Industrial Cybersecurity Market by Security Type (Network, Endpoint, Application, Cloud, Wireless), Offering (Products and Services), End-user (Power, Utilities, Transportation, Chemicals & Manufacturing) and Region (2022-2027)
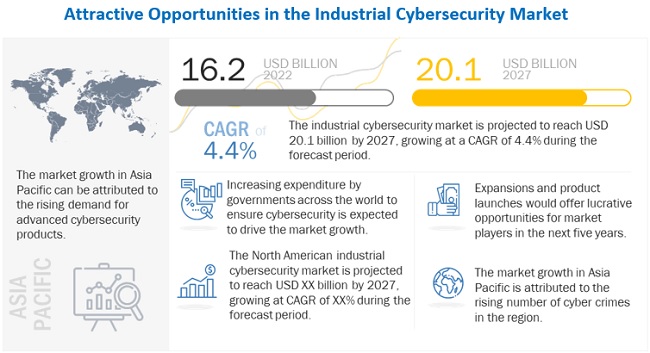
The global industrial cybersecurity market in terms of revenue was estimated to be worth USD 16.2 billion in 2022 and is poised to reach USD 20.1 billion by 2027, growing at a CAGR of 4.4% from 2022 to 2027. The new research study consists of an industry trend analysis of the market.
To know about the assumptions considered for the study, Request for Free Sample Report
COVID-19 impact on global Industrial cybersecurity market, in 2022
The pandemic hit the global economy at large during the start of 2020 and has created unprecedented turmoil and change for individuals and organizations across the world. The pandemic has led to the closure of workplaces, restrictions on travel, and the creation of the work-from-home option for almost all employees, which has created challenges for businesses to operate. In the realistic approach, it has been assumed that the first three-quarters of FY 20–21 have witnessed low growth in the industrial cybersecurity market, followed by a steady recovery during the last quarter of FY 20–21. In the most realistic scenario, the industrial cybersecurity industry is expected to grow at a CAGR of 11.6% during 2022–2027. The market is expected to witness a single-digit growth in FY 20–21 due to the COVID-19 pandemic.
Industrial Cybersecurity Market Dynamics
Driver: Increasing focus on integrating IoT into industrial control systems
The IoT has brought great convenience in executing complex tasks and simplified the lives of millions of people. It offers modern industries a new way to manage, store, and process data in the cloud and data centers. With the adoption of IoT technologies, industrial organizations can extract more meaningful information from a large volume of data generated in their facilities.
In 2021, the number of global IoT connections was 13.8 billion, and this number is expected to reach 39.0 billion by 2027. Smart devices have revolutionized the way customers, enterprises, and communication service providers interact with each other. They have enabled the automation and agility of different business processes. The increased smartphone penetration across the world has led to a rise in the number of interconnected devices using multiple platforms. These devices are connected to each other through wireless cellular and non-cellular networks such as Zigbee, Bluetooth, 3G, 4G, and upcoming 5G. These connected devices are instrumental in ensuring that the data is continuously tracked to understand the deviation in the standard operating processes (SOPs).
Restraint: Underestimation of threat levels and misunderstanding of nature of threats
The industrial control system has been continuously evolving and has started including a wide range of interconnected devices that help the industry workforce to understand and analyze the operational environment. However, it also puts the system in danger of cyberattacks. Owing to the relative rarity of targeted attacks against automation systems and the excessive reliance on safety measures, owners of industrial enterprises and their staff underestimate the existing and upcoming probable threats in the ICS environment.
Similarly, over the past few years, security technologies have developed extensively to catch up on offensive cyber capabilities. To analyze and design a security system, developers always try to stay ahead of the attackers, but security products and associated technologies are generally designed by analyzing the historical threats, which generally do not include all details of operational technologies (OTs). Thus, industrial control systems are designed to protect against synthetic attacks. Consequently, security products and software solutions are designed without imaging or considering potential threats or the nature of future attacks and without a thorough analysis and scrutiny of a day-to-day threat landscape. As a result, real-world threats are underestimated.
Opportunity: Growing focus of government organizations on releasing rules and regulations for security of industrial control systems
Several government organizations such as the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) and the National Institute of Standards and Technology (NIST) are continuously releasing security guidelines, rules and regulations, and standards for the security of industrial control systems. NIST has also introduced many security standards and guidelines that are commonly used to secure traditional IT systems.
Some most prominent security standards applicable for industrial control systems are the ISA/IEC 62443 and the NIST SP 800-82. NCCIC and ICS-CERT save control system environments from emerging cyber threats. The Department of Homeland Security (DHS) and ICS-CERT have incorporated the Industrial Control Systems Joint Working Group (ICSJWG) to enable information sharing and reduce threats related to industrial systems. Additionally, the United States Computer Emergency Readiness Team (US-CERT), an organization of DHS, is responsible for analyzing and reducing cyber threats and vulnerabilities, disseminating cyber threat warning information, and coordinating incident response activities.
Challenge: Lack of awareness about best practices and criticality of cybersecurity in industrial control systems
The industrial sector implements modern security technologies to prevent cyberattacks, but attackers develop new techniques and procedures to infiltrate these technologies. Investments in security defense and detection technologies help develop effective defense strategies; however, human errors are one of the key reasons for most breaches.
These errors take place due to the lack of awareness among employees, which is putting the industrial sector at risk. Advanced cyber threats that are diverse in nature target particular vulnerabilities in networks and use these vulnerabilities to get an entry into enterprise networks. Advanced cyber threats have significantly increased over the last few years and have become a major security concern for the industrial sector.
In addition to implementing appropriate hardware and software-based protection tools, employee training should also be considered equally critical to completely secure industrial facilities from cyberattacks or cyber threats. Every employee who is a part of an organization poses a threat to the security in case of non-awareness of the associated risks. This makes cybersecurity training a critical factor for professionals to understand, identify, and avoid future threats before escalation. Training will also allow the workforce to practice safe business duties at the workplace. The figure provided below indicates some most sophisticated attacks on the ICS network.
The market for power expected to hold the largest market share in Industrial cybersecurity market, by verticals, in 2027
Power companies are increasingly adopting cybersecurity solutions and upgrading their cybersecurity capabilities to protect their industrial systems from rapidly evolving cyber threats. Cybersecurity in power companies helps in mitigating the challenges pertaining to aging grid infrastructure, monitoring power system operations, maintaining the balance between power generation and production, and providing fast and efficient ways to restore services after interruptions. The importance of monitoring systems has increased with the growing use of renewable sources in power grids.
Industrial Cybersecurity Market Segment Overview
The market for the products to grow at the highest CAGR during the forecast period
Cyberattacks and threats against critical infrastructure have increased over the years due to the growing use of connected devices and IT systems. Instead of stealing data, digital attackers target to access industrial control systems, such as SCADA, DCS, and PLC, on which organizations rely for managing their industrial processes. Industries such as pharmaceuticals, oil & gas, manufacturing, and electric utilities use control systems. These systems are connected with a large number of sensors with the help of network infrastructure (either wired or wireless systems). Any alteration in control network infrastructure by infrastructure industries to meet their business needs might lead to an increase in cyberattacks.
The industrial cybersecurity market for products has been broadly segmented into gateways and networking devices. Gateways help prevent cyberattacks on SCADA systems by allowing them to connect with management information systems securely. Gateways help manage network user access by directly accessing the networks in the industrial zone. Furthermore, networking devices are further classified into routers and industrial Ethernet switches.
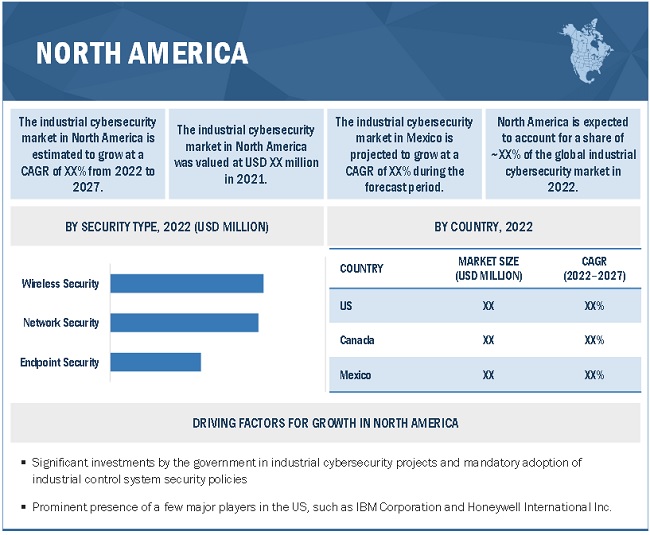
North America to hold the largest share of Industrial cybersecurity market in 2022
The industrial cybersecurity market in North America, based on country, has been segmented into the US, Canada, and Mexico. This region is a major market for industrial cybersecurity solutions and services as it is home to a few of the largest multinational companies, such as IBM Corporation (US); Cisco Systems, Inc. (US); Honeywell International Inc.(US); Fortinet (US); Splunk (US), Broadcom INC. (US); Fireeye (US); Proofpoint (US); Microsoft (US); Palo Alto Networks (US); and Dell, Inc. (US).
To know about the assumptions considered for the study, download the pdf brochure
Key Players in Industrial Cybersecurity Industry:
A few key industrial cybersecurity companies are IBM (US), Honeywell International (US), ABB Ltd. (Switzerland), Schneider Electric (France), CISCO (US), and Rockwell Automation (US) are among a few key players in this market.
Industrial Cybersecurity Market Report Scope:
|
Report Metric |
Details |
| Estimated Market Size | USD 16.2 billion in 2022 |
| Projected Market Size | USD 20.1 billion by 2027 |
| Growth Rate | CAGR of 4.4% |
|
Market size available for years |
2018–2027 |
|
Base year |
2021 |
|
Forecast period |
2022–2027 |
|
Units |
Value USD Million |
|
Segments covered |
Offering, Security Type, End-user Industry, and Region. |
|
Geographic regions covered |
North America, APAC, Europe, and RoW |
|
Companies covered |
The companies covered in the industrial cybersecurity market are IBM (US), Honeywell International (US), ABB LTD. (Switzerland), Schneider Electric (France), CISCO Systems (US), McAfee Corporation (US), Siemens (Germany), Dell Technologies Inc. (US), NortonLifeLock Inc. (US), Rockwell Automation (US). The other company profiles included in the scope are Kaspersky Lab (Russia), Fortinet (US), Palo Alto Network (US), Proofpoint (US), Trend Micro (Japan), Splunk Technology (US), Broadcom Inc. (US), Microsoft Corporation (US), Opswat (US), Dragos Inc. (US), Upstream Security (Israel), Cylus (Israel), Argus Cyber Security (Israel), Cyberark (US), Forescout Technologies Inc (US). |
This report categorizes the industrial cybersecurity market based on security type, offering, end-user industry, and region.AI in Computer Vision Market.
Industrial cybersecurity Market, By Security Type
- Network Security
- Endpoint Security
- Application Security
- Cloud Security
- Wireless Security
- Others
Market, By Offering
- Products
- Solutions & Services
Market, By End-User Industry
- Power
- Utilities
- Transportation
- Chemicals & Manufacturing
- Others
Geographic Analysis
- Introduction
-
North America
- US
- Canada
- Mexico
-
Europe
- UK
- Germany
- France
- Italy
- Netherlands
- Rest of Europe (RoE)
-
Asia Pacific (APAC)
- China
- Japan
- India
- South Korea
- Rest of APAC (RoAPAC)
-
Rest of the World (RoW)
- South America
- Middle East & Africa
Recent Developments in Industrial Cybersecurity
- In August 2022, IBM Corporation launched the Secure Access Service Edge (SASE) solution designed to help organizations adopt cloud-delivered security at the edge, closer to users and devices accessing corporate resources. With SASE, software-defined networking and network security technologies are bundled into a single, cloud-based service.
- In January 2022, Honeywell International Inc. and Acalvio Technologies (US) teamed up to launch HTDP, a platform designed to detect known and unknown cyberattacks across the OT environments in commercial buildings. The sophisticated, active defense system features autonomous deception tactics to outsmart attackers and provides high-fidelity threat detection.
- In March 2022, ABB Ltd. (Switzerland) partnered with Nozomi Networks (US), a leading provider of OT and IoT security and visibility solutions, to fulfill the growing demand for improved OT cybersecurity solutions from the energy, process, and hybrid industries. This acquisition enabled ABB to integrate Nozomi Networks’ advanced solutions for operational resiliency and real-time network visibility to assist ABB’s global automation and digitalization customers.
Frequently Asked Questions (FAQ):
What is current size of global Industrial cybersecurity market?
The global Industrial cybersecurity market is estimated to be around USD 16.2 billion in 2022 and projected to reach USD 20.1 billion by 2027 at a CAGR of 4.4%.
What is COVID-19 impact on global Industrial cybersecurity market?
The global lockdowns and shutdowns have indirectly affected the industrial cybersecurity market. It is expected that it will take approximately 2–3 years for all the process industries to recover from the adverse effect of the pandemic and another 1–2 years for the market to recover with an organized supply and demand chain.
In this scenario, it is assumed that all measures, both health and economic, would neither help control the spread of the virus nor lead to economic recovery. Most economies would experience an unprecedented economic loss, social and political turmoil recession until the third quarter of 2022, and modest recovery starting in Q4 of 2022. This is likely to be an L-shaped economic recovery, with countries taking longer to return to their pre-crisis levels. The industrial cybersecurity market is expected to recover at a gradual pace in the coming 2–3 years and at an accelerated pace thereafter.
Where will all these developments take the industry in the mid-to-long term?
Technology will continue to play a critical role in the Industrial cybersecurity ecosystem. Key players operating in the Industrial cybersecurity marketplace are integrating emerging technologies within their existing ecosystem, which has helped to improve Industrial cybersecurity services.
Who are the winners of global Industrial cybersecurity market?
Companies such as IBM (US), Honeywell International (US), ABB Ltd (Switzerland), Schneider Electric (France), CISCO (US), and Controlant (Iceland) are among a few key players in this market.
What are some features of industrial cybersecurity?
Industrial cybersecurity refers to the safety and security of industrial control systems, automation processes, plant operations, and critical infrastructure from cyber intrusions. Industrial control systems, including programmable logic controllers (PLCs), distributed control systems (DCS), and supervisory control and data acquisition (SCADA) systems, are primarily prone to cyberattacks. To secure these systems from cyberattacks, various technologies, such as distributed denial of service (DDoS), firewall, intrusion detection and prevention systems, antivirus software solutions, and products such as gateways and networking devices are used to ensure uninterrupted productivity of utilities, grids, transportation systems, and the manufacturing sector. .
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
TABLE OF CONTENTS
1 INTRODUCTION (Page No. - 26)
1.1 STUDY OBJECTIVES
1.2 MARKET DEFINITION
1.3 STUDY SCOPE
1.3.1 MARKETS COVERED
1.3.2 GEOGRAPHIC SCOPE
1.3.3 GENERAL INCLUSIONS AND EXCLUSIONS
1.3.4 INCLUSIONS AND EXCLUSIONS AT COMPANY LEVEL
1.3.5 INCLUSIONS AND EXCLUSIONS AT OFFERING LEVEL
1.3.6 INCLUSIONS AND EXCLUSIONS AT END-USER INDUSTRY LEVEL
1.3.7 INCLUSIONS AND EXCLUSIONS AT REGIONAL LEVEL
1.3.8 YEARS CONSIDERED
1.4 CURRENCY
1.5 PACKAGE SIZE
1.6 LIMITATIONS
1.7 STAKEHOLDERS
1.8 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY (Page No. - 32)
2.1 RESEARCH DATA
2.1.1 SECONDARY DATA
2.1.1.1 List of major secondary sources
2.1.1.2 Key data from secondary sources
2.1.2 PRIMARY DATA
2.1.2.1 Key data from primary sources
2.1.2.2 Key industry insights
2.1.2.3 Breakdown of primaries
2.1.3 SECONDARY AND PRIMARY RESEARCH
2.2 MARKET SIZE ESTIMATION
2.2.1 BOTTOM-UP APPROACH
2.2.1.1 Approach for capturing market size by bottom-up analysis (demand side)
2.2.2 TOP-DOWN APPROACH
2.2.2.1 Approach for capturing market size by top-down analysis
2.3 DEMAND- AND SUPPLY-SIDE APPROACH ANALYSES
2.3.1 INDUSTRIAL CYBERSECURITY MARKET: SUPPLY-SIDE ANALYSIS
2.4 MARKET BREAKDOWN AND DATA TRIANGULATION
2.5 RESEARCH ASSUMPTIONS
3 EXECUTIVE SUMMARY (Page No. - 42)
4 PREMIUM INSIGHTS (Page No. - 47)
4.1 ATTRACTIVE OPPORTUNITIES IN INDUSTRIAL CYBERSECURITY MARKET
4.2 INDUSTRIAL CYBERSECURITY MARKET, BY END-USER INDUSTRY AND REGION, 2022
4.3 INDUSTRIAL CYBERSECURITY MARKET, BY OFFERING
4.4 INDUSTRIAL CYBERSECURITY MARKET, BY SECURITY TYPE
4.5 INDUSTRIAL CYBERSECURITY MARKET, BY REGION
5 MARKET OVERVIEW (Page No. - 50)
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
5.2.1 DRIVERS
5.2.1.1 Rising investments by governments and private organizations worldwide to create safe and secure industrial environment
5.2.1.2 Growing number of sophisticated cyberattacks on critical industrial infrastructure
5.2.2 RESTRAINTS
5.2.2.1 Underestimation of threat levels and misunderstanding of nature of threats
5.2.2.2 Lack of adequate funds, framework, and governance required to develop high-end cybersecurity solutions
5.2.3 OPPORTUNITIES
5.2.3.1 Rising importance of cloud-based industrial cybersecurity services
5.2.3.2 Growing focus of government organizations on releasing rules and regulations for security of industrial control systems
5.2.4 CHALLENGES
5.2.4.1 Lack of awareness about best practices and criticality of cybersecurity in industrial control systems
5.3 PRICING ANALYSIS
5.3.1 INDUSTRIAL ROUTERS
5.4 VALUE CHAIN ANALYSIS
5.4.1 INDUSTRIAL CYBERSECURITY MARKET
5.5 PORTER’S FIVE FORCES ANALYSIS
5.5.1 THREAT OF NEW ENTRANTS
5.5.2 THREAT OF SUBSTITUTES
5.5.3 BARGAINING POWER OF SUPPLIERS
5.5.4 BARGAINING POWER OF BUYERS
5.5.5 INTENSITY OF COMPETITION RIVALRY
5.6 KEY STAKEHOLDERS AND BUYING CRITERIA
5.6.1 KEY STAKEHOLDERS IN BUYING PROCESS
5.6.2 BUYING CRITERIA
5.7 KEY CONFERENCES AND EVENTS IN 2022–2023
5.8 INDUSTRIAL CYBERSECURITY MARKET: ECOSYSTEM
5.9 PATENT ANALYSIS
5.10 TRADE ANALYSIS
5.11 TARIFF AND REGULATORY LANDSCAPE
5.11.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
5.12 CASE STUDIES
5.12.1 POWER AND WATER INDUSTRY
5.12.2 MINING INDUSTRY
5.13 TECHNOLOGICAL TRENDS IN INDUSTRIAL CYBERSECURITY
5.13.1 ZERO-TRUST FRAMEWORK
5.13.2 POTENTIAL OF ARTIFICIAL INTELLIGENCE AND MACHINE LEARNING
5.13.3 SECURITY FOR CLOUD-NATIVE ENVIRONMENTS
5.14 CODES AND STANDARDS RELATED TO INDUSTRIAL CYBERSECURITY
5.15 KEY STAKEHOLDERS AND BUYING CRITERIA
5.15.1 TRENDS/DISRUPTIONS IMPACTING CUSTOMER’S BUSINESS
5.15.1.1 Revenue shift and new revenue pockets for cybersecurity service providers
6 INDUSTRIAL CYBERSECURITY MARKET, BY SECURITY TYPE (Page No. - 81)
6.1 INTRODUCTION
6.2 NETWORK SECURITY
6.2.1 EXPOSURE OF GOVERNMENT ORGANIZATIONS AND PRODUCTION FACILITIES TO UNAUTHORIZED NETWORK ACCESS TRIGGERS MARKET GROWTH OF NETWORK SECURITY
6.3 ENDPOINT SECURITY
6.3.1 ENDPOINT SECURITY ASSURES PROTECTION OF IT AND OT INFRASTRUCTURE THAT INCLUDES ENDPOINTS AND REMOTE DEVICES FROM CYBER THREATS
6.4 APPLICATION SECURITY
6.4.1 INCREASED PRESENCE OF CLOUD-CONNECTED NETWORKS CREATES NEED FOR APPLICATION SECURITY TO PROTECT THEM FROM CYBERATTACKS AND DATA BREACH ISSUES
6.5 CLOUD SECURITY
6.5.1 ADOPTION OF SAAS APPLICATION ACCELERATES NEED FOR CLOUD SECURITY SOLUTIONS
6.6 WIRELESS SECURITY
6.6.1 STRONG FOCUS ON PREVENTION OF DATA THEFT ACROSS WIRELESS NETWORKS TO INCREASE NEED FOR WIRELESS SECURITY
6.7 OTHERS
7 INDUSTRIAL CYBERSECURITY MARKET, BY OFFERING (Page No. - 121)
7.1 INTRODUCTION
7.2 PRODUCTS
7.2.1 GATEWAYS
7.2.1.1 Gateways help provide cybersecurity to industrial control systems
7.2.2 NETWORKING DEVICES
7.2.2.1 Routers
7.2.2.1.1 Conventional routers will be replaced with advanced technology-based routers
7.2.2.2 Industrial Ethernet switches
7.2.2.2.1 Industrial Ethernet switches offer industry-grade reliability, network redundancy, and enhanced security
7.3 SOLUTIONS & SERVICES
7.3.1 SOLUTIONS
7.3.1.1 Antivirus/malware
7.3.1.1.1 Antivirus/malware segment to hold largest share of solutions market in 2027
7.3.1.2 Firewall
7.3.1.2.1 Working via VPN during COVID-19 heightened requirement for firewall solutions
7.3.1.2.1.1 Proxy firewall
7.3.1.2.1.2 Packet-filtering firewall
7.3.1.2.1.3 Stateful inspection firewall
7.3.1.2.1.4 Next-generation firewall (NGFW)
7.3.1.3 SCADA encryption
7.3.1.3.1 SCADA encryption helps mitigate common attacks
7.3.1.4 Virtualization security
7.3.1.4.1 Demand for virtualization security expected to increase during forecast period
7.3.1.5 Data loss prevention (DLP)
7.3.1.5.1 DLP solutions to have huge demand in post-pandemic situation
7.3.1.6 Security information and event management (SIEM)
7.3.1.6.1 SIEM provides centralized combined system
7.3.1.7 Intrusion detection system/intrusion prevention system
7.3.1.7.1 IDS/IPS technologies to help in detecting suspicious activities
7.3.1.8 Identity and access management (IAM)
7.3.1.8.1 IAM helps provide secure remote access
7.3.1.9 Unified threat management (UTM)
7.3.1.9.1 UTM allows network operators to monitor and control security-related applications
7.3.1.10 Distributed denial of service (DDoS)
7.3.1.10.1 Increasing DDOS attacks to heighten need for DDOS
7.3.1.11 Others
7.3.1.11.1 Application whitelisting
7.3.1.11.2 Update and patch management
7.3.1.11.3 Database activity monitoring (DAM)
7.3.2 SERVICES
7.3.2.1 Managed services
7.3.2.1.1 Managed services help companies with critical infrastructure to gain complete visibility and control over systems that are part of network infrastructure
7.3.2.2 Professional Services
7.3.2.2.1 Professional services to dominate market from 2022 to 2027
7.3.2.2.1.1 Risk management services (RMS)
7.3.2.2.1.2 Companies such as Sword and Shield Enterprise Security, Inc. (US) and Thales S.A. (France) provide risk management and assessment services to industries having critical infrastructure. Audit and reporting services
7.3.2.2.1.3 Design, integration, and consulting services
8 INDUSTRIAL CYBERSECURITY MARKET, BY END-USER INDUSTRY (Page No. - 145)
8.1 INTRODUCTION
8.2 POWER
8.2.1 POWER SECTOR EXPECTED TO HOLD LARGEST MARKET SHARE IN 2027
8.2.1.1 Power generation
8.2.1.2 Nuclear power plants
8.2.1.3 Thermal and hydropower plants
8.2.1.4 Renewable energy power plants
8.2.1.5 Power grid
8.3 UTILITIES
8.3.1 UTILITIES SECTOR TO WITNESS HIGH DEMAND FOR INDUSTRIAL CYBERSECURITY PRODUCTS OWING TO RISING NUMBER OF CYBER CRIMES
8.3.1.1 Oil and gas pipelines
8.3.1.2 Electric power transmission
8.3.1.3 Water treatment and distribution
8.3.1.4 Wastewater collection and treatment
8.4 TRANSPORTATION
8.4.1 TRANSPORTATION INDUSTRY TO WITNESS HIGHEST CAGR IN INDUSTRIAL CYBERSECURITY MARKET DUE TO INCREASED NUMBER OF CYBERATTACKS
8.4.1.1 Airports
8.4.1.2 Seaports
8.4.1.3 Railways
8.4.1.4 Others
8.5 CHEMICALS AND MANUFACTURING
8.5.1 URGENT NEED TO PROTECT INDUSTRIAL CONTROL SYSTEMS PROPELS GROWTH OF INDUSTRIAL CYBERSECURITY MARKET
8.5.1.1 Automated production units
8.5.1.2 Refining plants
8.5.1.3 Mining units
8.6 OTHERS
9 GEOGRAPHIC ANALYSIS (Page No. - 167)
9.1 INTRODUCTION
9.2 NORTH AMERICA
9.2.1 US
9.2.1.1 US to hold major share of industrial cybersecurity in 2027
9.2.2 CANADA
9.2.2.1 Canada to witness high demand for industrial cybersecurity products and services owing to rising adoption of digital technologies by business owners
9.2.3 MEXICO
9.2.3.1 Mexican market growth is driven by implementation of wireless connectivity devices in industrial plants
9.3 EUROPE
9.3.1 UK
9.3.1.1 Rising number of active cybersecurity firms in UK to create opportunities for market growth
9.3.2 GERMANY
9.3.2.1 Growing adoption of industrial cybersecurity solutions by private and government organizations to ensure data privacy
9.3.3 FRANCE
9.3.3.1 Increasing demand for data security solutions from defense sector to fuel industrial cybersecurity market growth
9.3.4 ITALY
9.3.4.1 Increasing number of cybercrimes prompts use of industrial cybersecurity solutions in Italy
9.3.5 NETHERLANDS
9.3.5.1 Growing number of digital attacks to create strong need for cybersecurity products
9.3.6 REST OF EUROPE
9.4 ASIA PACIFIC
9.4.1 CHINA
9.4.1.1 Growing implementation of latest technologies in industrial plants to boost demand for industrial cybersecurity products
9.4.2 JAPAN
9.4.2.1 Rising technological advancements in Japan will force country to follow industrial cybersecurity measures
9.4.3 INDIA
9.4.3.1 Increasing number of crimes prompts country to install industrial cybersecurity solutions
9.4.4 SOUTH KOREA
9.4.4.1 Surging penetration of computer networks to propel growth of industrial cybersecurity market
9.4.5 REST OF ASIA PACIFIC
9.5 REST OF THE WORLD (ROW)
9.5.1 MIDDLE EAST AND AFRICA (MEA)
9.5.1.1 Cybersecurity spending by governments increased due to growing vulnerability of critical infrastructure to cyber threats
9.5.2 SOUTH AMERICA
9.5.2.1 Demand for cybersecurity solutions during forecast period would increase with rising number of cyberattacks in oil & gas and transportation sectors
10 COMPETITIVE LANDSCAPE (Page No. - 201)
10.1 INTRODUCTION
10.2 KEY PLAYER STRATEGIES/RIGHT TO WIN
10.2.1 OVERVIEW OF STRATEGIES ADOPTED BY KEY PLAYERS IN INDUSTRIAL CYBERSECURITY MARKET
10.3 MARKET SHARE ANALYSIS
10.4 REVENUE ANALYSIS
10.4.1 INDUSTRIAL CYBERSECURITY MARKET
10.5 COMPANY EVALUATION QUADRANT
10.5.1 INDUSTRIAL CYBERSECURITY MARKET
10.5.1.1 Star
10.5.1.2 Emerging leader
10.5.1.3 Pervasive
10.5.1.4 Participant
10.6 COMPETITIVE BENCHMARKING
10.6.1 STARTUP/SMALL AND MEDIUM-SIZED ENTERPRISES (SME) EVALUATION MATRIX
10.6.1.1 Progressive company
10.6.1.2 Responsive company
10.6.1.3 Dynamic company
10.6.1.4 Starting block
10.7 COMPETITIVE SCENARIO AND TRENDS
10.7.1 INDUSTRIAL CYBERSECURITY
10.7.1.1 Product Launches and developments
10.7.1.2 Deals
10.7.1.3 Others
11 COMPANY PROFILES (Page No. - 226)
11.1 KEY PLAYERS
11.1.1 INTERNATIONAL BUSINESS MACHINES (IBM) CORPORATION
11.1.1.1 Business overview
11.1.1.2 Products/solutions/services offered
11.1.1.3 Recent developments
11.1.1.4 MnM view
11.1.1.4.1 Key strengths/right to win
11.1.1.4.2 Strategic choices made
11.1.1.4.3 Weaknesses and competitive threats
11.1.2 HONEYWELL INTERNATIONAL INC.
11.1.2.1 Business overview
11.1.2.2 Products/solutions/services offered
11.1.2.3 Recent developments
11.1.2.4 MnM view
11.1.2.4.1 Key strengths/right to win
11.1.2.4.2 Strategic choices made
11.1.2.4.3 Weaknesses and competitive threats
11.1.3 ABB LTD.
11.1.3.1 Business overview
11.1.3.2 Products offered
11.1.3.3 Recent developments
11.1.3.4 MnM view
11.1.3.4.1 Key strengths/right to win
11.1.3.4.2 Strategic choices made
11.1.3.4.3 Weaknesses and competitive threats
11.1.4 CISCO SYSTEMS, INC.
11.1.4.1 Business overview
11.1.4.2 Products offered
11.1.4.3 Recent developments
11.1.4.4 MnM view
11.1.4.4.1 Key strengths/Right to win
11.1.4.4.2 Strategic choices made
11.1.4.4.3 Weaknesses and competitive threats
11.1.5 SCHNEIDER ELECTRIC
11.1.5.1 Business overview
11.1.5.2 Products offered
11.1.5.3 Recent developments
11.1.5.4 MnM view
11.1.5.4.1 Key strengths/right to win
11.1.5.4.2 Strategic choices made
11.1.5.4.3 Weaknesses and competitive threats
11.1.6 MCAFEE CORPORATION
11.1.6.1 Business overview
11.1.6.2 Products offered
11.1.6.3 Recent developments
11.1.7 SIEMENS
11.1.7.1 Business overview
11.1.7.2 Products offered
11.1.7.3 Recent developments
11.1.8 DELL TECHNOLOGIES INC.
11.1.8.1 Business overview
11.1.8.2 Products offered
11.1.8.3 Recent developments
11.1.9 NORTONLIFELOCK INC.
11.1.9.1 Business overview
11.1.9.2 Products offered
11.1.9.3 Recent developments
11.1.10 ROCKWELL AUTOMATION INC.
11.1.10.1 Business overview
11.1.10.2 Products offered
11.2 OTHER PLAYERS
11.2.1 KASPERSKY LAB
11.2.2 FORTINET
11.2.3 PALO ALTO NETWORK
11.2.4 PROOFPOINT
11.2.5 TREND MICRO
11.2.6 SPLUNK TECHNOLOGY
11.2.7 BROADCOM INC.
11.2.8 MICROSOFT CORPORATION
11.2.9 FORESCOUT TECHNOLOGIES INC.
11.2.10 OPSWAT
11.2.11 DRAGOS INC.
11.2.12 CYBERARK
11.2.13 ARGUS CYBER SECURITY
11.2.14 CYLUS
11.2.15 UPSTREAM SECURITY
12 APPENDIX (Page No. - 282)
12.1 DISCUSSION GUIDE
12.2 KNOWLEDGE STORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
12.3 AVAILABLE CUSTOMIZATIONS
12.4 RELATED REPORTS
12.5 AUTHOR DETAILS
LIST OF TABLES (238 TABLES)
TABLE 1 GOVERNMENT FUNDING PLANS TO ENSURE CYBERSECURITY FOR CRITICAL INFRASTRUCTURE
TABLE 2 PORTER’S 5 FORCES IMPACT ON INDUSTRIAL CYBERSECURITY MARKET
TABLE 3 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR TOP THREE SECURITY TYPE (%)
TABLE 4 KEY BUYING CRITERIA FOR TOP 3 SECURITY TYPE
TABLE 5 INDUSTRIAL CYBERSECURITY MARKET: DETAILED LIST OF CONFERENCES AND EVENTS
TABLE 6 INDUSTRIAL CYBERSECURITY MARKET: ECOSYSTEM
TABLE 7 LIST OF FEW PATENTS IN INDUSTRIAL CYBERSECURITY MARKET, 2020–2021
TABLE 8 IMPORT DATA FOR SWITCHING AND ROUTING APPARATUS, HS CODE: 851769 (USD MILLION)
TABLE 9 EXPORT DATA FOR SWITCHING AND ROUTING APPARATUS, HS CODE: 851769 (USD MILLION)
TABLE 10 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 11 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 12 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 13 REST OF WORLD: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 14 ABB CYBER SECURITY SOLUTIONS DEPLOYED AT A U.S. WASTEWATER TREATMENT PLANT
TABLE 15 BOLIDEN (SWEDEN) USED ABB ABILITY CYBER SECURITY FINGERPRINT TO MITIGATE RISKS
TABLE 16 INDUSTRIAL CYBERSECURITY MARKET, BY SECURITY TYPE, 2018–2021 (USD BILLION)
TABLE 17 INDUSTRIAL CYBERSECURITY MARKET, BY SECURITY TYPE, 2022–2027 (USD BILLION)
TABLE 18 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY, BY REGION, 2018–2021 (USD MILLION)
TABLE 19 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY, BY REGION, 2022–2027 (USD MILLION)
TABLE 20 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN NORTH AMERICA, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 21 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 22 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 23 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 24 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN ASIA PACIFIC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 25 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN ASIA PACIFIC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 26 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 27 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 28 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 29 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORK SECURITY, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 30 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY, BY REGION, 2018–2021 (USD MILLION)
TABLE 31 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY, BY REGION, 2022–2027 (USD MILLION)
TABLE 32 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY IN NORTH AMERICA, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 33 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 34 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 35 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 36 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY IN ASIA PACIFIC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 37 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY IN ASIA PACIFIC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 38 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 39 INDUSTRIAL CYBERSECURITY MARKET FOR END-POINT SECURITY IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 40 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 41 INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 42 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY, BY REGION, 2018–2021 (USD MILLION)
TABLE 43 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY, BY REGION, 2022–2027 (USD MILLION)
TABLE 44 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN NORTH AMERICA, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 45 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 46 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 47 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 48 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN ASIA PACIFIC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 49 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN APAC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 50 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 51 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 52 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 53 INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 54 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY, BY REGION, 2018–2021 (USD MILLION)
TABLE 55 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY, BY REGION, 2022–2027 (USD MILLION)
TABLE 56 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN NORTH AMERICA, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 57 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 58 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 59 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 60 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN ASIA PACIFIC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 61 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN ASIA PACIFIC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 62 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 63 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 64 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 65 INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 66 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY, BY REGION, 2018–2021 (USD MILLION)
TABLE 67 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY, BY REGION, 2022–2027 (USD MILLION)
TABLE 68 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN NORTH AMERICA, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 69 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 70 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 71 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 72 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN ASIA PACIFIC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 73 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN ASIA PACIFIC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 74 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 75 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 76 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 77 INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 78 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS, BY REGION, 2018–2021 (USD MILLION)
TABLE 79 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS, BY REGION, 2022–2027 (USD MILLION)
TABLE 80 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN NORTH AMERICA, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 81 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 82 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 83 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 84 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN ASIA PACIFIC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 85 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN APAC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 86 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 87 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 88 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 89 INDUSTRIAL CYBERSECURITY MARKET FOR OTHERS, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 90 INDUSTRIAL CYBERSECURITY MARKET, BY OFFERING, 2018–2021 (USD BILLION)
TABLE 91 INDUSTRIAL CYBERSECURITY MARKET, BY OFFERING, 2022–2027 (USD BILLION)
TABLE 92 INDUSTRIAL CYBERSECURITY MARKET, BY PRODUCT, 2018–2021 (USD MILLION)
TABLE 93 INDUSTRIAL CYBERSECURITY MARKET, BY PRODUCT, 2022–2027 (USD MILLION)
TABLE 94 INDUSTRIAL CYBERSECURITY MARKET FOR GATEWAYS, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 95 INDUSTRIAL CYBERSECURITY MARKET FOR GATEWAYS, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 96 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORKING DEVICES, BY TYPE, 2018–2021 (THOUSAND UNITS)
TABLE 97 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORKING DEVICES, BY TYPE, 2022–2027 (THOUSAND UNITS)
TABLE 98 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORKING DEVICES, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 99 INDUSTRIAL CYBERSECURITY MARKET FOR NETWORKING DEVICES, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 100 INDUSTRIAL CYBERSECURITY MARKET, BY SOLUTIONS & SERVICES, 2018–2021 (USD BILLION)
TABLE 101 INDUSTRIAL CYBERSECURITY MARKET, BY SOLUTIONS & SERVICES, 2022–2027 (USD BILLION)
TABLE 102 INDUSTRIAL CYBERSECURITY MARKET FOR SOLUTIONS, BY TYPE, 2018–2021 (USD MILLION)
TABLE 103 INDUSTRIAL CYBERSECURITY MARKET FOR SOLUTIONS, BY TYPE, 2022–2027 (USD MILLION)
TABLE 104 INDUSTRIAL CYBERSECURITY MARKET FOR SOLUTIONS, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 105 INDUSTRIAL CYBERSECURITY MARKET FOR SOLUTIONS, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 106 INDUSTRIAL CYBERSECURITY MARKET FOR SERVICES, BY TYPE, 2018–2021 (USD MILLION)
TABLE 107 INDUSTRIAL CYBERSECURITY MARKET FOR SERVICES, BY TYPE, 2022–2027 (USD MILLION)
TABLE 108 INDUSTRIAL CYBERSECURITY MARKET FOR PROFESSIONAL SERVICES, BY TYPE, 2018–2021 (USD MILLION)
TABLE 109 INDUSTRIAL CYBERSECURITY MARKET FOR PROFESSIONAL SERVICES, BY TYPE, 2022–2027 (USD MILLION)
TABLE 110 INDUSTRIAL CYBERSECURITY MARKET FOR SERVICES, BY END-USER INDUSTRY, 2018–2021 (USD MILLION)
TABLE 111 INDUSTRIAL CYBERSECURITY MARKET FOR SERVICES, BY END-USER INDUSTRY, 2022–2027 (USD MILLION)
TABLE 112 INDUSTRIAL CYBERSECURITY MARKET, BY END-USER INDUSTRY, 2018–2021 (USD BILLION)
TABLE 113 INDUSTRIAL CYBERSECURITY MARKET, BY END-USER INDUSTRY, 2022–2027 (USD BILLION)
TABLE 114 INDUSTRIAL CYBERSECURITY MARKET FOR POWER INDUSTRY, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 115 INDUSTRIAL CYBERSECURITY MARKET FOR POWER INDUSTRY, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 116 INDUSTRIAL CYBERSECURITY MARKET FOR POWER INDUSTRY, BY PRODUCT, 2018–2021 (USD MILLION)
TABLE 117 INDUSTRIAL CYBERSECURITY MARKET FOR POWER INDUSTRY, BY PRODUCT, 2022–2027 (USD MILLION)
TABLE 118 INDUSTRIAL CYBERSECURITY MARKET FOR POWER INDUSTRY, BY SOLUTION AND SERVICE, 2018–2021 (USD MILLION)
TABLE 119 INDUSTRIAL CYBERSECURITY MARKET FOR POWER INDUSTRY, BY SOLUTION & SERVICE, 2022–2027 (USD MILLION)
TABLE 120 INDUSTRIAL CYBERSECURITY MARKET FOR UTILITIES INDUSTRY, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 121 INDUSTRIAL CYBERSECURITY MARKET FOR UTILITIES INDUSTRY, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 122 INDUSTRIAL CYBERSECURITY MARKET FOR UTILITIES INDUSTRY, BY PRODUCT, 2018–2021 (USD MILLION)
TABLE 123 INDUSTRIAL CYBERSECURITY MARKET FOR UTILITIES INDUSTRY, BY PRODUCT, 2022–2027 (USD MILLION)
TABLE 124 INDUSTRIAL CYBERSECURITY MARKET FOR UTILITIES INDUSTRY, BY SOLUTION AND SERVICE, 2018–2021 (USD MILLION)
TABLE 125 INDUSTRIAL CYBERSECURITY MARKET FOR UTILITIES INDUSTRY, BY SOLUTION & SERVICE, 2022–2027 (USD MILLION)
TABLE 126 INDUSTRIAL CYBERSECURITY MARKET FOR TRANSPORTATION INDUSTRY, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 127 INDUSTRIAL CYBERSECURITY MARKET FOR TRANSPORTATION INDUSTRY, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 128 INDUSTRIAL CYBERSECURITY MARKET FOR TRANSPORTATION INDUSTRY, BY PRODUCT, 2018–2021 (USD MILLION)
TABLE 129 INDUSTRIAL CYBERSECURITY MARKET FOR TRANSPORTATION INDUSTRY, BY PRODUCT, 2022–2027 (USD MILLION)
TABLE 130 INDUSTRIAL CYBERSECURITY MARKET FOR TRANSPORTATION INDUSTRY, BY SOLUTION AND SERVICE, 2018–2021 (USD MILLION)
TABLE 131 INDUSTRIAL CYBERSECURITY MARKET FOR TRANSPORTATION INDUSTRY, BY SOLUTION AND SERVICE, 2022–2027 (USD MILLION)
TABLE 132 INDUSTRIAL CYBERSECURITY MARKET FOR CHEMICALS AND MANUFACTURING INDUSTRY, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 133 INDUSTRIAL CYBERSECURITY MARKET FOR CHEMICALS AND MANUFACTURING INDUSTRY, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 134 INDUSTRIAL CYBERSECURITY MARKET FOR CHEMICALS AND MANUFACTURING INDUSTRY, BY PRODUCT, 2018–2021 (USD MILLION)
TABLE 135 INDUSTRIAL CYBERSECURITY MARKET FOR CHEMICALS AND MANUFACTURING INDUSTRY, BY PRODUCT, 2022–2027 (USD MILLION)
TABLE 136 INDUSTRIAL CYBERSECURITY MARKET FOR CHEMICALS AND MANUFACTURING INDUSTRY, BY SOLUTION AND SERVICE, 2018–2021 (USD MILLION)
TABLE 137 INDUSTRIAL CYBERSECURITY MARKET FOR CHEMICALS AND MANUFACTURING INDUSTRY, BY SOLUTION AND SERVICE, 2022–2027 (USD MILLION)
TABLE 138 INDUSTRIAL CYBERSECURITY MARKET FOR OTHER INDUSTRIES, BY OFFERING, 2018–2021 (USD MILLION)
TABLE 139 INDUSTRIAL CYBERSECURITY MARKET FOR OTHER INDUSTRIES, BY OFFERING, 2022–2027 (USD MILLION)
TABLE 140 INDUSTRIAL CYBERSECURITY MARKET FOR OTHER INDUSTRIES, BY PRODUCT, 2018–2021(USD MILLION)
TABLE 141 INDUSTRIAL CYBERSECURITY MARKET FOR OTHER INDUSTRIES, BY PRODUCT, 2022–2027 (USD MILLION)
TABLE 142 INDUSTRIAL CYBERSECURITY MARKET FOR OTHER INDUSTRIES, BY SOLUTION AND SERVICE, 2018–2021(USD MILLION)
TABLE 143 INDUSTRIAL CYBERSECURITY MARKET FOR OTHER INDUSTRIES, BY SOLUTION AND SERVICE, 2022–2027 (USD MILLION)
TABLE 144 INDUSTRIAL CYBERSECURITY MARKET, BY REGION, 2018–2021 (USD MILLION)
TABLE 145 INDUSTRIAL CYBERSECURITY MARKET, BY REGION, 2022–2027 (USD MILLION)
TABLE 146 INDUSTRIAL CYBERSECURITY MARKET IN NORTH AMERICA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 147 INDUSTRIAL CYBERSECURITY MARKET IN NORTH AMERICA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 148 INDUSTRIAL CYBERSECURITY MARKET IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 149 INDUSTRIAL CYBERSECURITY MARKET IN NORTH AMERICA, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 150 INDUSTRIAL CYBERSECURITY MARKET IN US, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 151 INDUSTRIAL CYBERSECURITY MARKET IN US, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 152 INDUSTRIAL CYBERSECURITY MARKET IN CANADA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 153 INDUSTRIAL CYBERSECURITY MARKET IN CANADA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 154 INDUSTRIAL CYBERSECURITY MARKET IN MEXICO, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 155 INDUSTRIAL CYBERSECURITY MARKET IN MEXICO, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 156 INDUSTRIAL CYBERSECURITY MARKET IN EUROPE, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 157 INDUSTRIAL CYBERSECURITY MARKET IN EUROPE, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 158 INDUSTRIAL CYBERSECURITY MARKET IN EUROPE, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 159 INDUSTRIAL CYBERSECURITY MARKET IN EUROPE, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 160 INDUSTRIAL CYBERSECURITY MARKET IN UK, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 161 INDUSTRIAL CYBERSECURITY MARKET IN UK, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 162 INDUSTRIAL CYBERSECURITY MARKET IN GERMANY, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 163 INDUSTRIAL CYBERSECURITY MARKET IN GERMANY, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 164 INDUSTRIAL CYBERSECURITY MARKET IN FRANCE, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 165 INDUSTRIAL CYBERSECURITY MARKET IN FRANCE, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 166 INDUSTRIAL CYBERSECURITY MARKET IN ITALY, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 167 INDUSTRIAL CYBERSECURITY MARKET IN ITALY, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 168 INDUSTRIAL CYBERSECURITY MARKET IN NETHERLANDS, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 169 INDUSTRIAL CYBERSECURITY MARKET IN NETHERLANDS, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 170 INDUSTRIAL CYBERSECURITY MARKET IN REST OF EUROPE, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 171 INDUSTRIAL CYBERSECURITY MARKET IN REST OF EUROPE, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 172 INDUSTRIAL CYBERSECURITY MARKET IN ASIA PACIFIC, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 173 INDUSTRIAL CYBERSECURITY MARKET IN ASIA PACIFIC, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 174 INDUSTRIAL CYBERSECURITY MARKET IN ASIA PACIFIC, BY COUNTRY, 2018–2021 (USD MILLION)
TABLE 175 INDUSTRIAL CYBERSECURITY MARKET IN ASIA PACIFIC, BY COUNTRY, 2022–2027 (USD MILLION)
TABLE 176 INDUSTRIAL CYBERSECURITY MARKET IN CHINA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 177 INDUSTRIAL CYBERSECURITY MARKET IN CHINA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 178 INDUSTRIAL CYBERSECURITY MARKET IN JAPAN, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 179 INDUSTRIAL CYBERSECURITY MARKET IN JAPAN, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 180 INDUSTRIAL CYBERSECURITY MARKET IN INDIA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 181 INDUSTRIAL CYBERSECURITY MARKET IN INDIA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 182 INDUSTRIAL CYBERSECURITY MARKET IN SOUTH KOREA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 183 INDUSTRIAL CYBERSECURITY MARKET IN SOUTH KOREA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 184 INDUSTRIAL CYBERSECURITY MARKET IN REST OF ASIA PACIFIC, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 185 INDUSTRIAL CYBERSECURITY MARKET IN REST OF ASIA PACIFIC, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 186 INDUSTRIAL CYBERSECURITY MARKET IN ROW, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 187 INDUSTRIAL CYBERSECURITY MARKET IN ROW, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 188 INDUSTRIAL CYBERSECURITY MARKET IN ROW, BY REGION, 2018–2021 (USD MILLION)
TABLE 189 INDUSTRIAL CYBERSECURITY MARKET IN ROW, BY REGION, 2022–2027 (USD MILLION)
TABLE 190 INDUSTRIAL CYBERSECURITY MARKET IN MEA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 191 INDUSTRIAL CYBERSECURITY MARKET IN MEA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 192 INDUSTRIAL CYBERSECURITY MARKET IN SOUTH AMERICA, BY SECURITY TYPE, 2018–2021 (USD MILLION)
TABLE 193 INDUSTRIAL CYBERSECURITY MARKET IN SOUTH AMERICA, BY SECURITY TYPE, 2022–2027 (USD MILLION)
TABLE 194 INDUSTRAIL CYBERSECURITY MARKET: DEGREE OF COMPETITION
TABLE 195 INDUSTRIAL CYBERSECURITY MARKET: DETAILED LIST OF KEY STARTUP/SMES
TABLE 196 INDUSTRIAL CYBERSECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY PLAYERS [STARTUPS/SMES]
TABLE 197 INDUSTRIAL CYBERSECURITY MARKET: PRODUCT LAUNCHES AND DEVELOPMENTS, AUGUST 2018 AND JANUARY 2022
TABLE 198 INDUSTRIAL CYBERSECURITY MARKET: DEALS, AUGUST 2018 AND JANUARY 2022
TABLE 199 IBM CORPORATION: BUSINESS OVERVIEW
TABLE 200 IBM CORPORATION: PRODUCTS AND SOLUTIONS OFFERED
TABLE 201 IBM CORPORATION: SERVICES OFFERED
TABLE 202 IBM CORPORATION: PRODUCT LAUNCHES
TABLE 203 IBM CORPORATION: DEALS
TABLE 204 IBM CORPORATION: OTHERS
TABLE 205 HONEYWELL INTERNATIONAL INC.: BUSINESS OVERVIEW
TABLE 206 HONEYWELL INTERNATIONAL INC.: PRODUCTS OFFERED
TABLE 207 HONEYWELL INTERNATIONAL INC.: SOLUTIONS OFFERED
TABLE 208 HONEYWELL INTERNATIONAL INC.: SERVICES OFFERED
TABLE 209 HONEYWELL INTERNATIONAL INC.: PRODUCT LAUNCHES
TABLE 210 HONEYWELL INTERNATIONAL INC.: DEALS
TABLE 211 ABB LTD.: BUSINESS OVERVIEW
TABLE 212 ABB LTD.: PRODUCTS OFFERED
TABLE 213 ABB LTD.: PRODUCT LAUNCHES
TABLE 214 ABB LTD.: DEALS
TABLE 215 CISCO SYSTEMS, INC.: BUSINESS OVERVIEW
TABLE 216 CISCO SYSTEMS, INC.: PRODUCTS OFFERED
TABLE 217 CISCO SYSTEMS, INC.: SERVICES OFFERED
TABLE 218 CISCO SYSTEMS, INC.: PRODUCT LAUNCHES
TABLE 219 CISCO SYSTEMS, INC.: DEALS
TABLE 220 SCHNEIDER ELECTRIC: BUSINESS OVERVIEW
TABLE 221 SCHNEIDER ELECTRIC: PRODUCTS OFFERED
TABLE 222 SCHNEIDER ELECTRIC: DEALS
TABLE 223 MCAFEE CORPORATION: BUSINESS OVERVIEW
TABLE 224 MCAFEE CORPORATION: PRODUCTS OFFERED
TABLE 225 MCAFEE CORPORATION: PRODUCT LAUNCHES
TABLE 226 MCAFEE CORPORATION: DEALS
TABLE 227 SIEMENS: BUSINESS OVERVIEW
TABLE 228 SIEMENS: PRODUCTS OFFERED
TABLE 229 SIEMENS: DEALS
TABLE 230 DELL TECHNOLOGIES INC.: BUSINESS OVERVIEW
TABLE 231 DELL TECHNOLOGIES INC.: PRODUCTS OFFERED
TABLE 232 DELL TECHNOLOGIES INC.: DEALS
TABLE 233 NORTONLIFELOCK INC.: BUSINESS OVERVIEW
TABLE 234 NORTONLIFELOCK INC.: PRODUCTS OFFERED
TABLE 235 NORTONLIFELOCK INC.: DEALS
TABLE 236 ROCKWELL AUTOMATION INC.: BUSINESS OVERVIEW
TABLE 237 ROCKWELL AUTOMATION INC.: PRODUCTS OFFERED
TABLE 238 ROCKWELL AUTOMATION INC.: DEALS
LIST OF FIGURES (77 FIGURES)
FIGURE 1 INDUSTRIAL CYBERSECURITY MARKET SEGMENTATION
FIGURE 2 INDUSTRIAL CYBERSECURITY MARKET: RESEARCH DESIGN
FIGURE 3 MARKET SIZE ESTIMATION METHODOLOGY: BOTTOM-UP APPROACH
FIGURE 4 MARKET SIZE ESTIMATION METHODOLOGY: TOP-DOWN APPROACH
FIGURE 5 MARKET SIZE ESTIMATION: SUPPLY-SIDE ANALYSIS
FIGURE 6 DATA TRIANGULATION
FIGURE 7 DEMAND FOR INDUSTRIAL CYBERSECURITY PRODUCTS AND SERVICES TO GROW AT SIGNIFICANT RATE DURING FORECAST PERIOD
FIGURE 8 INDUSTRIAL CYBERSECURITY MARKET FOR PRODUCTS TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
FIGURE 9 NETWORK SECURITY SEGMENT TO HOLD LARGEST SHARE OF INDUSTRIAL CYBERSECURITY MARKET IN 2022
FIGURE 10 POWER INDUSTRY TO ACCOUNT FOR LARGEST SIZE OF INDUSTRIAL CYBERSECURITY MARKET IN 2027
FIGURE 11 INDUSTRIAL CYBERSECURITY MARKET, BY REGION, 2021
FIGURE 12 INCREASING GOVERNMENT EXPENDITURE TO ENSURE CYBERSECURITY AND GROWING FOCUS ON INTEGRATING SMART TECHNOLOGIES IN INDUSTRIAL SECURITY SYSTEMS TO DRIVE MARKET GROWTH DURING FORECAST PERIOD
FIGURE 13 POWER INDUSTRY TO ACCOUNT FOR LARGEST SHARE OF GLOBAL INDUSTRIAL CYBERSECURITY MARKET IN 2022
FIGURE 14 SOLUTIONS & SERVICES SEGMENT TO CAPTURE LARGER SHARE OF INDUSTRIAL CYBERSECURITY MARKET IN 2022
FIGURE 15 NETWORK SECURITY SEGMENT TO CAPTURE LARGEST SHARE OF INDUSTRIAL CYBERSECURITY MARKET IN 2022
FIGURE 16 NORTH AMERICA HELD LARGEST SHARE OF INDUSTRIAL CYBERSECURITY MARKET IN 2021
FIGURE 17 INDUSTRIAL CYBERSECURITY MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
FIGURE 18 INDUSTRIAL CYBERSECURITY MARKET DRIVERS AND THEIR IMPACT
FIGURE 19 HISTORY OF CYBERATTACKS ON DIFFERENT INFRASTRUCTURES
FIGURE 20 NUMBER OF CYBER ATTACKS, 2018-2021
FIGURE 21 PROMINENT CYBERATTACK TYPES IN 2021
FIGURE 22 GLOBAL IOT CONNECTIONS, 2018–2027 (BILLION UNITS)
FIGURE 23 INDUSTRIAL CYBERSECURITY MARKET RESTRAINTS AND THEIR IMPACT
FIGURE 24 INDUSTRIAL CYBERSECURITY MARKET OPPORTUNITIES AND THEIR IMPACT
FIGURE 25 INDUSTRIAL CYBERSECURITY MARKET CHALLENGES AND THEIR IMPACT
FIGURE 26 PROMINENT ATTACKS ON ICS NETWORK
FIGURE 27 INDUSTRIAL ROUTERS: AVERAGE SELLING PRICE
FIGURE 28 INDUSTRIAL CYBERSECURITY: PORTER’S FIVE FORCES ANALYSIS
FIGURE 29 PORTER’S FIVE FORCES ANALYSIS: INDUSTRIAL CYBERSECURITY MARKET
FIGURE 30 KEY BUYING CRITERIA FOR TOP THREE SECURITY TYPE
FIGURE 31 NUMBER OF PATENTS GRANTED FOR INDUSTRIAL CYBERSECURITY, 2011–2021
FIGURE 32 REGIONAL ANALYSIS OF PATENTS GRANTED FOR INDUSTRIAL CYBERSECURITY EQUIPMENT, 2011–2021
FIGURE 33 SWITCHING AND ROUTING APPARATUS, IMPORT VALUES FOR MAJOR COUNTRIES, 2016–2020
FIGURE 34 SWITCHING AND ROUTING APPARATUS, EXPORT VALUES FOR MAJOR COUNTRIES, 2016–2020
FIGURE 35 REVENUE SHIFT FOR INDUSTRIAL CYBERSECURITY MARKET
FIGURE 36 INDUSTRIAL CYBERSECURITY MARKET, BY SECURITY TYPE
FIGURE 37 ASIA PACIFIC TO RECORD HIGHEST CAGR IN MARKET FOR NETWORK SECURITY DURING FORECAST PERIOD
FIGURE 38 NORTH AMERICA TO HOLD LARGEST MARKET SHARE OF INDUSTRIAL CYBERSECURITY MARKET FOR ENDPOINT SECURITY DURING FORECAST PERIOD
FIGURE 39 ASIA PACIFIC TO LEAD INDUSTRIAL CYBERSECURITY MARKET FOR APPLICATION SECURITY DURING FORECAST PERIOD
FIGURE 40 ASIA PACIFIC TO DOMINATE INDUSTRIAL CYBERSECURITY MARKET FOR CLOUD SECURITY DURING FORECAST PERIOD
FIGURE 41 ASIA PACIFIC TO COMMAND INDUSTRIAL CYBERSECURITY MARKET FOR WIRELESS SECURITY DURING FORECAST PERIOD
FIGURE 42 NORTH AMERICA TO WITNESS LARGEST SHARE OF INDUSTRIAL CYBERSECURITY MARKET FOR OTHER SECURITY TYPES DURING FORECAST PERIOD
FIGURE 43 INDUSTRIAL CYBERSECURITY MARKET, BY OFFERING
FIGURE 44 PRODUCTS SEGMENT TO EXHIBIT HIGHER CAGR IN INDUSTRIAL CYBERSECURITY MARKET, BY OFFERING, DURING FORECAST PERIOD
FIGURE 45 GATEWAYS TO DOMINATE INDUSTRIAL CYBERSECURITY MARKET FOR PRODUCTS SEGMENT DURING FORECAST PERIOD
FIGURE 46 POWER INDUSTRY HELD LARGEST SHARE OF INDUSTRIAL CYBERSECURITY MARKET FOR GATEWAYS IN 2021
FIGURE 47 INDUSTRIAL ETHERNET SWITCHES TO COMMAND INDUSTRIAL CYBERSECURITY MARKET FOR NETWORKING DEVICES THROUGHOUT FORECAST PERIOD
FIGURE 48 INDUSTRIAL CYBERSECURITY MARKET FOR SOLUTIONS SEGMENT TO GROW AT HIGHER CAGR THAN SERVICES SEGMENT DURING FORECAST PERIOD
FIGURE 49 POWER INDUSTRY CAPTURED LARGEST SHARE OF INDUSTRIAL CYBERSECURITY MARKET FOR SOLUTIONS IN 2021
FIGURE 50 PROFESSIONAL SERVICES ACCOUNTED FOR LARGER SHARE OF THAN MANAGED SERVICES IN 2021
FIGURE 51 RISK MANAGEMENT SERVICES TO REGISTER HIGHEST CAGR IN INDUSTRIAL CYBERSECURITY MARKET DURING FORECAST PERIOD
FIGURE 52 INDUSTRIAL CYBERSECURITY MARKET, BY END-USER INDUSTRY
FIGURE 53 TRANSPORTATION INDUSTRY TO EXHIBIT HIGHEST CAGR IN INDUSTRIAL CYBERSECURITY MARKET DURING FORECAST PERIOD
FIGURE 54 SOLUTIONS & SERVICES TO HOLD LARGEST SHARE OF INDUSTRIAL CYBERSECURITY MARKET FOR POWER INDUSTRY DURING FORECAST PERIOD
FIGURE 55 PRODUCT OFFERINGS TO RECORD HIGHER CAGR IN INDUSTRIAL CYBERSECURITY MARKET FOR UTILITIES INDUSTRY DURING FORECAST PERIOD
FIGURE 56 PRODUCTS SEGMENT TO WITNESS HIGHER CAGR IN INDUSTRIAL CYBERSECURITY MARKET FORTRANSPORTATION INDUSTRY DURING FORECAST PERIOD
FIGURE 57 SOLUTIONS & SERVICES SEGMENT TO HOLD LARGER SHARE OF INDUSTRIAL CYBERSECURITY MARKET FOR CHEMICALS AND MANUFACTURING INDUSTRY DURING FORECAST PERIOD
FIGURE 58 SOLUTIONS & SERVICES SEGMENT TO CAPTURE LARGER MARKET SHARE FOR OTHER INDUSTRIES DURING FORECAST PERIOD
FIGURE 59 INDUSTRIAL CYBERSECURITY MARKET IN ASIA PACIFIC TO GROW AT HIGHEST CAGR FROM 2022 TO 2027
FIGURE 60 SNAPSHOT OF INDUSTRIAL CYBERSECURITY MARKET IN NORTH AMERICA
FIGURE 61 SNAPSHOT OF INDUSTRIAL CYBERSECURITY MARKET IN EUROPE
FIGURE 62 SNAPSHOT OF INDUSTRIAL CYBERSECURITY MARKET IN ASIA PACIFIC
FIGURE 63 SNAPSHOT OF INDUSTRIAL CYBERSECURITY MARKET IN ROW
FIGURE 64 INDUSTRIAL CYBERSECURITY MARKET: MARKET SHARE ANALYSIS
FIGURE 65 REVENUE ANALYSIS OF KEY COMPANIES IN PAST FIVE YEARS
FIGURE 66 INDUSTRIAL CYBERSECURITY MARKET (GLOBAL) COMPANY EVALUATION MATRIX, 2021
FIGURE 67 STARTUP/SME EVALUATION MATRIX
FIGURE 68 IBM CORPORATION: COMPANY SNAPSHOT
FIGURE 69 HONEYWELL INTERNATIONAL INC.: COMPANY SNAPSHOT
FIGURE 70 ABB LTD.: COMPANY SNAPSHOT
FIGURE 71 CISCO SYSTEMS, INC.: COMPANY SNAPSHOT
FIGURE 72 SCHNEIDER ELECTRIC: COMPANY SNAPSHOT
FIGURE 73 MCAFEE CORPORATION: COMPANY SNAPSHOT
FIGURE 74 SIEMENS: COMPANY SNAPSHOT
FIGURE 75 DELL TECHNOLOGIES INC.: COMPANY SNAPSHOT
FIGURE 76 NORTONLIFELOCK INC.: COMPANY SNAPSHOT
FIGURE 77 ROCKWELL AUTOMATION INC.: COMPANY SNAPSHOT
The study involved 4 major activities in estimating the current size of industrial cybersecurity market. Exhaustive secondary research has been conducted to collect information about the market, the peer market, and the parent market. Validating findings, assumptions, and sizing with industry experts across the value chain through primary research has been the next step. Both top-down and bottom-up approaches have been employed to estimate the complete market size. After that, market breakdown and data triangulation methods have been used to estimate the market size of segments and subsegments.
Secondary Research
The research methodology used to estimate and forecast the industrial cybersecurity market begins with capturing the data on revenues of the key vendors in the market through secondary research. This study involves the use of extensive secondary sources, directories, and databases, such as Hoovers, Bloomberg Businessweek, Factiva, and OneSource, to identify and collect information useful for the technical and commercial study of the industrial cybersecurity market. Secondary sources also include annual reports, press releases, and investor presentations of companies; white papers, certified publications, and articles from recognized authors; directories; and databases. Secondary research has been mainly done to obtain key information about the industry’s supply chain, market’s value chain, total pool of key players, market classification and segmentation according to industry trends, geographic markets, and key developments from both market- and technology oriented perspectives.
Primary Research
In the primary research process, various primary sources from both supply and demand sides were interviewed to obtain the qualitative and quantitative information relevant to the industrial cybersecurity vision market. Primary sources from the supply side include experts such as CEOs, vice presidents, marketing directors, technology and innovation directors, application developers, application users, and related executives from various key companies and organizations operating in the ecosystem of the AI in computer vision market.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Both top-down and bottom-up approaches have been used to estimate and validate the overall size of the industrial cybersecurity market. These methods have also been used extensively to estimate the size of various market subsegments. The research methodology used to estimate the market size includes the following:
- Key players in major applications and markets have been identified through extensive secondary research.
- The industry’s supply chain and market size, in terms of value, have been determined through primary and secondary research processes.
- All percentage shares, splits, and breakdowns have been determined using secondary sources and verified through primary sources.
Data Triangulation
After arriving at the overall market size using the estimation processes as explained above, the market was split into several segments and subsegments. To complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, data triangulation, and market breakdown procedures have been employed, wherever applicable. The data have been triangulated by studying various factors and trends from both the demand and supply sides.
Report Objectives
- To define, describe, and forecast the industrial cybersecurity market on the basis of offering, temperature type, Logistic, application, and region.
- To forecast the size of the market segments for four major regions—North America, Europe, Asia Pacific (APAC), and Rest of the World (RoW)
- To provide detailed information regarding the major factors influencing the growth of the market (drivers, restraints, opportunities, and industry-specific challenges)
- To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and contributions to the total market
- To study the complete value chain and allied industry segments and perform a value chain analysis of the market
- To strategically profile key players and comprehensively analyze their market shares and core competencies2
- To analyze the opportunities in the market for stakeholders and describe the competitive landscape of the market
- To analyze competitive developments such as joint ventures, collaborations, agreements, contracts, partnerships, mergers & acquisitions, new product developments, and research & development (R&D) in the market
- To analyze the impact of COVID-19 on the industrial cybersecurity market and provide market estimates for both pre- and post-COVID-19 scenarios
Available Customizations
With the given market data, MarketsandMarkets offers customizations according to the company’s specific needs. The following customization options are available for the report:
Company Information
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...







Growth opportunities and latent adjacency in Industrial Cybersecurity Market