susceptibility of embedded systems to cyber-threats and security breaches
One of the main issues hindering the market growth of the embedded security industry is the security of embedded devices. Military forces, banks, data centers, and healthcare institutions may utilize information stored in embedded devices such as memory. As a result, protecting such devices against cyber-attacks and data breaches is critical. Because of irregular security upgrades, a long device lifecycle, remote deployment, and attack replication, embedded systems are vulnerable to cyberattacks. As a result, the embedded security market growth is expected to be hampered by its susceptibility to cyber-attacks and security breaches.
Opportunity: Growing Integration of embedded security in electric vehicles
Many innovations in the automobile sector are currently dependent on software and electronics, and IT is likely to contribute to a large percentage of the production cost. The EV market is expanding rapidly because it offers advantages over other types of vehicles. However, from the standpoint of charging infrastructure, EV charging is considerably more than a one-step, plug-and-go procedure. To ensure that every EV on the grid receives the necessary quantity of energy and electrical flow, a significant amount of communication must take place between the car, the charging point, and the utility supplier. Financial transactions and personal data should be managed responsibly and securely in some circumstances, particularly where remote EV charging is given for a fee.
Challenge: Shortage in supply of semiconductors
Semiconductors are a major component of embedded systems. The global supply chain was disrupted as a result of the 'trade war' between the United States and China. Tariffs and restrictions were placed by the two countries on each other, causing demand and supply disruptions. Supply chain disruptions have impacted multiple industries, resulting in a semiconductor shortage. The COVID-19 outbreak also wreaked havoc on the semiconductor supply chain. China is a major supplier of semiconductors; delays in supply due to the aforementioned factors have hampered the development of embedded systems.
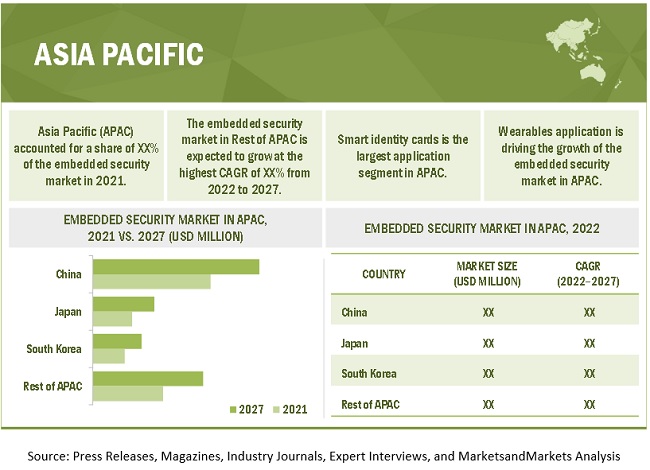
APAC held the largest market for the embedded security market in 2027 owing to the increasing adoption of embedded security devices in different wearables and automobiles being manufactured in the region
APAC is the largest market for the embedded security market. Many of the region's emerging economies, including India, China, Singapore, and Japan, are dealing with growing cybersecurity concerns. In terms of overall DNS hijackings, India ranks fifth in the globe, with tremendous growth in cybercrime registrations. Furthermore, according to Gemalto, India is responsible for 37% of global data breaches in terms of stolen or compromised data. Security is a major concern in the APAC region, which contains highly sensitive data and billions of devices connected to loT. The APAC cybersecurity market is expected to grow significantly as a result of the recent outbreak of COVID-19, as there is an increasing trend of cyber-attacks via malware and ransomware in the context of COVID-19, forcing organizations to adopt cybersecurity solutions as many have shifted to remote work environments amid lockdown in various countries. According to Microsoft. between February and May 2020, 19 million ransomware and phishing attacks were identified in Asia.
To know about the assumptions considered for the study, download the pdf brochure
Top Embedded Security Companies - Key Market Players
The embedded security companies is dominated the market by a few globally established players such as Infineon (Germany), STMicroelectronics (Switzerland), NXP (Netherlands), Qualcomm(US), Thales Group(France), Microchip Technology (US), Samsung (South Korea), Texas Instruments (US), IDEMIA (France), Renesas (Japan).
Embedded Security Market Report Scope
|
Report Attributes |
Details |
|
Market Size Value in 2022 |
USD 6.8 Billion |
| Revenue Forecast in 2027 | USD 9.0 Billion |
| Growth Rate | 5.9% |
| Base Year Considered | 2021 |
| Historical Data Available for Years | 2018–2027 |
|
Forecast Period |
2022–2027 |
|
Segments Covered |
|
|
Region Covered |
|
| Market Leaders |
|
| Top Companies in North America |
|
| Key Market Driver | Inclusion of payments functionality in wearables |
| Key Market Opportunity | Growing Integration of embedded security in electric vehicles |
| Largest Growing Region | APAC |
| Largest Market Share Segment | Payments Segment |
| Highest CAGR Segment | Wearables Segment |
| Largest Application Market Share | IoT-based Application |
The study categorizes the embedded security market based on offering, security type, application, and region.
Embedded Security Market By Offering:
- Hardware
- Software
- Services
Embedded Security Market By Security type:
- Authentication And Access Management
- Payment
- Content Protection
Embedded Security Market By Application:
- Wearables
- Smartphones
- Automotive
- Smart Identity Cards
- Industrial
- Payment Processing And Card
- Others
Embedded Security Market By Region:
- North America
- Europe
- APAC
- RoW
Recent Developments
- In January 2022, Thales Group delivered SafeNet MobilePASS+ 2.2 which is a mobile authenticator for android and windows. With a single swipe, approve push authentication requests and generate secure one-time passcodes. Authenticators can be unlocked via fingerprint or face recognition. Self-enrollment is simple and quick with QR code activation.
- In May 2021, Microchip launched Trust Platform Design Suite (TPDS) which is a software platform for device configuration and onboarding to Microchip secure provisioning services.
- In February 2021, NXP Semiconductor delivered the EdgeLock 2GO which is designed for zero-touch, secure deployment, and security maintenance of IoT devices
Frequently Asked Questions (FAQ):
What is the current size of the global embedded security market?
The embedded security market size is valued at USD 6.8 Billion in 2022 and is anticipated to be USD 9.0 Billion by 2027; growing at a CAGR of 5.9% from 2022 to 2027
Why embedded security solutions are used?
Embedded security solutions are used to protect the software that runs on top of embedded systems from any significant threats. An embedded system is made up of programmable hardware that is integrated with the operating system and software.
What is the impact of covid-19 on the embedded security market?
The COVID-19 pandemic has increased the use of contactless payments which in turn is boosting the market of embedded security solutions. Due to the imposition of lockdowns across the globe, organizations have adopted remote working which has increased the need for secure platforms to protect the sensitive data of the organizations. As a result, this has increased the use of embedded security solutions for protecting devices ensuring that only authorized users can access the data. However, the pandemic has also caused supply chain disruptions hampering the growth of embedded security solutions due to the shortage of semiconductors. The impact of supply chain disruption is expected to decrease during the forecasted period.
What are the technological trends going on in the embedded security market?
Embedded security solutions are being increasingly used in automotive and wearables applications. Payments functionality is an emerging trend in the field of embedded security solutions. contactless payments are made with contactless cards or mobile apps. Consumers can pay with a wearable device, such as a smartwatch, or with e-wallets on their smartphones. To prevent cyberattacks FinTech organizations have already begun using innovative techniques such as cryptograms to verify that the data they receive came from the customer's mobile device. Fintech companies have used a technique known as AI fuzzing to detect software vulnerabilities such as insecure APIs.
Which are the major companies in the embedded security market?
Infineon (Germany), STMicroelectronics (Switzerland), NXP (Netherlands), Qualcomm(US), Thales Group(France), Microchip Technology (US), Samsung (South Korea), Texas Instruments (US), IDEMIA (France), Renesas (Japan) are the players dominating the global embedded security market. .
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
TABLE OF CONTENTS
1 INTRODUCTION (Page No. - 29)
1.1 STUDY OBJECTIVES
1.2 DEFINITION
1.2.1 INCLUSIONS AND EXCLUSIONS
1.2.2 MARKETS COVERED
FIGURE 1 EMBEDDED SECURITY MARKET SEGMENTATION
1.2.3 GEOGRAPHIC SCOPE
1.2.4 YEARS CONSIDERED
1.3 CURRENCY
1.4 PACKAGE SIZE
1.5 LIMITATIONS
1.6 STAKEHOLDERS
1.7 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY (Page No. - 34)
2.1 RESEARCH DATA
FIGURE 2 EMBEDDED SECURITY MARKET: RESEARCH DESIGN
2.1.1 SECONDARY AND PRIMARY RESEARCH
2.1.2 SECONDARY DATA
2.1.2.1 List of major secondary sources
2.1.2.2 Secondary sources
2.1.3 PRIMARY DATA
2.1.3.1 List of primaries
2.1.3.2 Primary interviews with experts
2.1.3.3 Primary sources
2.1.3.4 Key industry insights
2.1.3.5 Breakdown of primaries
2.2 MARKET SIZE ESTIMATION
FIGURE 3 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 1 (SUPPLY SIDE)
FIGURE 4 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 2 (DEMAND SIDE)—BOTTOM-UP ESTIMATION OF EMBEDDED SECURITY MARKET, BY APPLICATION
2.2.1 BOTTOM-UP APPROACH
2.2.1.1 Approach for estimating market size by bottom-up analysis (demand side)
FIGURE 5 MARKET SIZE ESTIMATION METHODOLOGY: BOTTOM-UP APPROACH
2.2.2 TOP-DOWN APPROACH
2.2.2.1 Approach for estimating market size by top-down analysis (supply side)
FIGURE 6 MARKET SIZE ESTIMATION METHODOLOGY: TOP-DOWN APPROACH
2.3 MARKET BREAKDOWN & DATA TRIANGULATION
FIGURE 7 DATA TRIANGULATION
2.4 RISK ASSESSMENT
2.4.1 EMBEDDED SECURITY MARKET: LIMITATIONS AND ASSOCIATED RISKS
TABLE 1 LIMITATIONS AND ASSOCIATED RISKS
2.5 RESEARCH ASSUMPTIONS
2.6 LIMITATIONS
FIGURE 8 LIMITATIONS FOR RESEARCH STUDY
TABLE 2 MARKET FORECASTING METHODOLOGY ADOPTED FROM 2022 TO 2027
3 EXECUTIVE SUMMARY (Page No. - 47)
FIGURE 9 PAYMENT SEGMENT TO ACCOUNT FOR LARGEST SIZE OF EMBEDDED SECURITY MARKET, BY SECURITY TYPE, DURING FORECAST PERIOD
FIGURE 10 SMART IDENTITY CARDS SEGMENT LIKELY TO LEAD EMBEDDED SECURITY MARKET FROM 2022 TO 2027
FIGURE 11 SERVICES SEGMENT TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
FIGURE 12 EMBEDDED SECURITY MARKET TO GROW AT HIGHEST CAGR IN APAC DURING FORECAST PERIOD
3.1 COVID-19 IMPACT ON EMBEDDED SECURITY MARKET
FIGURE 13 COVID-19 IMPACT ON EMBEDDED SECURITY MARKET
3.1.1 REALISTIC SCENARIO (POST-COVID-19)
3.1.2 OPTIMISTIC SCENARIO (POST-COVID-19)
3.1.3 PESSIMISTIC SCENARIO (POST-COVID-19)
4 PREMIUM INSIGHTS (Page No. - 51)
4.1 ATTRACTIVE MARKET OPPORTUNITIES IN GLOBAL EMBEDDED SECURITY MARKET
FIGURE 14 GROWING IOT APPLICATIONS WOULD INCREASE NEED FOR IOT SECURITY, THEREBY DRIVING GROWTH OF EMBEDDED SECURITY MARKET DURING FORECAST PERIOD
4.2 EMBEDDED SECURITY MARKET, BY OFFERING
FIGURE 15 EMBEDDED SECURITY MARKET, BY OFFERING, 2018–2027
4.3 EMBEDDED SECURITY MARKET, BY APPLICATION AND SECURITY TYPE
FIGURE 16 SMART IDENTITY CARDS AND PAYMENT SEGMENTS HELD LARGEST SHARES OF EMBEDDED SECURITY MARKET IN 2021
4.4 REGION ANALYSIS OF EMBEDDED SECURITY MARKET
FIGURE 17 JAPAN TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
4.5 EMBEDDED SECURITY MARKET, BY REGION
FIGURE 18 EMBEDDED SECURITY MARKET IN APAC EXPECTED TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
4.6 EMBEDDED SECURITY MARKET, BY APPLICATION
FIGURE 19 EMBEDDED SECURITY MARKET FOR WEARABLES APPLICATION EXPECTED TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
5 MARKET OVERVIEW (Page No. - 54)
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
5.2.1 DRIVERS
5.2.1.1 Growing IoT applications would increase need for embedded security
5.2.1.2 Inclusion of payments functionality in wearables
5.2.1.3 Government agencies promoting digitization
5.2.1.4 Increase in data breaches and cyberattacks
FIGURE 20 NUMBER OF CYBERATTACKS IN US, 2005–2020
5.2.1.5 Increased demand for embedded security in electric and hybrid vehicles
5.2.1.6 Intensifying need to secure digital crypto-based transactions
5.2.2 RESTRAINTS
5.2.2.1 Non-adherence to government regulations due to lack of auditing
5.2.2.2 Susceptibility of embedded systems to cyber-threats and security breaches
5.2.2.3 Costs associated with hardware security modules
5.2.2.4 Strong inclination of customers toward adoption of hardware security modules on rental basis
5.2.3 OPPORTUNITIES
5.2.3.1 Integration of embedded security in electric vehicles
5.2.3.2 Need for integrated security solutions for IoT paired with advent of smart cities
5.2.3.3 Growing adoption of embedded systems in healthcare systems
5.2.3.4 Introduction of 5G and development of 5G-enabled embedded devices
5.2.4 CHALLENGES
5.2.4.1 Lack of awareness regarding safety and low-security budget
5.2.4.2 High energy consumption associated with compact embedded systems
5.2.4.3 Complexities involved in designing embedded systems
5.2.4.4 Shortage in supply of semiconductors
5.3 PORTER’S FIVE FORCES ANALYSIS
TABLE 3 IMPACT OF EACH FORCE ON EMBEDDED SECURITY MARKET, 2021
5.3.1 BARGAINING POWER OF SUPPLIERS
5.3.2 BARGAINING POWER OF BUYERS
5.3.3 THREAT OF NEW ENTRANTS
5.3.4 THREAT OF SUBSTITUTES
5.3.5 INTENSITY OF COMPETITIVE RIVALRY
5.4 TRADE ANALYSIS
5.4.1 EXPORT SCENARIO OF AUTOMATIC DATA PROCESSING MACHINES
TABLE 4 AUTOMATIC DATA PROCESSING MACHINES EXPORT, BY KEY COUNTRY, 2016–2020 (USD MILLION)
5.4.1.1 Import scenario of automatic data processing machines
TABLE 5 AUTOMATIC DATA PROCESSING MACHINES IMPORT, BY KEY COUNTRY, 2016–2020 (USD MILLION)
5.5 ECOSYSTEM
TABLE 6 EMBEDDED SECURITY MARKET: ECOSYSTEM
FIGURE 21 ECOSYSTEM VIEW
5.6 VALUE CHAIN ANALYSIS
FIGURE 22 ORIGINAL EQUIPMENT MANUFACTURERS AND SYSTEM INTEGRATORS ADD MAJOR VALUE TO EMBEDDED SECURITY MARKET
5.7 EMBEDDED SECURITY MARKET: CASE STUDIES
TABLE 7 EMBEDDED SECURITY STRENGTHENS CONFIDENCE IN MEDICAL TESTING EQUIPMENT
TABLE 8 GARUDA INDONESIA DEVELOPED CORPORATE MOBILITY MANAGEMENT SYSTEM TO WORK ON ELECTRONIC FLIGHT BAGS FOR PILOTS
TABLE 9 US-BASED FINANCIAL SERVICES COMPANY CREATED PUBLIC KEY INFRASTRUCTURE INVENTORY USING VENAFI PLATFORM
TABLE 10 KASPERSKY LAB AND BE.SERVICES GMBH DEVELOP EMBEDDED SECURITY SHIELD
TABLE 11 HEALTHCARE ORGANIZATION PROTECTS EMPLOYEE SAFETY, SECURITY WITH WASHABLE, RFID-EMBEDDED KEYBOARD
5.8 PATENT ANALYSIS
FIGURE 23 NUMBER OF PATENTS GRANTED PER YEAR, 2012–2022
TABLE 12 TOP 10 PATENT OWNERS FOR EMBEDDED SECURITY MARKET
FIGURE 24 TOP 10 COMPANIES WITH HIGHEST NO. OF PATENTS APPLICATION IN LAST 10 YEAR
TABLE 13 IMPORTANT PATENT REGISTRATIONS, 2018–2022
5.9 REVENUE SHIFT AND NEW REVENUE POCKETS FOR PLAYERS IN EMBEDDED SECURITY MARKET
FIGURE 25 REVENUE SHIFT IN EMBEDDED SECURITY MARKET
5.10 REGULATORY STANDARDS
5.10.1 STANDARDS IN EMBEDDED SECURITY
TABLE 14 BASE STANDARDS OF INFORMATION SECURITY
TABLE 15 STANDARDS: EUROPEAN TELECOMMUNICATIONS STANDARDS INSTITUTE
5.10.2 GLOBAL REGULATIONS FOCUSED ON FRAUD PREVENTION AND STANDARDIZATION
5.10.3 REGULATIONS IN US FOCUSED ON CONSUMER PROTECTION
5.10.4 REGULATIONS IN EUROPE FOCUSED ON STANDARDIZATION
5.10.5 REGULATIONS IN APAC FOCUSED ON DOMESTIC PAYMENT NETWORKS
6 TECHNOLOGY TRENDS (Page No. - 90)
6.1 GROWING EMPHASIS ON AUTOMOBILE SECURITY
6.2 INCREASED CONTACTLESS PAYMENT
6.3 RISE OF WEARABLES
6.4 INCREASED NUMBER OF IOT DEVICES
6.5 EMERGENCE OF 5G
6.6 AVERAGE SELLING PRICE (ASP) TRENDS
TABLE 16 AVERAGE SELLING PRICE (ASP) TRENDS
6.7 KEY CONFERENCES & EVENTS IN 2022-2023
TABLE 17 EMBEDDED SECURITY MARKET: DETAILED LIST OF CONFERENCES & EVENTS
7 EMBEDDED SECURITY MARKET, BY SECURITY TYPE (Page No. - 95)
7.1 INTRODUCTION
FIGURE 26 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2022–2027(USD MILLION)
TABLE 18 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 19 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2022–2027 (USD MILLION)
7.2 AUTHENTICATION AND ACCESS MANAGEMENT
7.2.1 AUTHENTICATION AND ACCESS MANAGEMENT DEVICES BLOCK UNAUTHORIZED USERS FROM ACCESSING DEVICES
7.3 PAYMENT
7.3.1 PAYMENT SECURITY PROVIDES SECURITY TO SENSITIVE CONSUMER DATA AND ENABLES SECURED TRANSACTIONS BETWEEN MERCHANTS AND CUSTOMERS
7.4 CONTENT PROTECTION
7.4.1 CONTENT PROTECTION PROTECTS SENSITIVE ORGANIZATIONAL DATA FROM MALICIOUS ATTACKS, FRAUDULENT ACTIVITIES, CYBER-ATTACKS, NETWORK THREATS, AND PRIVACY BREACHES
8 EMBEDDED SECURITY MARKET, BY OFFERING (Page No. - 99)
8.1 INTRODUCTION
FIGURE 27 EMBEDDED SECURITY MARKET, BY OFFERING, 2022-2027 (USD MILLION)
TABLE 20 EMBEDDED SECURITY MARKET, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 21 EMBEDDED SECURITY MARKET, BY OFFERING, 2022–2027 (USD MILLION)
8.2 HARDWARE
TABLE 22 HARDWARE SECURITY MARKET, BY PRODUCT, 2018–2021 (USD MILLION)
TABLE 23 HARDWARE SECURITY MARKET, BY PRODUCT, 2022–2027 (USD MILLION)
8.2.1 SECURE ELEMENT AND EMBEDDED SIM
8.2.1.1 Increasing number of M2M connections is driving market growth
8.2.2 EMBEDDED SIM
8.2.2.1 eSIM, is a reprogrammable chip that comes in various shapes and sizes
8.2.3 TRUSTED PLATFORM MODULE
8.2.3.1 Increasing number of cyber security threats is driving trusted platform module market
8.2.4 HARDWARE SECURITY MODULE
8.2.4.1 Increasing demand for information and data security is driving growth of hardware security module market
8.2.5 HARDWARE TOKEN
8.2.5.1 Increase in number of internet-based transactions and need for high level of security is driving hardware token market
8.3 SOFTWARE
8.3.1 FIREWALL
8.3.1.1 Firewalls stop unauthorized users from gaining access to computers or networks
8.3.2 ANTIVIRUS
8.3.2.1 Antivirus software tackles security concerns when attackers get past a firewall
8.3.3 ANTISPYWARE
8.3.3.1 Antispyware software detects specific actions taken by spyware by monitoring communications
8.3.4 NETWORK SECURITY
8.3.4.1 Network-level security implementation is more cost-efficient than other methods
8.4 SERVICES
8.4.1 SYSTEM INTEGRATED SERVICES
8.4.1.1 Systems integration services can help businesses gain connectivity
8.4.2 SUPPORT AND MAINTENANCE SERVICES
8.4.2.1 Specialized support and maintenance services help in immediate bug fixing for critical issues as well as permanent resolution for high-level optimization.
8.4.3 SECURITY CONSULTING
8.4.3.1 Security consulting assist companies in improving effectiveness of business and IT processes
9 EMBEDDED SECURITY MARKET, BY APPLICATION (Page No. - 107)
9.1 INTRODUCTION
FIGURE 28 EMBEDDED SECURITY MARKET, BY APPLICATION, 2021 (MILLION UNITS)
FIGURE 29 EMBEDDED SECURITY MARKET, BY APPLICATION, 2022–2027(USD MILLION)
TABLE 24 EMBEDDED SECURITY MARKET, BY APPLICATION, 2018-2021(USD MILLION)
TABLE 25 EMBEDDED SECURITY MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
9.2 WEARABLES
9.2.1 INCREASING PAYMENTS THROUGH WEARABLES IS DRIVING DEMAND FOR EMBEDDED SECURITY
9.3 SMARTPHONES
9.3.1 INCREASING USE OF IOT APPLICATIONS IS DRIVING NEED FOR SECURITY SOLUTIONS FOR SMARTPHONES
9.4 AUTOMOTIVE
9.4.1 GROWING DEMAND FOR CONNECTED CARS IS FUELING DEMAND FOR EMBEDDED SECURITY SOLUTIONS
9.5 SMART IDENTITY CARDS
9.5.1 EMERGENCE OF MULTI-APPLICATION SMART CARDS IS DRIVING SMART IDENTITY CARDS MARKET
9.6 INDUSTRIAL
9.6.1 INCREASING FOCUS ON INTEGRATING IOT INTO INDUSTRIAL CONTROL SYSTEMS IS DRIVING MARKET GROWTH
9.7 PAYMENT PROCESSING AND CARDS
9.7.1 INCREASING ECOMMERCE SALES, ALONG WITH GROWING INTERNET PENETRATION, IS DRIVING PAYMENT PROCESSING AND CARDS MARKET
9.8 OTHERS
10 GEOGRAPHIC ANALYSIS (Page No. - 115)
10.1 INTRODUCTION
FIGURE 30 EMBEDDED SECURITY MARKET, BY GEOGRAPHY
TABLE 26 EMBEDDED SECURITY MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 27 EMBEDDED SECURITY MARKET, BY REGION, 2022–2027 (USD MILLION)
TABLE 28 EMBEDDED SECURITY MARKET, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 29 EMBEDDED SECURITY MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 30 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 31 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 32 EMBEDDED SECURITY MARKET, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 33 EMBEDDED SECURITY MARKET, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 34 EMBEDDED SECURITY MARKET, BY HARDWARE, 2018–2021 (USD MILLION)
TABLE 35 EMBEDDED SECURITY MARKET, BY HARDWARE, 2022–2027 (USD MILLION)
10.2 EUROPE
FIGURE 31 SNAPSHOT: EMBEDDED SECURITY MARKET IN EUROPE
TABLE 36 EMBEDDED SECURITY MARKET IN EUROPE, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 37 EMBEDDED SECURITY MARKET IN EUROPE, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 38 EMBEDDED SECURITY MARKET IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 39 EMBEDDED SECURITY MARKET IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 40 EMBEDDED SECURITY MARKET IN EUROPE, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 41 EMBEDDED SECURITY MARKET IN EUROPE, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 42 EMBEDDED SECURITY MARKET IN EUROPE, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 43 EMBEDDED SECURITY MARKET IN EUROPE, BY OFFERING, 2022–2027 (USD MILLION)
10.2.1 UK
10.2.1.1 Rising cases of cyberattacks to fuel embedded security market growth in UK
TABLE 44 EMBEDDED SECURITY MARKET IN UK, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 45 EMBEDDED SECURITY MARKET IN UK, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 46 EMBEDDED SECURITY MARKET IN UK, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 47 EMBEDDED SECURITY MARKET IN UK, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 48 EMBEDDED SECURITY MARKET IN UK, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 49 EMBEDDED SECURITY MARKET IN UK, BY APPLICATION, 2022–2027 (USD MILLION)
10.2.2 GERMANY
10.2.2.1 Introduction of security concepts in manufacturing sector to boost market growth in Germany
TABLE 50 EMBEDDED SECURITY MARKET IN GERMANY, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 51 EMBEDDED SECURITY MARKET IN GERMANY, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 52 EMBEDDED SECURITY MARKET IN GERMANY, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 53 EMBEDDED SECURITY MARKET IN GERMANY, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 54 EMBEDDED SECURITY MARKET IN GERMANY, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 55 EMBEDDED SECURITY MARKET IN GERMANY, BY APPLICATION, 2022–2027 (USD MILLION)
10.2.3 FRANCE
10.2.3.1 Focus on boosting cybersecurity strategy to support market growth in France
TABLE 56 EMBEDDED SECURITY MARKET IN FRANCE, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 57 EMBEDDED SECURITY MARKET IN FRANCE, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 58 EMBEDDED SECURITY MARKET IN FRANCE, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 59 EMBEDDED SECURITY MARKET IN FRANCE, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 60 EMBEDDED SECURITY MARKET IN FRANCE, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 61 EMBEDDED SECURITY MARKET IN FRANCE, BY APPLICATION, 2022–2027 (USD MILLION)
10.2.4 REST OF EUROPE
TABLE 62 EMBEDDED SECURITY MARKET IN REST OF EUROPE, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 63 EMBEDDED SECURITY MARKET IN REST OF EUROPE, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 64 EMBEDDED SECURITY MARKET IN REST OF EUROPE, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 65 EMBEDDED SECURITY MARKET IN REST OF EUROPE, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 66 EMBEDDED SECURITY MARKET IN REST OF EUROPE, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 67 EMBEDDED SECURITY MARKET IN REST OF EUROPE, BY APPLICATION, 2022–2027 (USD MILLION)
10.3 ASIA PACIFIC
FIGURE 32 SNAPSHOT: EMBEDDED SECURITY MARKET IN ASIA PACIFIC
TABLE 68 EMBEDDED SECURITY MARKET IN APAC, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 69 EMBEDDED SECURITY MARKET IN APAC, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 70 EMBEDDED SECURITY MARKET IN APAC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 71 EMBEDDED SECURITY MARKET IN APAC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 72 EMBEDDED SECURITY MARKET IN APAC, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 73 EMBEDDED SECURITY MARKET IN APAC, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 74 EMBEDDED SECURITY MARKET IN APAC, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 75 EMBEDDED SECURITY MARKET IN APAC, BY OFFERING, 2022–2027 (USD MILLION)
10.3.1 CHINA
10.3.1.1 Increasing cyberattacks on industrial systems in China to fuel demand for embedded security
TABLE 76 EMBEDDED SECURITY MARKET IN CHINA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 77 EMBEDDED SECURITY MARKET IN CHINA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 78 EMBEDDED SECURITY MARKET IN CHINA, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 79 EMBEDDED SECURITY MARKET IN CHINA, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 80 EMBEDDED SECURITY MARKET IN CHINA, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 81 EMBEDDED SECURITY MARKET IN CHINA, BY APPLICATION, 2022–2027 (USD MILLION)
10.3.2 SOUTH KOREA
10.3.2.1 Increased exposure to cyberattacks post introduction of 5G to generate demand for embedded security in South Korea
TABLE 82 EMBEDDED SECURITY MARKET IN SOUTH KOREA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 83 EMBEDDED SECURITY MARKET IN SOUTH KOREA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 84 EMBEDDED SECURITY MARKET IN SOUTH KOREA, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 85 EMBEDDED SECURITY MARKET IN SOUTH KOREA, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 86 EMBEDDED SECURITY MARKET IN SOUTH KOREA, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 87 EMBEDDED SECURITY MARKET IN SOUTH KOREA, BY APPLICATION, 2022–2027 (USD MILLION)
10.3.3 JAPAN
10.3.3.1 Government focus on strengthening cybersecurity capabilities to boost market growth in Japan
TABLE 88 EMBEDDED SECURITY MARKET IN JAPAN, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 89 EMBEDDED SECURITY MARKET IN JAPAN, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 90 EMBEDDED SECURITY MARKET IN JAPAN, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 91 EMBEDDED SECURITY MARKET IN JAPAN, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 92 EMBEDDED SECURITY MARKET IN JAPAN, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 93 EMBEDDED SECURITY MARKET IN JAPAN, BY APPLICATION, 2022–2027 (USD MILLION)
10.3.4 REST OF APAC
TABLE 94 EMBEDDED SECURITY MARKET IN REST OF APAC, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 95 EMBEDDED SECURITY MARKET IN REST OF APAC, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 96 EMBEDDED SECURITY MARKET IN REST OF APAC, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 97 EMBEDDED SECURITY MARKET IN REST OF APAC, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 98 EMBEDDED SECURITY MARKET IN REST OF APAC, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 99 EMBEDDED SECURITY MARKET IN REST OF APAC, BY APPLICATION, 2022–2027 (USD MILLION)
10.4 NORTH AMERICA
FIGURE 33 SNAPSHOT: EMBEDDED SECURITY MARKET IN NORTH AMERICA
TABLE 100 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 101 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 102 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 103 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 104 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 105 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 106 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 107 EMBEDDED SECURITY MARKET IN NORTH AMERICA, BY OFFERING, 2022–2027 (USD MILLION)
10.4.1 US
10.4.1.1 US holds major share of embedded security market in North America
TABLE 108 EMBEDDED SECURITY MARKET IN US, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 109 EMBEDDED SECURITY MARKET IN US, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 110 EMBEDDED SECURITY MARKET IN US, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 111 EMBEDDED SECURITY MARKET IN US, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 112 EMBEDDED SECURITY MARKET IN US, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 113 EMBEDDED SECURITY MARKET IN US, BY OFFERING, 2022–2027 (USD MILLION)
10.4.2 CANADA
10.4.2.1 Growing cases of cyberattacks to foster market growth in Canada
TABLE 114 EMBEDDED SECURITY MARKET IN CANADA, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 115 EMBEDDED SECURITY MARKET IN CANADA, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 116 EMBEDDED SECURITY MARKET IN CANADA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 117 EMBEDDED SECURITY MARKET IN CANADA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 118 EMBEDDED SECURITY MARKET IN CANADA, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 119 EMBEDDED SECURITY MARKET IN CANADA, BY OFFERING, 2022–2027 (USD MILLION)
10.4.3 MEXICO
10.4.3.1 Adoption of advanced technologies in industries to augment market growth in Mexico
TABLE 120 EMBEDDED SECURITY MARKET IN MEXICO, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 121 EMBEDDED SECURITY MARKET IN MEXICO, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 122 EMBEDDED SECURITY MARKET IN MEXICO, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 123 EMBEDDED SECURITY MARKET IN MEXICO, BY SECURITY TYPE, 2022–2027 (USD MILLION
TABLE 124 EMBEDDED SECURITY MARKET IN MEXICO, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 125 EMBEDDED SECURITY MARKET IN MEXICO, BY OFFERING, 2022–2027 (USD MILLION)
10.5 REST OF THE WORLD (ROW)
TABLE 126 EMBEDDED SECURITY MARKET IN ROW, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 127 EMBEDDED SECURITY MARKET IN ROW, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 128 EMBEDDED SECURITY MARKET IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 129 EMBEDDED SECURITY MARKET IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 130 EMBEDDED SECURITY MARKET IN ROW, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 131 EMBEDDED SECURITY MARKET IN ROW, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 132 EMBEDDED SECURITY MARKET IN ROW, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 133 EMBEDDED SECURITY MARKET IN ROW, BY OFFERING, 2022–2027 (USD MILLION)
10.5.1 MIDDLE EAST AND AFRICA (MEA)
10.5.1.1 Marked rise in cyberespionages to intensify demand for embedded security in MEA
10.5.2 LATIN AMERICA
10.5.2.1 Increasing smartphone and internet adoption to drive market growth in Latin America
11 COMPETITIVE LANDSCAPE (Page No. - 157)
11.1 INTRODUCTION
FIGURE 34 GLOBAL SMARTPHONE SALES WITH EMBEDDED HARDWARE SECURITY MARKET SHARE BY VOLUME IN 2018 VS 2019 VS 2020
11.2 REVENUE ANALYSIS: TOP 4 COMPANIES
FIGURE 35 SHARE OF TOP 4 PLAYERS IN EMBEDDED SECURITY MARKET, 2018–2020
11.3 STRATEGIES OF KEY PLAYERS
11.4 MARKET SHARE ANALYSIS, 2021
TABLE 134 EMBEDDED SECURITY MARKET: MARKET SHARE ANALYSIS (2021)
FIGURE 36 MARKET SHARE ANALYSIS EMBEDDED SECURITY MARKET, 2021
11.5 COMPANY EVALUATION QUADRANT, 2021
11.5.1 STAR
11.5.2 PERVASIVE
11.5.3 EMERGING LEADER
11.5.4 PARTICIPANT
FIGURE 37 EMBEDDED SECURITY MARKET (GLOBAL): COMPANY EVALUATION QUADRANT, 2021
11.6 COMPETITIVE BENCHMARKING
11.6.1 APPLICATION AND REGIONAL FOOTPRINT ANALYSIS OF TOP PLAYERS
TABLE 135 APPLICATION AND REGIONAL FOOTPRINT OF COMPANIES
TABLE 136 APPLICATION FOOTPRINT OF COMPANIES
TABLE 137 REGIONAL FOOTPRINT OF COMPANIES
11.7 SMALL AND MEDIUM-SIZED ENTERPRISES (SME) EVALUATION QUADRANT, 2021
11.7.1 PROGRESSIVE COMPANY
11.7.2 RESPONSIVE COMPANY
11.7.3 DYNAMIC COMPANY
11.7.4 STARTING BLOCK
FIGURE 38 EMBEDDED SECURITY MARKET (GLOBAL): SME EVALUATION QUADRANT, 2021
11.8 COMPETITIVE SITUATIONS & TRENDS
TABLE 138 EMBEDDED SECURITY MARKET: PRODUCT LAUNCHES AND DEVELOPMENTS
TABLE 139 EMBEDDED SECURITY MARKET: DEALS
TABLE 140 EMBEDDED SECURITY MARKET: DETAILED LIST OF KEY STARTUPS/SMES
TABLE 141 EMBEDDED SECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES
12 COMPANY PROFILES (Page No. - 172)
12.1 KEY PLAYERS
(Business Overview, Products Offered, Product Launches, Deals, and MnM View)*
12.1.1 INFINEON TECHNOLOGIES
TABLE 142 INFINEON TECHNOLOGIES: BUSINESS OVERVIEW
FIGURE 39 INFINEON TECHNOLOGIES: COMPANY SNAPSHOT
12.1.2 STMICROELECTRONICS
TABLE 143 STMICROELECTRONICS: BUSINESS OVERVIEW
FIGURE 40 STMICROELECTRONICS: COMPANY SNAPSHOT
12.1.3 NXP SEMICONDUCTOR
TABLE 144 NXP SEMICONDUCTOR: BUSINESS OVERVIEW
FIGURE 41 NXP SEMICONDUCTORS: COMPANY SNAPSHOT
12.1.4 TEXAS INSTRUMENTS
TABLE 145 TEXAS INSTRUMENTS: BUSINESS OVERVIEW
FIGURE 42 TEXAS INSTRUMENTS: COMPANY SNAPSHOT
12.1.5 QUALCOMM
TABLE 146 QUALCOMM: BUSINESS OVERVIEW
FIGURE 43 QUALCOMM: COMPANY SNAPSHOT
12.1.6 RENESAS
TABLE 147 RENESAS: BUSINESS OVERVIEW
FIGURE 44 RENESAS: COMPANY SNAPSHOT
12.1.7 THALES GROUP
TABLE 148 THALES GROUP: BUSINESS OVERVIEW
FIGURE 45 THALES GROUP: COMPANY SNAPSHOT
12.1.8 MICROCHIP
TABLE 149 MICROCHIP: BUSINESS OVERVIEW
FIGURE 46 MICROCHIP: COMPANY SNAPSHOT
12.1.9 SAMSUNG
TABLE 150 SAMSUNG: BUSINESS OVERVIEW
FIGURE 47 SAMSUNG: COMPANY SNAPSHOT
12.1.10 IDEMIA
TABLE 151 IDEMIA: BUSINESS OVERVIEW
Business Overview, Products Offered, Product Launches, Deals, and MnM View might not be captured in case of unlisted companies.
12.2 OTHER PLAYERS
12.2.1 RAMBUS
12.2.2 CISCO
12.2.3 ESCRYPT
12.2.4 KURZ AND OVD KINEGRAM
12.2.5 BAE SYSTEMS PLC
12.2.6 LANTRONIX, INC.
12.2.7 IBM
12.2.8 SWIFT
12.2.9 MCAFEE LLC
12.2.10 BROADCOM INC
12.2.11 HITEX GMBH
12.2.12 ANALOG DEVICES INC
12.2.13 ADVANTECH CO. LTD.
12.2.14 ETA COMPUTE
12.2.15 RUNSAFE SECURITY
13 APPENDIX (Page No. - 223)
13.1 INSIGHTS OF INDUSTRY EXPERTS
13.2 DISCUSSION GUIDE
13.3 KNOWLEDGE STORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
13.4 AVAILABLE CUSTOMIZATIONS
13.5 RELATED REPORTS
13.6 AUTHOR DETAILS
The study involved four major activities in estimating the size of the embedded security market. Exhaustive secondary research has been done to collect information on the market, peer market, and parent market. Validation of these findings, assumptions, and sizing with industry experts across the value chain through primary research has been the next step. Both top-down and bottom-up approaches have been employed to estimate the global market size. After that, market breakdown and data triangulation have been used to estimate the market sizes of segments and subsegments.
Secondary Research
The secondary sources referred to for this research study includes corporate filings (such as annual reports, press releases, investor presentations, and financial statements); trade, business, and professional associations (such as Consumer Technology Association (CTA), Integrated Systems Europe, the Organisation Internationale des Constructeurs d'Automobiles (OICA), the Society for Information Display (SID), and Touch Taiwan); white papers, AR- and VR-related marketing journals, certified publications, and articles by recognized authors; gold and silver standard websites; directories; and databases.
Secondary research has been conducted to obtain key information about the supply chain of the embedded security industry, a monetary chain of the market, the total pool of key players, and market segmentation according to the industry trends to the bottommost level, regional markets, and key developments from both market- and technology oriented perspectives. The secondary data has been collected and analyzed to arrive at the overall market size, which has further been validated by primary research.
Primary Research
Extensive primary research has been conducted after acquiring an understanding of the embedded security market scenario through secondary research. Several primary interviews have been conducted with market experts from both the demand- (consumers, industries) and supply-side (embedded security device manufacturers) players across four major regions, namely, North America, Europe, Asia Pacific, and the Rest of the World (the Middle East & Africa). Approximately 70% and 30% of primary interviews have been conducted from the supply and demand side, respectively. Primary data has been collected through questionnaires, emails, and telephonic interviews. In the canvassing of primaries, various departments within organizations, such as sales, operations, and administration, were covered to provide a holistic viewpoint in our report.
After interacting with industry experts, brief sessions were conducted with highly experienced independent consultants to reinforce the findings from our primaries. This, along with the in-house subject matter experts’ opinions, has led us to the findings as described in the remainder of this report.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Both top-down and bottom-up approaches have been used to estimate and validate the total size of the embedded security market. These methods have also been extensively used to estimate the sizes of various market subsegments. The research methodology used to estimate the market sizes includes the following:
- Identifying various applications that use or are expected to use the embedded security market.
- Analyzing historical and current data pertaining to the size of the embedded security market, in terms of volume, for each application using their production statistics
- Analyzing the average selling prices of embedded security based on different technologies
- Studying various paid and unpaid sources, such as annual reports, press releases, white papers, and databases
- Identifying leading manufacturers of embedded security, studying their portfolios, and understanding features of their products and their underlying technologies, as well as the types of embedded security offered
- Tracking ongoing and identifying upcoming developments in the market through investments, research and development activities, product launches, expansions, and partnerships, and forecasting the market size based on these developments and other critical parameters
- Carrying out multiple discussions with key opinion leaders to understand the technologies used in embedded security, raw materials used to develop them, and products wherein they are deployed, and analyze the break-up of the scope of work carried out by key manufacturers of embedded security solutions providers
- Verifying and crosschecking estimates at every level through discussions with key opinion leaders, such as CXOs, directors, and operations managers, and finally with domain experts at MarketsandMarkets
Market Size Estimation Methodology-Bottom-up approach
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
After arriving at the overall market size—using the market size estimation processes explained above—the market has been split into several segments and subsegments. To complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, data triangulation, and market breakdown procedures have been employed, wherever applicable. The data has been triangulated by studying various factors and trends from both the demand and supply sides.
The main objectives of this study are as follows:
- To define, describe, segment, and forecast the embedded security market, in terms of value, based on offering, security type, application, and region
- To forecast the embedded security market, in terms of volume, based on application
- To forecast the size of the market and its segments with respect to four main regions, namely, North America, Europe, Asia Pacific (APAC), and the Rest of the World (RoW), along with their key countries
- To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and contributions to the total market
- To provide detailed information regarding the key factors influencing market growth, such as drivers, restraints, opportunities, and challenges
- To provide a detailed analysis of the embedded security supply chain
- To analyze the opportunities in the market for stakeholders and provide a detailed competitive landscape of the market leaders
- To strategically profile the key players and comprehensively analyze their market ranking and core competencies2
- To analyze key growth strategies such as expansions, contracts, joint ventures, acquisitions, product launches and developments, and research and development activities undertaken by players operating in the embedded security market
Available Customizations:
MarketsandMarkets offers the following customizations for this market report:
- Further breakdown of the market in different regions to the country-level
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...







Growth opportunities and latent adjacency in Embedded Security Market