Hardware Security Modules Market Size, Share and Industry Growth Analysis Report by Deployment Type (On-premises, Cloud Based), Type (LAN Based/Network Attached, PCI Based, USB Based, Smart Cards ), Applications, Verticals and Region (North America, Europe, APAC, RoW) - Global Growth Driver and Industry Forecast to 2027
Updated on : April 26, 2023
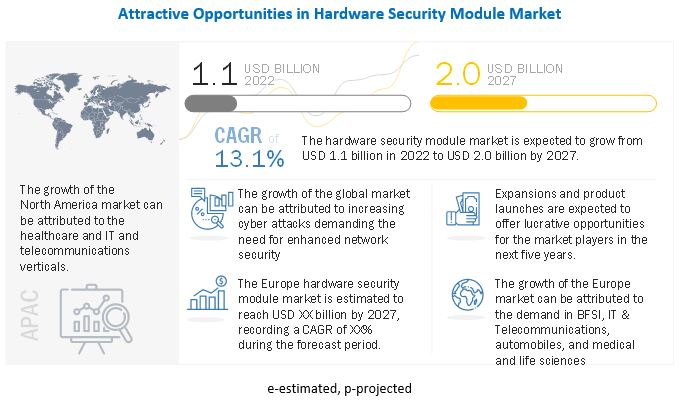
Hardware security module market size is projected to reach USD 2.0 Billion by 2027, growing at a CAGR of 13.1%.Factors such as the increase in data breaches and cyberattacks and the growing adoption of digital payments are driving the growth of the market during the forecast period.
To know about the assumptions considered for the study, Request for Free Sample Report
Hardware Security Module Market Dynamics
Driver : Increase in data breaches and cyberattacks
A data breach is an incident where information is stolen or taken from a system without the knowledge or authorization of the system’s owner. Usually, large companies or organizations are targets of data breaches.
The data stolen may be sensitive, proprietary, or confidential (such as credit card numbers, customer data, trade secrets, or national security information). Despite increased protection, government and healthcare organizations are the primary targets for cyberattacks because of the valuable personal data they collect, which can be monetized. According to a survey conducted by the UK government, 39% of businesses faced cyber attacks in 2021. The most frequent attack was phishing (83%). Out of the 39%, about 1 in 5 (21%) mentioned a more sophisticated attack type, such as a denial of service, malware, or ransomware attack.
Despite its low prevalence, organizations identified ransomware as a severe danger, and 56% of businesses have a policy against paying ransoms. Likewise, India has witnessed several data theft and breaches in recent years. Companies that are allowing employees to work from home (WFH) are not prepared to protect their data from unauthorized use or access. Thus, they are becoming a lame target for cybercriminals, increasing cybersecurity breaches. For instance, the data breach at Big Basket in 2019, in which the details of around 20 million users were put on sale on a forum on the dark web. India witnessed a 37% increase in cyberattacks in the first quarter of 2020 compared with 2019.
Hardware security modules are ideal solutions to avoid these breaches and cyberattacks, as they use secure cryptographic keys for different applications such as document signing, Secure Sockets Layer (SSL) and Transport Layer Security (TLS), code signing, and authentication. Thus, the increase in data breaches and cyberattacks is one of the major factors driving the growth of the hardware security modules industry .
Restraint: Vulnerability to cyberattacks and security breaches
Securing hardware is equally important for day-to-day business operations as securing software. However, physical device security is frequently neglected. Vulnerabilities exist because hardware security module updates are expensive.
Companies need to regularly update their cybersecurity systems to adapt to new technologies. It will be costly to upgrade hardware security modules’ cryptographic algorithm if a vulnerability is detected in it. Hardware security modules are vulnerable to cyberattacks due to irregular security upgrades, a long device lifecycle, remote deployment, and attack replication.
A remote, unauthenticated attacker can gain complete control of the vendor’s hardware security module due to the vulnerabilities. These attacks enable remote retrieval of all HSM secrets, including administrator credentials and cryptographic keys. Attackers can upload modified firmware to the hardware security module by taking advantage of a cryptographic vulnerability in the firmware signature verification.
Opportunity : Increased demand for hardware security modules with the advent of 5G
5G offers a plethora of opportunities for businesses to grow. However, if security issues are not addressed with a new trust model for the 5G era, these advantages can also be threats to the confidentiality and integrity of critical data. With 5G, various data types will be processed everywhere, from the network edge to the core.
The security environment is evolving due to 5G. Beyond consumer mobile broadband to industries and organizations, there is an increasing demand for security to effectively address an increasing number of new use cases and devices. Securing 5G requires ensuring sensitive data security. Sensitive data is consistently protected across on-premises, cloud, or hybrid storage via encryption and crypto key management. Thales is one of the leaders in the hardware security modules market.
The performance, adaptability, and scalability requirements for subscriber privacy and authentication security from the data center to the edge are met by Thales’ solutions. Public key infrastructures (PKIs), such as digital certificate management for cell towers, are given additional protection by the company’s 5G Luna hardware security modules. In the coming years, the demand for data security is likely to rise, resulting in increased demand for hardware security modules.
Challenge: Complex integration process
Hardware security modules are complex to integrate with commonly used tools and platforms. While client integrations vary between hardware security module providers, they often do not support all tools needed in a corporate environment.
Hardware security, such as hardware encryption, is often coupled to a specific device, making it less adaptable than its software counterpart because one solution cannot be used to secure the entire system and all of its components. If a company uses tools not already integrated with its hardware security modules, it needs to develop a customized integration.
Hardware security modules only expose a small number of interfaces (usually PKCS11, JCE, or CAPI/CNG), which makes developing customized integrations challenging and expensive. As a result, some organizations forgo the integrations altogether and simply leave private key material on end-user workstations to improve performance, leading to security risks.
USB-based/Portable segment to exhibit highest CAGR during the forecast period
USB-based/portable hardware security modules have a small form factor and are used for digital signature, code and document signing, and secure key storage, among other applications. These modules are ideally suitable for offline situations where the module is stored in a physical safe when not in use or where it is required to be portable.
USB-based hardware security modules enable organizations to provide high-assurance cryptographic solutions cost-effectively. Portability and USB connectivity make such modules suitable for use with laptops, workstations, and desktops. With its integrated smart card reader, this compact, full-featured module format is suited for situations with limited space or where it is used occasionally.
USB-based/portable modules have strong hardware-based security that ensures the highest levels of protection of sensitive information and data. Portable modules fit easily into a front USB slot of computers and servers and secure modern use cases such as cryptocurrency exchanges, IoT gateways and proxies, and cloud services. Portable modules verify the integrity of sensitive data stored in relatively less reliable locations such as databases and encrypt the confidential data securely for storage.
Payment Processing held the largest share of the market during the forecast period
Payment processing is a term used to describe the services and processes that automate payment transactions between a merchant and a shopper. It is usually a third-party service where a system or computer processes, verifies, and accepts or declines the transactions on behalf of the merchant through a secure Internet connection.
The importance and number of electronic transactions are increasing across industries. To prevent fraudulent activities, security protocols need to be strictly followed. HSM devices are used to protect payment transactions, such as PIN (generation, management, validation, and translation of the PIN Block in transactions carried out at POS and ATMs), electronic fund transfers (EFT), generation of data for magnetic strips and EMV chips in card production and personalization processes, processing of payment transactions with debit and credit cards, and validation of cards, users, and cry These devices typically offer cryptographic support for the payment applications of the majority of card brands, and they typically have more constrained connectivity interfaces than HSMs for general use.
Consumer goods and retail to grow at the second highest CAGR during the forecast period
The consumer goods and retail vertical includes a wide range of products that are intellectual property for the manufacturers. The safety of such information cannot be dependent solely on a software system, as insufficient security of code updates allows hackers to enter software code or steal data from the production line.
It can also allow them to take control of manufacturing software, steal or manipulate production or usage data and customer information. Management of digital rights is critical in this vertical, as the reproduction of unauthorized units that could be sold on the black market, either with authentic branding or white labeling, can lead to serious financial losses and damage to the brand’s reputation. Integration of hardware security modules prevents theft of critical product information. In the retail and consumer products vertical, hardware security modules provide solutions such as PIN card processing, message authentication, comprehensive key management, and general-purpose cryptographic processing.
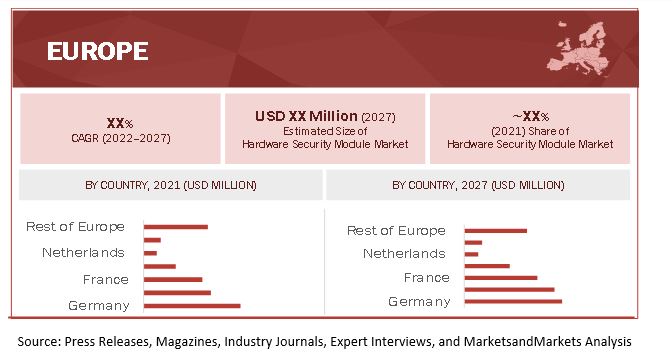
Europe to hold the largest share of the Hardware security modules market during the forecast period
Europe is projected to lead the hardware security modules market during the forecast period. The region presents a large, untapped potential for hardware security modules.
The E-Safety Vehicle Intrusion Protected Applications (EVITA) project funded by the European Union an automotive cybersecurity initiative that aimed to strengthen the automotive on-board network's resistance to attacks from emerging V2X applications as well as physical attacks made possible by the physical access that attackers can gain to vehicles in a public environment.
The consortium established three HSM security levels (Light, Medium, and Full), with several features similar to the Secure Hardware Extension (SHE) and Trusted Platform Module (TPM) specification. The biometric programs and national ID card contracts by governments in the region driven by security- and identity-related concerns are expected to boost the demand for hardware security modules for authentication purposes in Europe in the coming years.
To know about the assumptions considered for the study, download the pdf brochure
Top Hardware Security Module Companies - Key Market Players
The hardware security module companies are dominated by a few globally established players such as Thales (France), Utimaco (Germany), Futurex (US), IBM (US), STMicroelectronics (Switzerland), ATOS SE (France), Yubico (US), Infineon Technologies (Germany), Microchip Technology (US), and Swift (Belgium).
Hardware Security Module Market Report Scope
|
Report Metric |
Details |
| Estimated Market Size | USD 1.1 Billion |
|
Projected Market Size
|
USD 2.0 Billion |
| Growth Rate | 13.1% At a CAGR |
|
Market Size Available for Years |
2018–2027 |
|
Base Year Considered |
2021 |
|
Forecast Period |
2022–2027 |
|
Forecast units |
Value (USD Million/Billion) |
|
Segments Covered |
|
|
Region Covered |
|
|
Market Leaders |
|
| Top Companies in North America |
|
| Key Market Driver | Increase in data breaches and cyberattacks |
| Key Market Opportunity | Increased demand for hardware security modules with the advent of 5G |
| Largest Growing Region | Europe |
| Largest Market Share Segment | Payment Processing |
| Highest CAGR Segment | USB-based/Portable segment |
The study categorizes the hardware security module market based on Deployment Type, Type, Trends, Applications, Verticals, and Geography.
Hardware Security Module Market, By Deployment Type
- On-premise
- Cloud
Hardware Security Module Market, By Type
- LAN Based/ Network Attached
- PCI-Based/ Embedded Pluggins
- USB Based/ Portable
- Smart Cards
Hardware Security Module Industry, By Application
- Payment Processing
- Code and Document Signing
- Authentication
- Application-level encryption
- Database Encryption
- PKI and Credential Management
- Security Sockets Layer (SSL) and Transport Security Layer (TSL)
Hardware Security Module Market , By Verticals
- Consumer Goods & Retail
- Banking, Financial Services and Insurance
- Aerospace & defense
- Public Sector/ Government
- Energy and Power
- Industrial Manufacturing
- Medical and Life Sciences
- Transportation
- IT and Telecommunications
Hardware Security Module Market, By Geography
-
North America
- US
- Canada
- Mexico
-
Europe
- UK
- Germany
- France
- Italy
- Netherlands
- Russia
- Rest of Europe
-
Asia Pacific (APAC)
- China
- Japan
- India
- South Korea
- Australia
- Rest of APAC
-
Rest of the World (RoW)
- Middle East and Africa (MEA)
- South America
Recent Developments in Hardware Security Modules Industry
- In January 2022, Infineon Technologies launched Aurix TC4x, which offers enhanced connectivity as well as advanced safety and security. In addition, new SOTA (Software Over the Air) functions assist carmakers in meeting their demands for a quick and secure car-to-cloud connection, allowing for updates in the field as well as diagnosis and analysis while the vehicle is in use.
- In November 2021, Thales released its Luna network HSM 7.12. It consists of various components such as Luna T-series appliance software 7.12.0, Luna T7 Crypto Module firmware 7.12.0, Luna Client 7.12.0, Luna User Documentation Revision G. The new updates offers cryptographic mechanisms.
- In June 2021, Utimaco acquired Realsec. Realsec will provide its expertise in key management, HSM, compliance, and regulations to the Utimaco group.
- In January 2021, Utimaco acquired MYHSM (UK), a leading provider of Payment HSM as a service. This acquisition would fast-forward Utimaco’s cloud as-a-service offering, especially for, but not limited to, the retail and BFSI industries, and reduce customers’ need for investment in hardware, secure facilities, management, and ongoing PCI compliance, audit, and support.
Frequently Asked Questions (FAQ):
What is the current size of the global hardware security module market?
The hardware security module market size is valued at USD 1.1 Billion in 2022 and is anticipated to be USD 2.0 Billion by 2027; growing at a CAGR of 13.1% from 2022 to 2027.
Which is the fastest growing region for hardware security module market?
The North America region is expected to have the highest CAGR in the hardware security module market The market in this region is expected to be driven by the growing demand from the healthcare and IT and telecommunications verticals.
What is the deployment type that dominates the hardware security module market?
The cloud segment is significantly growing in the hardware security module market.
What are the key strategies adopted by key companies in the hardware security module market?
The key companies have been focusing on collaborations, acquisitions, and partnerships to significantly grow in the hardware security module market.
Which are the major companies in the hardware security module market?
Thales (France), Utimaco (Germany), Futurex (US), IBM (US), STMicroelectronics (Switzerland), ATOS SE (France), Yubico (US), Infineon Technologies (Germany), Microchip Technology (US), and Swift (Belgium) are the players dominating the global hardware security module market.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
TABLE OF CONTENTS
1 INTRODUCTION (Page No. - 31)
1.1 STUDY OBJECTIVES
1.2 MARKET DEFINITION
1.2.1 INCLUSIONS AND EXCLUSIONS
1.2.2 COMPANY: INCLUSIONS AND EXCLUSIONS
1.2.3 TYPE: INCLUSIONS AND EXCLUSIONS
1.2.4 DEPLOYMENT TYPE: INCLUSIONS AND EXCLUSIONS
1.2.5 APPLICATION: INCLUSIONS AND EXCLUSIONS
1.2.6 VERTICAL: INCLUSIONS AND EXCLUSIONS
1.2.7 REGION: INCLUSIONS AND EXCLUSIONS
1.3 STUDY SCOPE
1.3.1 MARKETS COVERED
FIGURE 1 HARDWARE SECURITY MODULES MARKET: SEGMENTATION
1.3.2 REGIONAL SCOPE
1.3.3 YEARS CONSIDERED
1.4 CURRENCY CONSIDERED
TABLE 1 CURRENCY CONVERSION RATES
1.5 LIMITATIONS
1.6 STAKEHOLDERS
1.7 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY (Page No. - 38)
2.1 RESEARCH DATA
FIGURE 2 PROCESS FLOW: HARDWARE SECURITY MODULE MARKET SIZE ESTIMATION
FIGURE 3 HARDWARE SECURITY MODULES MARKET: RESEARCH DESIGN
2.1.1 SECONDARY DATA
2.1.1.1 List of major secondary sources
2.1.1.2 Key data from secondary sources
2.1.2 PRIMARY DATA
2.1.3 PRIMARY INTERVIEWS
2.1.4 MARKET: BREAKDOWN OF PRIMARY INTERVIEWS
2.1.4.1 Primary interviews with experts
2.1.4.2 Key data from primary sources
2.1.5 SECONDARY AND PRIMARY RESEARCH
2.1.5.1 Key industry insights
2.1.5.2 Breakdown of primary interviews
2.2 MARKET SIZE ESTIMATION
FIGURE 4 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 1 (SUPPLY SIDE)—REVENUE GENERATED BY KEY PLAYERS IN MARKET
FIGURE 5 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 2 (SUPPLY SIDE)—ILLUSTRATION OF REVENUE ESTIMATION OF KEY PLAYER IN HARDWARE SECURITY MODULES MARKET
2.2.1 BOTTOM-UP APPROACH
2.2.1.1 Approach for deriving market size by bottom-up analysis (demand side)
FIGURE 6 MARKET SIZE ESTIMATION METHODOLOGY: BOTTOM-UP APPROACH
2.2.2 TOP-DOWN APPROACH
2.2.2.1 Approach for deriving market size by top-down analysis (supply side)
FIGURE 7 MARKET SIZE ESTIMATION METHODOLOGY: TOP-DOWN APPROACH
2.3 MARKET BREAKDOWN AND DATA TRIANGULATION
FIGURE 8 DATA TRIANGULATION
2.4 RISK ASSESSMENT
TABLE 2 RISK ASSESSMENT
2.5 RESEARCH ASSUMPTIONS
FIGURE 9 ASSUMPTIONS
2.5.1 RESEARCH LIMITATIONS
FIGURE 10 LIMITATIONS
3 EXECUTIVE SUMMARY (Page No. - 51)
FIGURE 11 LAN BASED/NETWORK ATTACHED SEGMENT TO LEAD HARDWARE SECURITY MODULES MARKET, BY TYPE, FROM 2022 TO 2027
FIGURE 12 CLOUD SEGMENT TO ACCOUNT FOR LARGER SHARE OF MARKET, BY DEPLOYMENT TYPE, FROM 2022 TO 2027
FIGURE 13 PAYMENT PROCESSING SEGMENT TO ACCOUNT FOR LARGEST SHARE OF MARKET, BY APPLICATION, IN 2027
FIGURE 14 BFSI SEGMENT TO HOLD LARGEST MARKET SHARE, BY VERTICAL, DURING FORECAST PERIOD
FIGURE 15 EUROPE ACCOUNTED FOR LARGEST SHARE OF MARKET IN 2021
4 PREMIUM INSIGHTS (Page No. - 55)
4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS OPERATING IN HARDWARE SECURITY MODULES MARKET
FIGURE 16 ADVANCEMENTS IN NETWORKING AND COMMUNICATION TECHNOLOGIES
4.2 HARDWARE SECURITY MODULES MARKET, BY DEPLOYMENT TYPE
FIGURE 17 CLOUD SEGMENT TO HOLD LARGER MARKET SHARE IN 2027
4.3 MARKET FOR MEDICAL & LIFE SCIENCES VERTICAL, BY REGION
FIGURE 18 EUROPE TO HOLD LARGEST SHARE OF MARKET FOR MEDICAL & LIFE SCIENCES VERTICAL DURING FORECAST PERIOD
4.4 MARKET, BY VERTICAL AND REGION
FIGURE 19 BFSI SEGMENT AND EUROPE ACCOUNTED FOR LARGEST SHARES OF MARKET IN 2021
4.5 MARKET, BY REGION
FIGURE 20 NORTH AMERICAN MARKET TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
5 MARKET OVERVIEW (Page No. - 58)
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
FIGURE 21 HARDWARE SECURITY MODULES MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
5.2.1 DRIVERS
FIGURE 22 MARKET: DRIVERS AND THEIR IMPACT
5.2.1.1 Increasing data breaches and cyberattacks
FIGURE 23 NUMBER OF CYBERATTACKS IN US, 2015–2021
5.2.1.2 Need to follow stringent data security compliances
5.2.1.3 Requirement for effective management of cryptographic keys
5.2.1.4 Growing preference for digital payments
5.2.2 RESTRAINTS
FIGURE 24 MARKET: RESTRAINTS AND THEIR IMPACT
5.2.2.1 High ownership costs associated with hardware security modules
5.2.2.2 Vulnerability to cyberattacks and security breaches
5.2.3 OPPORTUNITIES
FIGURE 25 MARKET: OPPORTUNITIES AND THEIR IMPACT
5.2.3.1 Rising demand for data security in cloud environments
5.2.3.2 Increased adoption of connected devices and Internet of Things (IoT) technologies in smart cities
5.2.3.3 Increased demand for hardware security modules with advent of 5G
5.2.4 CHALLENGES
FIGURE 26 MARKET: CHALLENGES AND THEIR IMPACT
5.2.4.1 Discovering and protecting sensitive data
5.2.4.2 Inability to control key management from outside physical protection boundary of hardware security modules
5.2.4.3 Complex integration process
5.3 VALUE CHAIN ANALYSIS
FIGURE 27 HARDWARE SECURITY MODULES MARKET: VALUE CHAIN
5.3.1 RESEARCH, DESIGN, AND DEVELOPMENT
5.3.2 RAW MATERIAL SUPPLIERS
5.3.3 ORIGINAL EQUIPMENT MANUFACTURERS (OEMS)
5.3.4 SYSTEM INTEGRATORS
5.3.5 SUPPLIERS AND DISTRIBUTORS
5.3.6 VERTICALS
5.4 ECOSYSTEM ANALYSIS
TABLE 3 MARKET: ECOSYSTEM
FIGURE 28 KEY PLAYERS IN HARDWARE SECURITY MODULES ECOSYSTEM
5.5 TECHNOLOGY ANALYSIS
5.5.1 COMMERCIALIZATION OF INTERNET OF THINGS (IOT)
5.5.2 EMERGENCE OF 5G
5.5.3 INTEGRATION OF HARDWARE SECURITY MODULES INTO CONTACTLESS SMART CARDS
5.5.4 DIGITAL SIGNATURE
5.6 AVERAGE SELLING PRICE (ASP) ANALYSIS
FIGURE 29 AVERAGE SELLING PRICE (USD) OF HARDWARE SECURITY MODULES
5.7 PATENTS ANALYSIS
TABLE 4 PATENTS RELATED TO HARDWARE SECURITY MODULES MARKET
FIGURE 30 NUMBER OF PATENTS RELATED TO MARKET, 2012–2021
TABLE 5 TOP 10 PATENT OWNERS IN MARKET
FIGURE 31 TOP 10 PATENT OWNERS IN MARKET
5.8 TRADE DATA
TABLE 6 EXPORT DATA FOR PRODUCTS UNDER HS CODE 8471, BY COUNTRY, 2017–2021 (USD THOUSAND)
TABLE 7 IMPORT DATA FOR PRODUCTS UNDER HS CODE 8471, BY COUNTRY, 2017–2021 (USD THOUSAND)
5.9 REGULATORY LANDSCAPE
5.9.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 8 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 9 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 10 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 11 ROW: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
5.9.2 GLOBAL REGULATIONS FOCUSED ON FRAUD PREVENTION AND STANDARDIZATION
5.9.3 REGULATIONS IN NORTH AMERICA FOCUSED ON CONSUMER PROTECTION
5.9.4 REGULATIONS IN EUROPE FOCUSED ON STANDARDIZATION
5.9.5 REGULATIONS IN ASIA PACIFIC FOCUSED ON DOMESTIC PAYMENT NETWORKS
5.10 PORTER’S FIVE FORCES ANALYSIS
FIGURE 32 MARKET: PORTER’S FIVE FORCES ANALYSIS
TABLE 12 IMPACT OF EACH OF PORTER’S FIVE FORCES
5.10.1 THREAT OF NEW ENTRANTS
5.10.2 THREAT OF SUBSTITUTES
5.10.3 BARGAINING POWER OF SUPPLIERS
5.10.4 BARGAINING POWER OF BUYERS
5.10.5 INTENSITY OF COMPETITIVE RIVALRY
5.11 CASE STUDY ANALYSIS
5.11.1 FARMERS & MERCHANTS BANK IMPLEMENTS CARDONCE SOLUTION OFFERED BY CPI CARD GROUP
5.11.2 RBS DEPLOYS FINGERPRINT BIOMETRIC CARDS FOR PAYMENTS
5.11.3 MASTERCARD, IDEMIA, AND MATCHMOVE PARTNERED TO LAUNCH BIOMETRIC CARDS IN ASIA
5.11.4 NASDAQ OMX PARTNERED WITH THALES TO DELIVER SECURE CLOUD FOR FINANCIAL SERVICES
TABLE 13 MARKET: DETAILED LIST OF CONFERENCES AND EVENTS
5.12 KEY STAKEHOLDERS AND BUYING PROCESS
5.12.1 KEY STAKEHOLDERS IN BUYING PROCESS
FIGURE 33 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR TOP THREE APPLICATIONS
TABLE 14 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR TOP THREE APPLICATIONS (%)
5.12.2 BUYING CRITERIA
FIGURE 34 KEY BUYING CRITERIA FOR TOP THREE APPLICATIONS
TABLE 15 KEY BUYING CRITERIA FOR TOP THREE APPLICATIONS
5.13 REVENUE SHIFT AND NEW REVENUE POCKETS FOR CUSTOMERS’ BUSINESSES
FIGURE 35 REVENUE SHIFT IN HARDWARE SECURITY MODULES MARKET
6 HARDWARE SECURITY MODULES MARKET, BY DEPLOYMENT TYPE (Page No. - 91)
6.1 INTRODUCTION
FIGURE 36 CLOUD SEGMENT TO EXHIBIT HIGHER CAGR IN HARDWARE SECURITY MODULES MARKET DURING FORECAST PERIOD
TABLE 16 MARKET, BY DEPLOYMENT TYPE, 2018–2021 (USD MILLION)
TABLE 17 MARKET, BY DEPLOYMENT TYPE, 2022–2027 (USD MILLION)
6.2 ON-PREMISE
6.2.1 GROWING NEED FOR COMPLETE CONTROL DRIVES
TABLE 18 ON-PREMISE: MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
TABLE 19 ON-PREMISE: MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
6.3 CLOUD
6.3.1 COST-EFFECTIVENESS ASSOCIATED WITH CLOUD-BASED HARDWARE SECURITY MODULES
TABLE 20 CLOUD: MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
TABLE 21 CLOUD: MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
7 HARDWARE SECURITY MODULES MARKET, BY APPLICATION (Page No. - 97)
7.1 INTRODUCTION
FIGURE 37 SECURE SOCKETS LAYER (SSL) AND TRANSPORT LAYER SECURITY (TLS) SEGMENT TO EXHIBIT HIGHEST CAGR IN MARKET DURING FORECAST PERIOD
TABLE 22 HARDWARE SECURITY MODULES MARKET, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 23 MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 24 NORTH AMERICA: MARKET, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 25 NORTH AMERICA: MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 26 EUROPE: MARKET, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 27 EUROPE: MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 28 ASIA PACIFIC: MARKET, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 29 ASIA PACIFIC: MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
TABLE 30 ROW: MARKET, BY APPLICATION, 2018–2021 (USD MILLION)
TABLE 31 ROW: MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
7.2 PAYMENT PROCESSING
7.2.1 HIGH DEMAND FOR SOPHISTICATED PAYMENT PROCESSING METHODS TO IMPROVE ELECTRONIC TRANSACTIONS
7.3 CODE AND DOCUMENT SIGNING
7.3.1 HIGH ADOPTION OF HARDWARE SECURITY MODULES FOR CODE AND DOCUMENT SIGNING
7.4 SECURITY SOCKETS LAYER (SSL) AND TRANSPORT SECURITY LAYER (TSL)
7.4.1 INCREASED DEMAND FOR SECURITY SOCKETS LAYER (SSL) AND TRANSPORT SECURITY LAYER (TSL) IN IT & TELECOMMUNICATIONS VERTICAL
7.5 AUTHENTICATION
7.5.1 GROWING NEED FOR HARDWARE SECURITY MODULES IN AUTHENTICATION APPLICATIONS
7.6 DATABASE ENCRYPTION
7.6.1 RISING FOCUS ON PROTECTING DATA THROUGH ENCRYPTION
7.7 PUBLIC KEY INFRASTRUCTURE (PKI) AND CREDENTIAL MANAGEMENT
7.7.1 INCREASING DEMAND FOR HARDWARE SECURITY MODULES IN CREDENTIAL MANAGEMENT TO ENABLE USERS TO TRANSMIT DATA SAFELY
7.8 APPLICATION-LEVEL ENCRYPTION
7.8.1 INCREASING REQUIREMENT FOR ENHANCING EFFICIENCY AND ACCURACY OF APPLICATION-LEVEL ENCRYPTION
8 HARDWARE SECURITY MODULES MARKET, BY TYPE (Page No. - 106)
8.1 INTRODUCTION
FIGURE 38 USB BASED/PORTABLE SEGMENT TO EXHIBIT HIGHEST CAGR IN HARDWARE SECURITY MODULES MARKET DURING FORECAST PERIOD
TABLE 32 MARKET, BY TYPE, 2018–2021 (USD MILLION)
TABLE 33 MARKET, BY TYPE, 2022–2027 (USD MILLION)
TABLE 34 NORTH AMERICA: MARKET, BY TYPE, 2018–2021 (USD MILLION)
TABLE 35 NORTH AMERICA: MARKET, BY TYPE, 2022–2027 (USD MILLION)
TABLE 36 EUROPE: MARKET, BY TYPE, 2018–2021 (USD MILLION)
TABLE 37 EUROPE: MARKET, BY TYPE, 2022–2027 (USD MILLION)
TABLE 38 ASIA PACIFIC: MARKET, BY TYPE, 2018–2021 (USD MILLION)
TABLE 39 ASIA PACIFIC: MARKET, BY TYPE, 2022–2027 (USD MILLION)
TABLE 40 ROW: MARKET, BY TYPE, 2018–2021 (USD MILLION)
TABLE 41 ROW: MARKET, BY TYPE, 2022–2027 (USD MILLION)
8.2 LAN BASED/NETWORK ATTACHED
8.2.1 LAN-BASED HARDWARE SECURITY MODULE ACT AS CENTRALIZED KEY MANAGEMENT SYSTEM
8.3 PCI BASED OR EMBEDDED PLUGIN
8.3.1 PCI-BASED HARDWARE SECURITY MODULES CAN SECURE ENTIRE ELECTRONIC CONTROL UNIT (ECU)
8.4 USB BASED OR PORTABLE
8.4.1 PORTABLE HARDWARE SECURITY MODULES CAN PERFORM ENCRYPTION AND KEY PROTECTION FUNCTIONS
8.5 SMART CARDS
8.5.1 SMART CARDS REDUCE RISK OF CYBERCRIMES BY PROTECTING DIGITAL ASSETS
9 HARDWARE SECURITY MODULES MARKET, BY VERTICAL (Page No. - 113)
9.1 INTRODUCTION
FIGURE 39 BFSI VERTICAL TO HOLD LARGEST MARKET SHARE DURING FORECAST PERIOD
TABLE 42 HARDWARE SECURITY MODULES MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
TABLE 43 MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
9.2 BANKING, FINANCIAL SERVICES, AND INSURANCE (BFSI)
9.2.1 RISING USE OF HARDWARE SECURITY MODULES TO MITIGATE RISKS OF ONLINE FINANCIAL FRAUD
TABLE 44 BFSI: NORTH AMERICA MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 45 BFSI: NORTH AMERICA HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 46 BFSI: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 47 BFSI: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 48 BFSI: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 49 BFSI: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 50 BFSI: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 51 BFSI: ROW MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
9.3 IT & TELECOMMUNICATIONS
9.3.1 GROWING NEED FOR HIGH AUTHENTICATION AND DEVICE SECURITY AND RISING DEVELOPMENTS IN 5G INFRASTRUCTURE
TABLE 52 IT & TELECOMMUNICATIONS: NORTH AMERICA HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 53 IT & TELECOMMUNICATIONS: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 54 IT & TELECOMMUNICATIONS: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 55 IT & TELECOMMUNICATIONS: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 56 IT & TELECOMMUNICATIONS: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 57 IT & TELECOMMUNICATIONS: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 58 IT & TELECOMMUNICATIONS: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 59 IT & TELECOMMUNICATIONS: ROW MARKET, BY REGION, 2022–2027 (USD MILLION)
9.4 PUBLIC SECTOR/GOVERNMENT
9.4.1 RISING NEED FOR PROLONGED DATA PROTECTION IRRESPECTIVE OF LOCATION
TABLE 60 PUBLIC SECTOR/GOVERNMENT: NORTH AMERICA HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 61 PUBLIC SECTOR/GOVERNMENT: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 62 PUBLIC SECTOR/GOVERNMENT: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 63 PUBLIC SECTOR/GOVERNMENT: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 64 PUBLIC SECTOR/GOVERNMENT: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 65 PUBLIC SECTOR/GOVERNMENT: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 66 PUBLIC SECTOR/GOVERNMENT: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 67 PUBLIC SECTOR/GOVERNMENT: ROW MARKET, BY REGION, 2022–2027 (USD MILLION)
9.5 INDUSTRIAL MANUFACTURING
9.5.1 ADOPTION OF HARDWARE SECURITY MODULES TO EXCHANGE DATA ACROSS MULTIPLE BUSINESS LEVELS
TABLE 68 INDUSTRIAL MANUFACTURING: NORTH AMERICA MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 69 INDUSTRIAL MANUFACTURING: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 70 INDUSTRIAL MANUFACTURING: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 71 INDUSTRIAL MANUFACTURING: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 72 INDUSTRIAL MANUFACTURING: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 73 INDUSTRIAL MANUFACTURING: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 74 INDUSTRIAL MANUFACTURING: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 75 INDUSTRIAL MANUFACTURING: ROW MARKET, BY REGION, 2022–2027 (USD MILLION)
9.6 ENERGY & POWER
9.6.1 INTEGRATION OF HARDWARE SECURITY MODULES INTO CRITICAL INFRASTRUCTURES TO ENHANCE SECURITY PROTOCOLS
TABLE 76 ENERGY & POWER: NORTH AMERICA HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 77 ENERGY & POWER: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 78 ENERGY & POWER: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 79 ENERGY & POWER: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 80 ENERGY & POWER: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 81 ENERGY & POWER: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 82 ENERGY & POWER: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 83 ENERGY & POWER: ROW MARKET, BY REGION, 2022–2027 (USD MILLION)
9.7 CONSUMER GOODS & RETAIL
9.7.1 HIGH NEED TO SECURE PROPRIETARY INFORMATION
TABLE 84 CONSUMER GOODS & RETAIL: NORTH AMERICA HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 85 CONSUMER GOODS & RETAIL: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 86 CONSUMER GOODS & RETAIL: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 87 CONSUMER GOODS & RETAIL: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 88 CONSUMER GOODS & RETAIL: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 89 CONSUMER GOODS & RETAIL: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 90 CONSUMER GOODS & RETAIL: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 91 CONSUMER GOODS & RETAIL: ROW MARKET, BY REGION, 2022–2027 (USD MILLION)
9.8 MEDICAL & LIFE SCIENCES
9.8.1 RISING NEED TO SHARE DATA ONLY ACROSS TRUSTED PARTNERS AND DEVICES
TABLE 92 MEDICAL & LIFE SCIENCES: NORTH AMERICA MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 93 MEDICAL & LIFE SCIENCES: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 94 MEDICAL & LIFE SCIENCES: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 95 MEDICAL & LIFE SCIENCES: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 96 MEDICAL & LIFE SCIENCES: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 97 MEDICAL & LIFE SCIENCES: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 98 MEDICAL & LIFE SCIENCES: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 99 MEDICAL & LIFE SCIENCES: ROW MARKET, BY REGION, 2022–2027 (USD MILLION)
9.9 AEROSPACE & DEFENSE
9.9.1 INCREASING USE OF HARDWARE SECURITY MODULES TO SAFEGUARD CRITICAL DATA
TABLE 100 AEROSPACE & DEFENSE: NORTH AMERICA HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 101 AEROSPACE & DEFENSE: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 102 AEROSPACE & DEFENSE: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 103 AEROSPACE & DEFENSE: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 104 AEROSPACE & DEFENSE: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 105 AEROSPACE & DEFENSE: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 106 AEROSPACE & DEFENSE: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 107 AEROSPACE & DEFENSE: ROW MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
9.10 TRANSPORTATION
9.10.1 INCREASING ADVANCEMENTS IN CONNECTED CARS
TABLE 108 TRANSPORTATION: NORTH AMERICA HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 109 TRANSPORTATION: NORTH AMERICA MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 110 TRANSPORTATION: EUROPE MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 111 TRANSPORTATION: EUROPE MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 112 TRANSPORTATION: ASIA PACIFIC MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 113 TRANSPORTATION: ASIA PACIFIC MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 114 TRANSPORTATION: ROW MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 115 TRANSPORTATION: ROW MARKET, BY REGION, 2022–2027 (USD MILLION)
10 HARDWARE SECURITY MODULES MARKET, BY REGION (Page No. - 145)
10.1 INTRODUCTION
FIGURE 40 REGIONAL SNAPSHOT: NORTH AMERICAN HARDWARE SECURITY MODULES MARKET TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
FIGURE 41 EUROPE TO DOMINATE MARKET DURING FORECAST PERIOD
TABLE 116 MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 117 MARKET, BY REGION, 2022–2027 (USD MILLION)
10.2 NORTH AMERICA
TABLE 118 NORTH AMERICA: MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 119 NORTH AMERICA: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
FIGURE 42 NORTH AMERICA: SNAPSHOT OF HARDWARE SECURITY MODULES MARKET
10.2.1 US
10.2.1.1 Rising adoption of communication devices to provide high-quality encrypted services
10.2.2 CANADA
10.2.2.1 Rising number of cyberattacks
10.2.3 MEXICO
10.2.3.1 Rising demand for improved network security in automobile manufacturing plants
10.3 EUROPE
TABLE 120 EUROPE: MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 121 EUROPE: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
FIGURE 43 EUROPE: SNAPSHOT OF HARDWARE SECURITY MODULES MARKET
10.3.1 GERMANY
10.3.1.1 High deployment of hardware security modules across connected networks in automotive industry
10.3.2 UK
10.3.2.1 Increasing adoption of advanced interconnected technologies
10.3.3 FRANCE
10.3.3.1 Rising adoption of hardware security modules in aerospace & defense and medical & life sciences verticals
10.3.4 ITALY
10.3.4.1 Growing awareness regarding IT security
10.3.5 NETHERLANDS
10.3.5.1 Increasing digital advancements
10.3.6 RUSSIA
10.3.6.1 Increasing establishment of manufacturing units
10.3.7 REST OF EUROPE
10.4 ASIA PACIFIC
TABLE 122 ASIA PACIFIC: HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 123 ASIA PACIFIC: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
FIGURE 44 ASIA PACIFIC: SNAPSHOT OF MARKET
10.4.1 CHINA
10.4.1.1 Rising number of manufacturing facilities
10.4.2 JAPAN
10.4.2.1 Expanding consumer goods & retail, medical device, and IT & telecommunications verticals
10.4.3 INDIA
10.4.3.1 Rising initiatives to boost foreign direct investments
10.4.4 SOUTH KOREA
10.4.4.1 Surging adoption of hardware security modules in consumer goods & retail vertical
10.4.5 AUSTRALIA
10.4.5.1 High demand for mobile security solutions
10.4.6 REST OF ASIA PACIFIC
10.5 ROW
TABLE 124 ROW: HARDWARE SECURITY MODULES MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 125 ROW: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
10.5.1 SOUTH AMERICA
10.5.1.1 Brazil
10.5.1.1.1 Booming healthcare vertical
10.5.1.2 Argentina
10.5.1.2.1 Government-led initiatives to boost economic growth
10.5.1.3 Rest of South America
10.5.2 MIDDLE EAST & AFRICA
10.5.2.1 Saudi Arabia
10.5.2.1.1 Rising focus on boosting consumer electronics and healthcare verticals
10.5.2.2 United Arab Emirates (UAE)
10.5.2.2.1 Government policies to boost economic growth
10.5.2.3 Rest of Middle East & Africa
11 COMPETITIVE LANDSCAPE (Page No. - 164)
11.1 OVERVIEW
TABLE 126 COMPANIES ADOPTED ACQUISITIONS AND PARTNERSHIPS AS KEY GROWTH STRATEGIES FROM JANUARY 2018 TO JUNE 2022
11.2 MARKET SHARE ANALYSIS
TABLE 127 HARDWARE SECURITY MODULES MARKET: DEGREE OF COMPETITION
TABLE 128 MARKET: MARKET RANKING ANALYSIS
FIGURE 45 MARKET: MARKET SHARE ANALYSIS
11.3 HARDWARE SECURITY MODULES MARKET: REVENUE ANALYSIS, 2019–2021
FIGURE 46 THREE-YEAR REVENUE SNAPSHOT OF KEY COMPANIES
11.4 COMPANY EVALUATION QUADRANT, 2021
11.4.1 STARS
11.4.2 PERVASIVE PLAYERS
11.4.3 EMERGING LEADERS
11.4.4 PARTICIPANTS
FIGURE 47 MARKET: (GLOBAL) COMPANY EVALUATION QUADRANT, 2021
11.5 COMPETITIVE BENCHMARKING
11.5.1 PRODUCT FOOTPRINT (10 COMPANIES)
TABLE 129 TYPE: COMPANY FOOTPRINT (25 COMPANIES)
TABLE 130 DEPLOYMENT TYPE: COMPANY FOOTPRINT (25 COMPANIES)
TABLE 131 REGION: COMPANY FOOTPRINT (25 COMPANIES)
TABLE 132 OVERALL: COMPANY FOOTPRINT (25 COMPANIES)
11.6 STARTUP/SME EVALUATION QUADRANT, 2021
11.6.1 PROGRESSIVE COMPANIES
11.6.2 RESPONSIVE COMPANIES
11.6.3 DYNAMIC COMPANIES
11.6.4 STARTING BLOCKS
FIGURE 48 HARDWARE SECURITY MODULES MARKET: (GLOBAL) STARTUP/SME EVALUATION QUADRANT, 2021
11.7 COMPETITIVE SCENARIOS AND TRENDS
11.7.1 PRODUCT LAUNCHES
TABLE 133 MARKET: PRODUCT LAUNCHES, JANUARY 2018–MARCH 2021
11.7.2 DEALS
TABLE 134 MARKET: DEALS, JANUARY 2018–JUNE 2022
TABLE 135 MARKET: DETAILED LIST OF KEY STARTUPS/SMES
12 COMPANY PROFILES (Page No. - 189)
12.1 KEY COMPANIES
(Business Overview, Products Offered, Recent Developments, MnM view, Key strengths/right to win, Strategic choices made, Weakness/competitive threats)*
12.1.1 THALES
TABLE 136 THALES: COMPANY OVERVIEW
FIGURE 49 THALES: COMPANY SNAPSHOT
TABLE 137 THALES: PRODUCTS OFFERED
TABLE 138 THALES: PRODUCT LAUNCHES
TABLE 139 THALES: DEALS
12.1.2 UTIMACO
TABLE 140 UTIMACO: COMPANY OVERVIEW
TABLE 141 UTIMACO: PRODUCTS OFFERED
TABLE 142 UTIMACO: PRODUCT LAUNCHES
TABLE 143 UTIMACO: DEALS
12.1.3 FUTUREX
TABLE 144 FUTUREX: COMPANY OVERVIEW
TABLE 145 FUTUREX: PRODUCTS OFFERED
TABLE 146 FUTUREX: PRODUCT LAUNCHES
TABLE 147 FUTUREX: DEALS
12.1.4 INFINEON TECHNOLOGIES
TABLE 148 INFINEON TECHNOLOGIES: COMPANY OVERVIEW
FIGURE 50 INFINEON TECHNOLOGIES: COMPANY SNAPSHOT
TABLE 149 INFINEON TECHNOLOGIES: PRODUCTS OFFERED
TABLE 150 INFINEON TECHNOLOGIES: PRODUCT LAUNCHES
TABLE 151 INFINEON TECHNOLOGIES: DEALS
12.1.5 IBM
TABLE 152 IBM: COMPANY OVERVIEW
FIGURE 51 IBM: COMPANY SNAPSHOT
TABLE 153 IBM: PRODUCTS OFFERED
TABLE 154 IBM: DEALS
12.1.6 STMICROELECTRONICS
TABLE 155 STMICROELECTRONICS: COMPANY OVERVIEW
FIGURE 52 STMICROELECTRONICS: COMPANY SNAPSHOT
TABLE 156 STMICROELECTRONICS: PRODUCTS OFFERED
TABLE 157 STMICROELECTRONICS: PRODUCT LAUNCHES
TABLE 158 STMICROELECTRONICS: DEALS
12.1.7 MICROCHIP TECHNOLOGY
TABLE 159 MICROCHIP TECHNOLOGY: COMPANY OVERVIEW
FIGURE 53 MICROCHIP TECHNOLOGY: COMPANY SNAPSHOT
TABLE 160 MICROCHIP TECHNOLOGY: PRODUCTS OFFERED
12.1.8 ATOS SE
TABLE 161 ATOS SE: COMPANY OVERVIEW
FIGURE 54 ATOS SE: COMPANY SNAPSHOT
TABLE 162 ATOS SE: PRODUCTS OFFERED
TABLE 163 ATOS SE: PRODUCT LAUNCHES
TABLE 164 ATOS SE: DEALS
12.1.9 YUBICO
TABLE 165 YUBICO: COMPANY OVERVIEW
TABLE 166 YUBICO: PRODUCTS OFFERED
TABLE 167 YUBICO: PRODUCT LAUNCHES
TABLE 168 YUBICO: DEALS
12.1.10 SWIFT
TABLE 169 SWIFT: COMPANY OVERVIEW
FIGURE 55 SWIFT: COMPANY SNAPSHOT
TABLE 170 SWIFT: PRODUCTS OFFERED
12.2 OTHER PLAYERS
12.2.1 SECUROSYS
TABLE 171 SECUROSYS: COMPANY OVERVIEW
12.2.2 SPYRUS
TABLE 172 SPYRUS: COMPANY OVERVIEW
12.2.3 LEDGER
TABLE 173 LEDGER: COMPANY OVERVIEW
12.2.4 ULTRA ELECTRONICS
TABLE 174 ULTRA ELECTRONICS: COMPANY OVERVIEW
12.2.5 ADWEBTECH
TABLE 175 ADWEBTECH: COMPANY OVERVIEW
12.2.6 EFFICIENT INDIA
TABLE 176 EFFICIENT INDIA: COMPANY OVERVIEW
12.2.7 LATTICE SEMICONDUCTORS
TABLE 177 LATTICE SEMICONDUCTORS: COMPANY OVERVIEW
12.2.8 ELLIPTICSECURE
TABLE 178 ELLIPTICSECURE: COMPANY OVERVIEW
12.2.9 AMAZON INC.
TABLE 179 AMAZON INC.: COMPANY OVERVIEW
12.2.10 ENTRUST SECURITY
TABLE 180 ENTRUST SECURITY: COMPANY OVERVIEW
12.2.11 ESCRYPT
TABLE 181 ESCRYPT: COMPANY OVERVIEW
12.2.12 SANSEC TECHNOLOGY
TABLE 182 SANSEC TECHNOLOGY: COMPANY OVERVIEW
12.2.13 FORTANIX
TABLE 183 FORTANIX: COMPANY OVERVIEW
12.2.14 JISA SOFTECH
TABLE 184 JISA SOFTECH: COMPANY OVERVIEW
12.2.15 MICROSOFT
TABLE 185 MICROSOFT: COMPANY OVERVIEW
*Details on Business Overview, Products Offered, Recent Developments, Deals, MnM view, Key strengths/right to win, Strategic choices made, Weakness/competitive threats might not be captured in case of unlisted companies.
13 APPENDIX (Page No. - 242)
13.1 INSIGHTS FROM INDUSTRY EXPERTS
13.2 DISCUSSION GUIDE
13.3 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
13.4 CUSTOMIZATION OPTIONS
13.5 RELATED REPORTS
13.6 AUTHOR DETAILS
The study involved four major activities in estimating the size of the hardware security module market. Exhaustive secondary research has been done to collect information on the market, peer market, and parent market. Validation of these findings, assumptions, and sizing with industry experts across the value chain through primary research has been the next step. Both top-down and bottom-up approaches have been employed to estimate the global market size. After that, market breakdown and data triangulation have been used to estimate the market sizes of segments and subsegments.
Secondary Research
The secondary sources referred to for this research study includes These secondary sources include biometric technologies journals and magazines, IEEE journals; annual reports, press releases, and investor presentations of companies; white papers; certified publications and articles from recognized authors; and directories and databases such as Factiva, Hoovers, and OneSource.
Secondary research has been conducted to obtain key information about the supply chain of the hardware security module industry, the monetary chain of the market, the total pool of key players, and market segmentation according to the industry trends to the bottommost level, regional markets, and key developments from both market- and technology oriented perspectives. The secondary data has been collected and analyzed to arrive at the overall market size, which has further been validated by primary research.
Primary Research
Extensive primary research has been conducted after acquiring an understanding of the hardware security module market scenario through secondary research. Several primary interviews have been conducted with market experts from both the demand- (consumers, industries) and supply-side (hardware security module providers) players across four major regions, namely, North America, Europe, Asia Pacific, and the Rest of the World (the Middle East & Africa). Approximately 75% and 25% of primary interviews have been conducted from the supply and demand side, respectively. Primary data has been collected through questionnaires, emails, and telephonic interviews. In the canvassing of primaries, various departments within organizations, such as sales, operations, and administration, were covered to provide a holistic viewpoint in our report.
After interacting with industry experts, brief sessions were conducted with highly experienced independent consultants to reinforce the findings from our primaries. This, along with the in-house subject matter experts’ opinions, has led us to the findings as described in the remainder of this report.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Both top-down and bottom-up approaches have been used to estimate and validate the total size of the hardware security module market. These methods have also been extensively used to estimate the sizes of various market subsegments. The research methodology used to estimate the market sizes includes the following:
- Identifying various applications that use or are expected to use the hardware security module market.
- Analyzing historical and current data pertaining to the size of the hardware security module market for each application
- Analyzing the average selling prices of hardware security modules based on different technologies
- Studying various paid and unpaid sources, such as annual reports, press releases, white papers, and databases
- Identifying leading providers of hardware security module, studying their portfolios, and understanding features of their products and their underlying technologies, as well as the types of hardware security module products offered
- Tracking ongoing and identifying upcoming developments in the market through investments, research and development activities, product launches, expansions, and partnerships, and forecasting the market size based on these developments and other critical parameters
- Carrying out multiple discussions with key opinion leaders to understand the technologies used in hardware security module, and products wherein they are deployed, and analyze the break-up of the scope of work carried out by key manufacturers of hardware security module solutions providers
- Verifying and crosschecking estimates at every level through discussions with key opinion leaders, such as CXOs, directors, and operations managers, and finally with domain experts at MarketsandMarkets
Market Size Estimation Methodology-Bottom-up approach

Data Triangulation
After arriving at the overall market size-using the market size estimation processes explained above-the market has been split into several segments and subsegments. To complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, data triangulation, and market breakdown procedures have been employed, wherever applicable. The data has been triangulated by studying various factors and trends from both the demand and supply sides.
The main objectives of this study are as follows:
- To define, describe, segment, and forecast the hardware security module market, in terms of value, based on deployment type, type, applications, verticals, and geography.
- To forecast the size of the market and its segments with respect to four main regions, namely, North America, Europe, Asia Pacific (APAC), and the Rest of the World (RoW), along with their key countries
- To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and contributions to the total market
- To provide detailed information regarding the key factors influencing market growth, such as drivers, restraints, opportunities, and challenges
- To provide a detailed analysis of the hardware security module supply chain
- To analyze the opportunities in the market for stakeholders and provide a detailed competitive landscape of the market leaders
- To strategically profile the key players and comprehensively analyze their market ranking and core competencies2
- To analyze key growth strategies such as expansions, contracts, joint ventures, acquisitions, product launches and developments, and research and development activities undertaken by players operating in the hardware security module market.
Available Customizations:
MarketsandMarkets offers the following customizations for this market report:
- Further breakdown of the market in different regions to the country-level
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...







Growth opportunities and latent adjacency in Hardware Security Modules Market